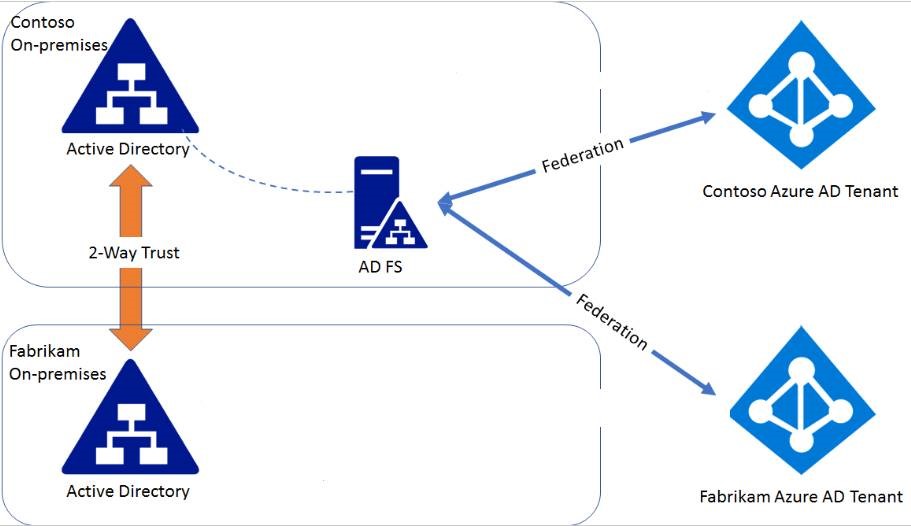
First of all, I'd like to make clear that ADFS is not a requirement to have SSO with Azure AD workloads (eg. Office 365). You can use Azure Active Directory Seamless Single Sign-On and even other options for Windows 10.
When you are using Form Based Authentication, the user is doing an explicit credential logon. Meaning that the password is sent to the ADFS server for logon but not the domain controller. From the ADFS server, the service asks for a Kerberos ticket for the user. So the Windows logon really starts from the ADFS server. As a result, if you look at the DC's logs, the Kerberos ticket request events will show the IP address of the ADFS server, and if the password is wrong and the account has to be locked out, the source workstation will show the ADFS server name.
ADFS is making LDAP calls (not to authenticate the user, but to enrich the token depending on your claim issuance rules). If the user is from a different domain, the ADFS service still need to do LDAP queries to this domain. The service also uses the Kerberos S4ULogin feature (Service for User to Self) to check group membership and build tokens.