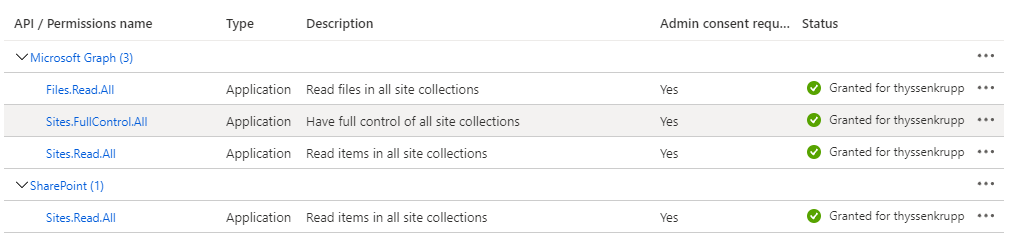
Hi @Joanna Łęgowska ,
Per my test, this issue might not involve permission. Since Azure app is different with sharepoint app. Azure app is unable to use client secret to connect sharepoint. Certificate file is necessary. We need to login with following cmdlet :
Connect-PnPOnline -ClientId <$application client id as copied over from the AAD app registration above> -CertificatePath '<$path to the PFX file generated by the PowerShell script above>' -CertificatePassword (ConvertTo-SecureString -AsPlainText "<$password assigned to the generated certificate pair above>" -Force) -Url https://<$yourtenant>.sharepoint.com -Tenant "<$tenantname>.onmicrosoft.com"
Per my test, 'Site.Read.All' is enough for GetPnPList .
If you want to use Azure app you can refer to the following link:
https://learn.microsoft.com/en-us/sharepoint/dev/solution-guidance/security-apponly-azuread
If you want to use sharepoint app , please refer to the following link:
https://learn.microsoft.com/en-us/sharepoint/dev/solution-guidance/security-apponly-azureacs
If the answer is helpful, please click "Accept Answer" and kindly upvote it. If you have extra questions about this answer, please click "Comment".
Note: Please follow the steps in our documentation to enable e-mail notifications if you want to receive the related email notification for this thread.