Hello @Tom Bulsink | Inspiro , This is really a great question on DPS and IoT Hub best practices. The majority covers very broad areas! I tried my best to put it in a simple way to reduce reading confusion.
When a device connects to DPS, will it be registered to a hub if the intermediate certificate is removed, but the root certificate is still present and valid?
When a device connects to DPS, will it be registered to a hub if the intermediate certificate has expired but the root certificate is still valid?
When a device connects to DPS, will it be registered to a hub if the intermediate certificate is valid but the root certificate has expired?
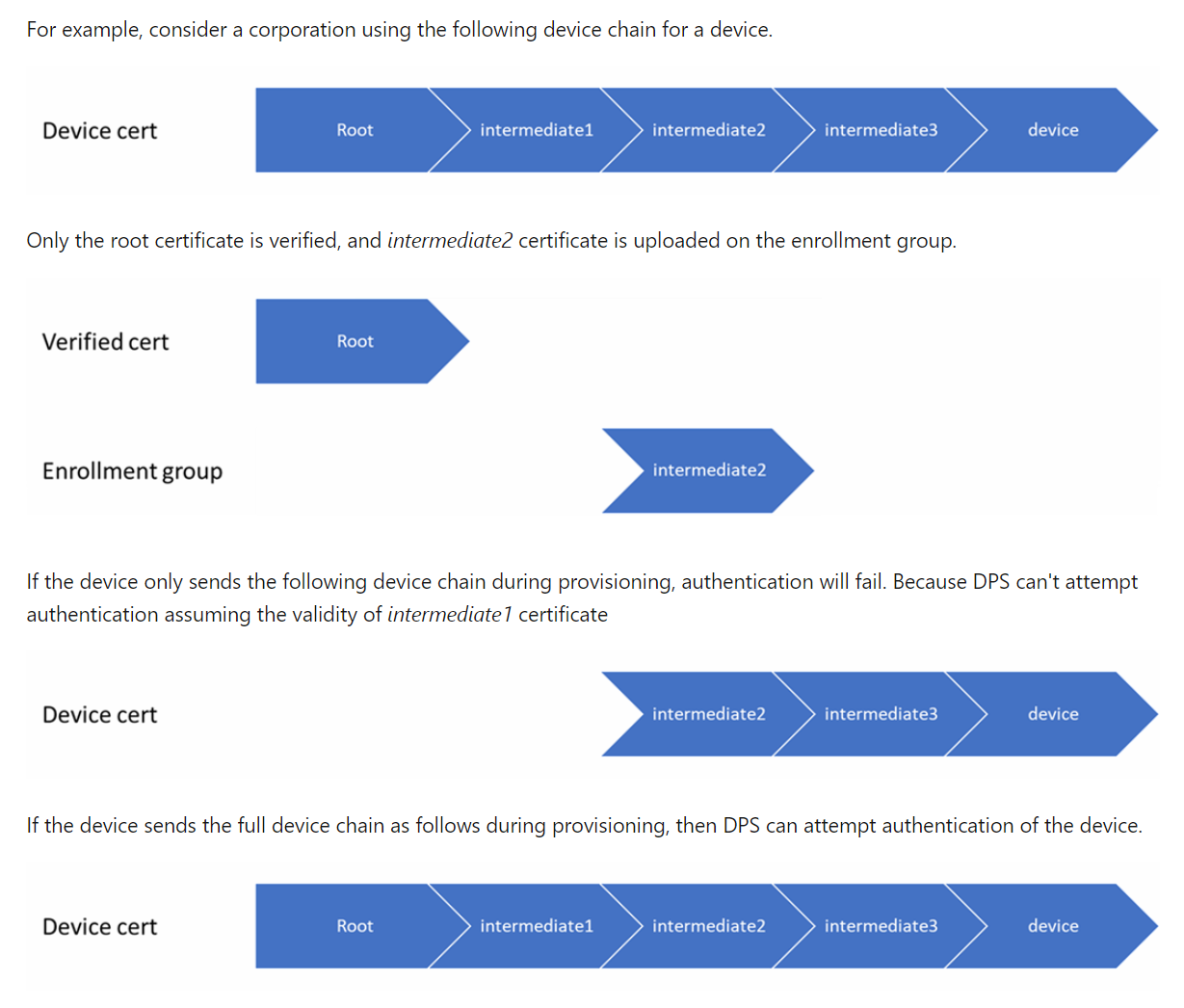
Please see this documentation for an example: DPS device chain requirements
Be aware, though, that, if you delete the enrollment group and there is an enabled enrollment group for a signing certificate higher up in the certificate chain of one or more of the devices, those devices can re-enroll. More info: Enrollment groups||How to deprovision devices that were previously auto-provisioned
To disallow DPS access in a group certificate setup, one would create an individual device registration using the device certificate and then disable that device. However, in such a setup the device certificate might not be available as that is generated with the intermediate certificate. How does one create this individual device registration in this case?
You may be interested to read this document: Disallow specific devices in an enrollment group
Is the device certificate actually used as TLS client authentication or is device authentication something built on top of of TLS?
This document talks about the DPS and TLS support: TLS support in Azure IoT Hub Device Provisioning Service (DPS)
What are the recommended validity periods of CA, intermediate/group and device certificates in DPS/IoT hub?
The frequency in which you roll your certificates will depend on the security needs of your solution. Customers with solutions involving highly sensitive data may roll certificate(s) daily, while others roll their certificates every couple of years. Please see this document on How to roll X.509 device certificates
What is the recommended strategy regarding device certificates if devices could be offline for longer (5 years and more perhaps) periods of time in which there might be no way of updating (client) certificates?
Please see this document : Understand extended offline capabilities for IoT Edge devices, modules, and child devices, for the certificate management, again it depends on the security needs of your solution.
Please comment in the below section if you need any further help in this matter, happy to help.
If the response is helpful, please click "Accept Answer" and upvote it.