
Hi, dear @AD Dev
Your idea is a bit complicated, this is actually a very simple process. When you use the admin consent URL to log in to the administrator of the target tenant, it will still ask the administrator to consent to the MS graph permissions granted to the multi-tenant application in the original tenant. When the administrator of the target tenant consent, the multi-tenant application will be added to the target tenant as an enterprise application and have the permissions granted to it in the original tenant.
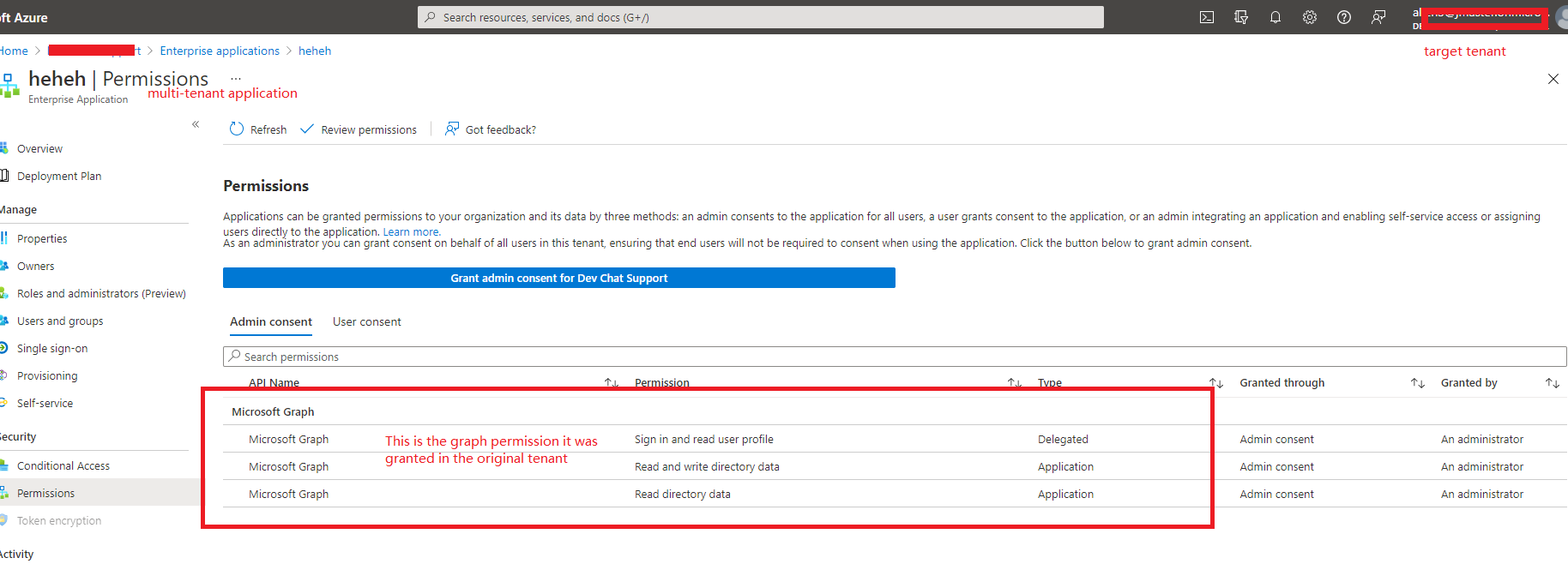
So I think you don't need to bind users to the target tenant for collaboration, because you are using the client credential flow and there is no user login involved. Next, you only need to use the client credential flow to obtain a token according to the normal process to access the resources of the target tenant.
If the answer is helpful, please click "Accept Answer" and kindly upvote it. If you have extra questions about this answer, please click "Comment".
Note: Please follow the steps in our documentation to enable e-mail notifications if you want to receive the related email notification for this thread.
