@Natoshi Sakamato Thanks for reaching out and apologies for the delay on this.
You should be able to generate the incidents on basis of whatever logs you have inflowing.
For that you need to create the Scheduled Query Rule (as default MS incident creation rule only check for MS related security products like Azure Defender, Cloud app security etc).
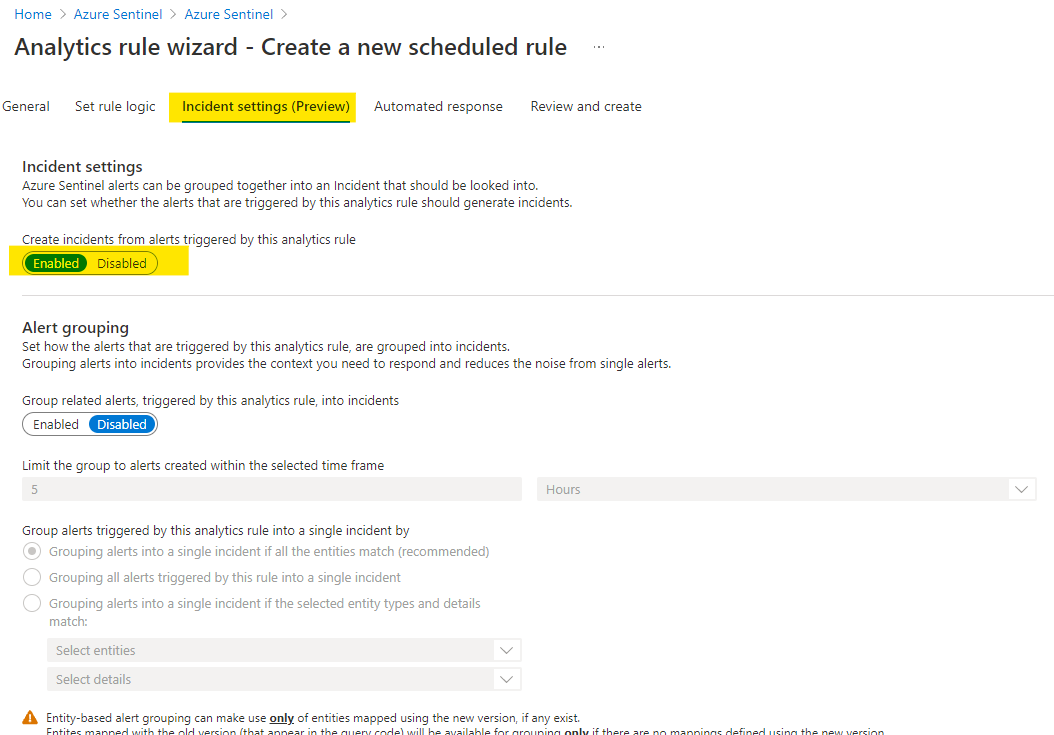
Once you are into the process of creating it and have specified the query , on 3rd segment you have the option to generate Incidents on basis of this Scheduled query rule.
Let me know if you have done this already and still having issue.
-----------------------------------------------------------------------------------------------------------------
Please remember to "Accept Answer" if any answer/reply helped, so that others in the community facing similar issues can easily find the solution.