You need to map the external domain (https://externallink.company.com) to your app service.
signin-oidc Attemps to Call Internal FQDN
We have an ASP.NET Core application that uses the OpenId Connect authentication protocol. In Azure AD B2C we setup the external FQDN (domain alias) (https://externallink.company.com) as the redirect URI. What we noticed is that after redirecting to https://externallink.company.com/signin-oidc it then redirects to the internal FQDN https://internallink.company.com/signin-oidc which is the URL of the App Service in Azure. The internal link is not accessible outside the company's network and should stay that way.
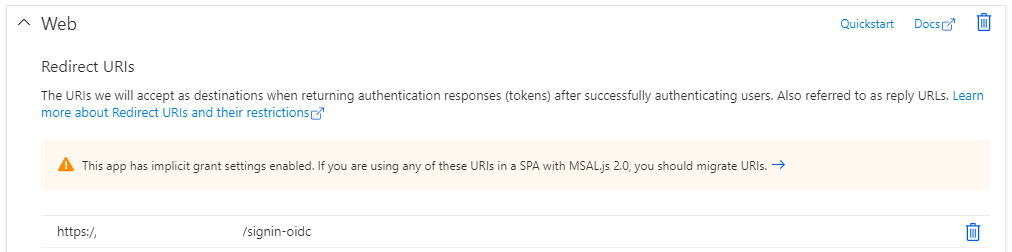
The error that we got is this:
redirect_uri_mismatch&error_description=AADB2C90006: The redirect URI 'https://internallink.company.com/signin-oidc' provided in the request is not registered for the client id 'xxxxxxx-xxxx-xxxx-xxxx-xxxxxxx'.%0D%0ACorrelation ID
This is how we have setup the authentication in the Startup class.
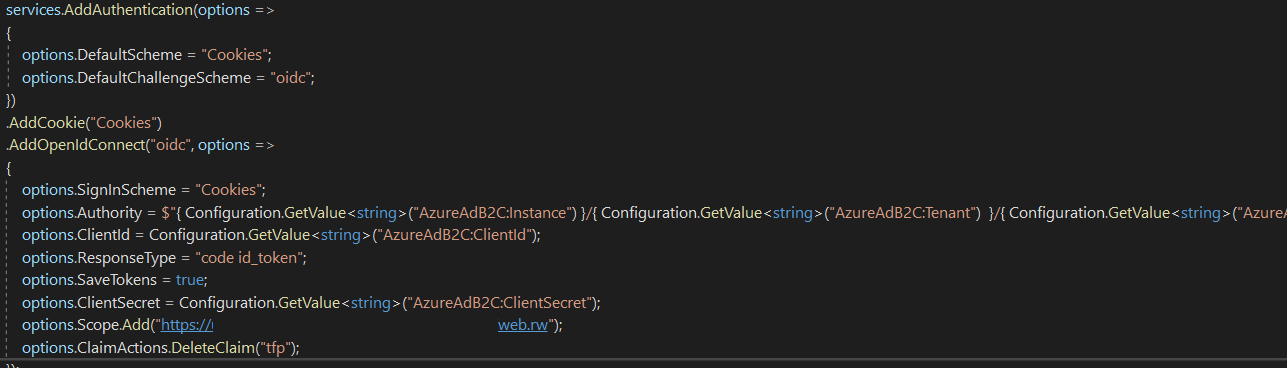
Should I specifically put the Callback path so that OpenId does not attempt to call the internal FQDN?
Update:
If I try to add the internal FQDN in the list of redirect URIs I will be able to sign in but afterwards I will get this error (URL is https://internallink.company.com/signin-oidc). This is expected because as I've mentioned the internal URL cannot be accessed via the public internet.
Microsoft Security | Microsoft Entra | Microsoft Entra External ID
1 answer
Sort by: Most helpful
-
 Alfredo Revilla - Upwork Top Talent | IAM SWE SWA 27,526 Reputation points Moderator
Alfredo Revilla - Upwork Top Talent | IAM SWE SWA 27,526 Reputation points Moderator2020-08-06T07:10:08.827+00:00