Hi @MD89 ,
What error do you see in the Event Viewer? I'll be able to help diagnose much more accurately if I have this.
If you are getting a username/password error, you can update the passwords and make sure everything in the integration guide has been configured as described. https://learn.microsoft.com/en-us/azure/active-directory/saas-apps/cisco-anyconnect#:~:text=When%20you%20integrate%20Cisco%20AnyConnect%20with%20Azure%20AD%2C,in%20one%20central%20location%20-%20the%20Azure%20portal.
Then, make sure you have added the users to the Cisco Any connect App in the Azure portal.
Then, restart the services and the server.
I'm providing a pretty long list of additional possibilities so apologies in advance if you have tried some of these. The DLL error can happen any of the following reasons (among others):
1) The user for which NPS rejects the requests have unicode characters in their passwords. The NPS does not support Unicode passwords and it can fail for that reason. You can change the user's password to resolve this. (This could be the case if this is failing for some users and not others, but likely not the case if the users can login sometimes and not others as you described.)
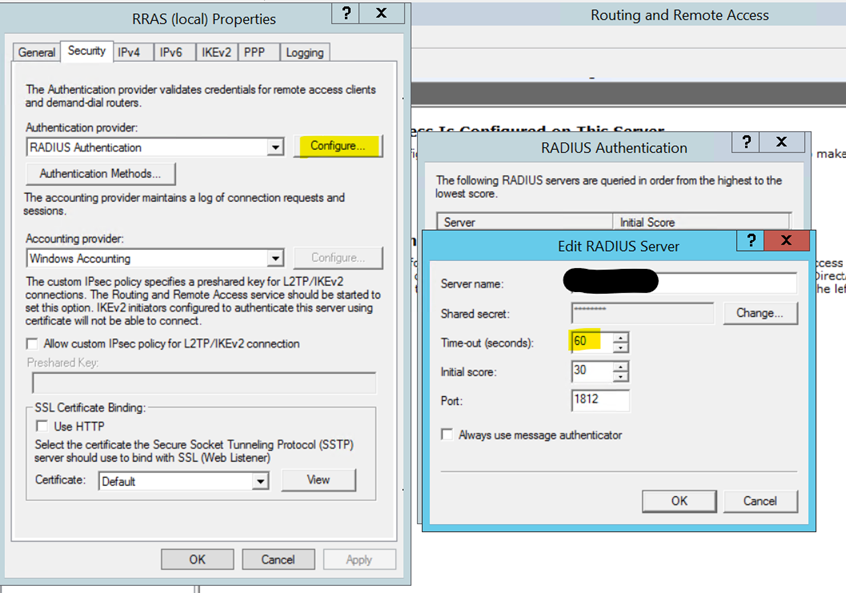
2) Timeout observed within any firewall that you may have within your network.
3) During my own setup of this extension I have received this error when the request was timing out too soon, when the latest version of the extension was not installed, and when there were old certificates on the server that needed to be removed.
If the request is timing out too soon, make sure that it's set to at least 60 seconds to give enough time for the request to succeed.
4) Make sure also you have the latest version of the extension installed, as well as all Windows updates. Older versions sometimes threw that DLL error. https://learn.microsoft.com/en-us/azure/active-directory/authentication/howto-mfa-nps-extension-rdg#install-the-nps-extension
5) Make sure that there aren't any duplicate or old certificates on the server.
You can check for old certificates using:
Get-MsolServicePrincipalCredential -AppPrincipalId "app-principal-id" -ReturnKeyValues 1
Then you can remove duplicates using:
Remove-MsolServicePrincipalCredential -AppPrincipalId "app-principal-id" -KeyIds <enterkeyidhere>
6) The connection method is not allowed by network policy
7) NPS does not have access to the user account database on the domain controller.
8) There is an issue with the primary authentication. Check the NPS logs and authentication requests related to any of the users receiving the error.
9)
The NPS server must be able to communicate with the specified URLs: https://learn.microsoft.com/en-us/azure/active-directory/authentication/howto-mfa-nps-extension#network-requirements
If you provide me with the event viewer information and any additional logs, I'll be happy to help diagnose this further.