Issue:
When I tried to reset password from Azure portal for test user, I keep getting the following error.
"Unfortunately, you cannot reset this user's password because your on-premises policy does not allow it. Please review your on-premises policy to ensure that it is setup correctly."
When I do it from https://passwordreset.microsoftonline.com
I get similar error.
Event 6329 & 33008
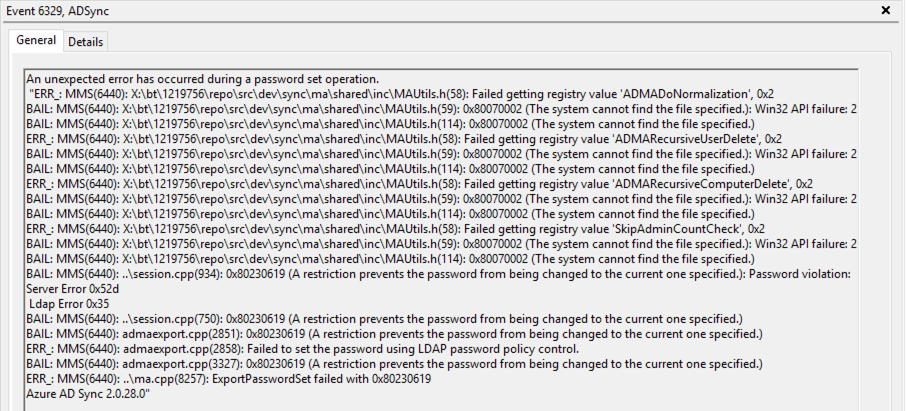
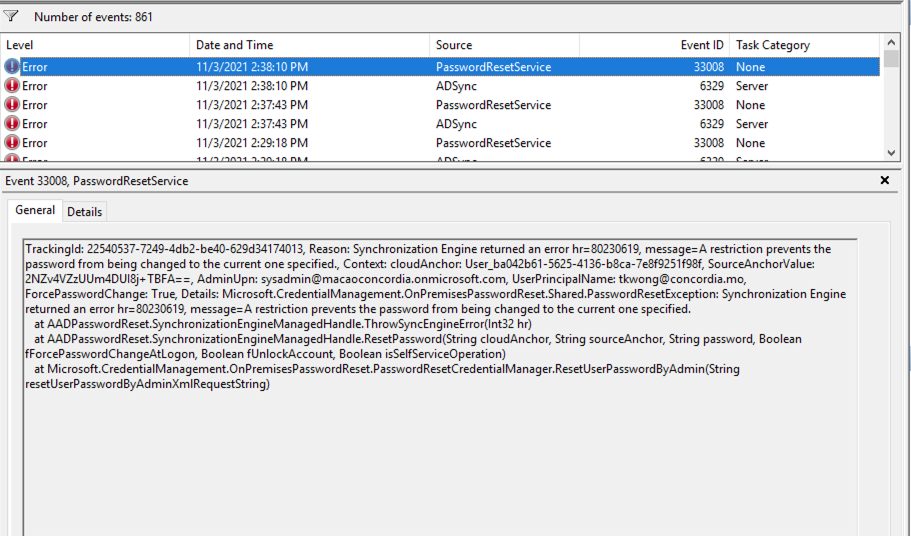
background:
--------------
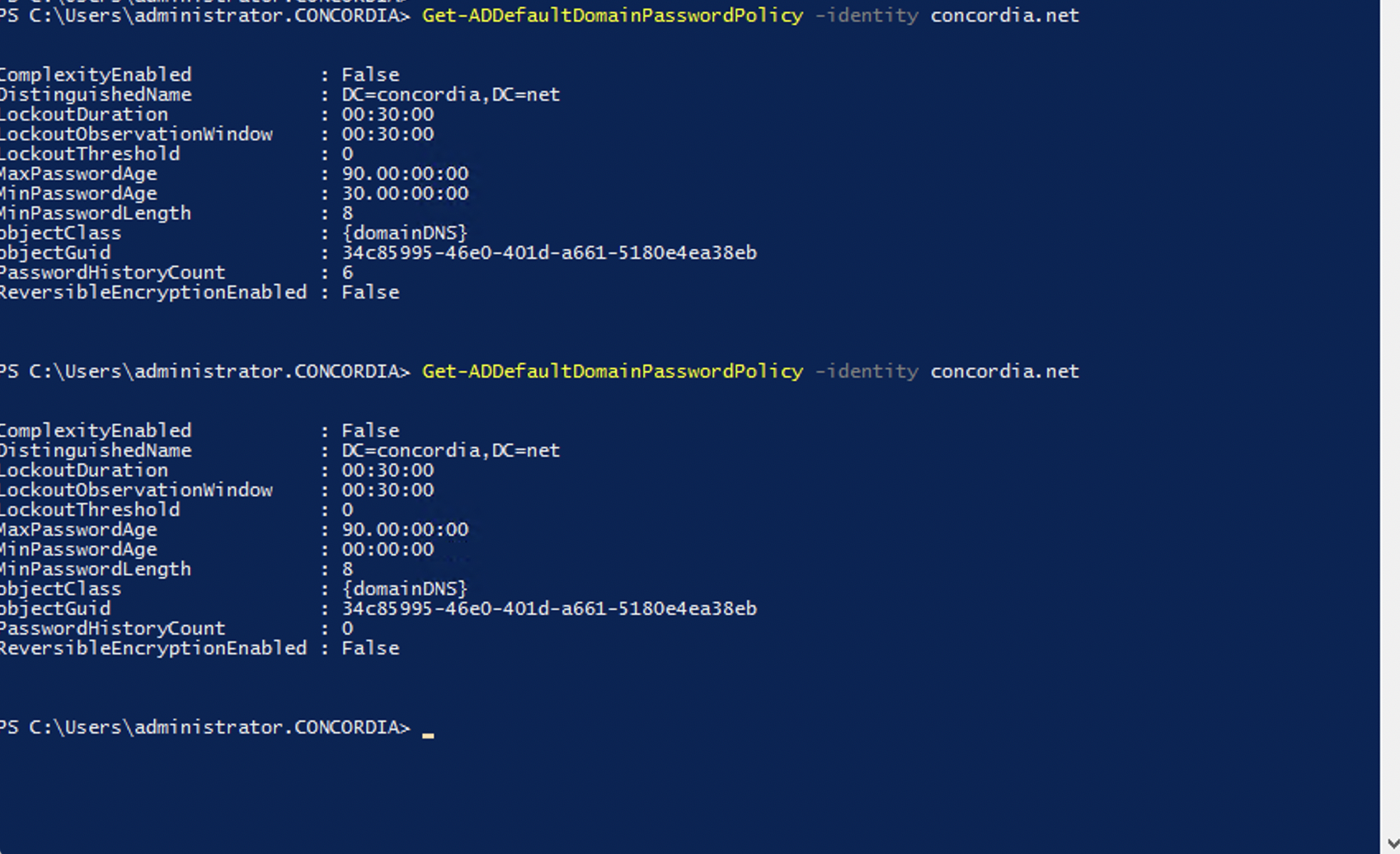
On-prem Ad password Policy ----looks ok
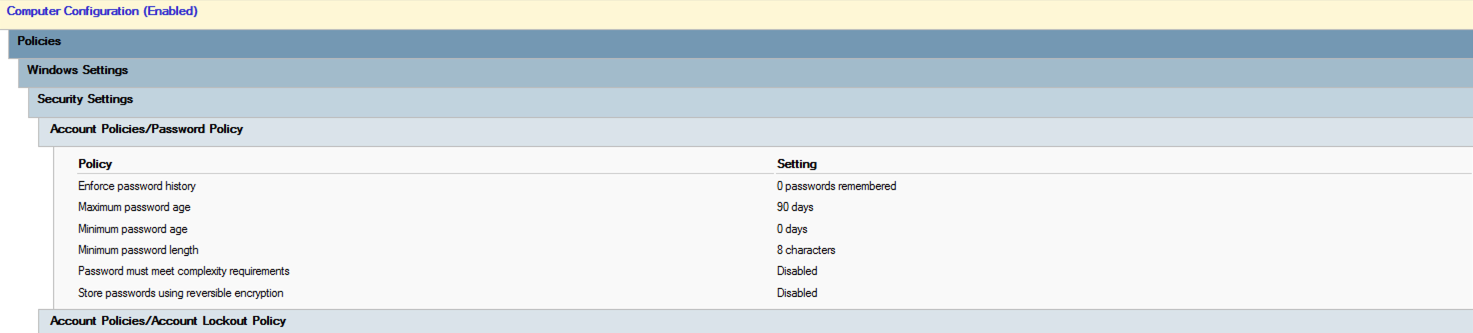
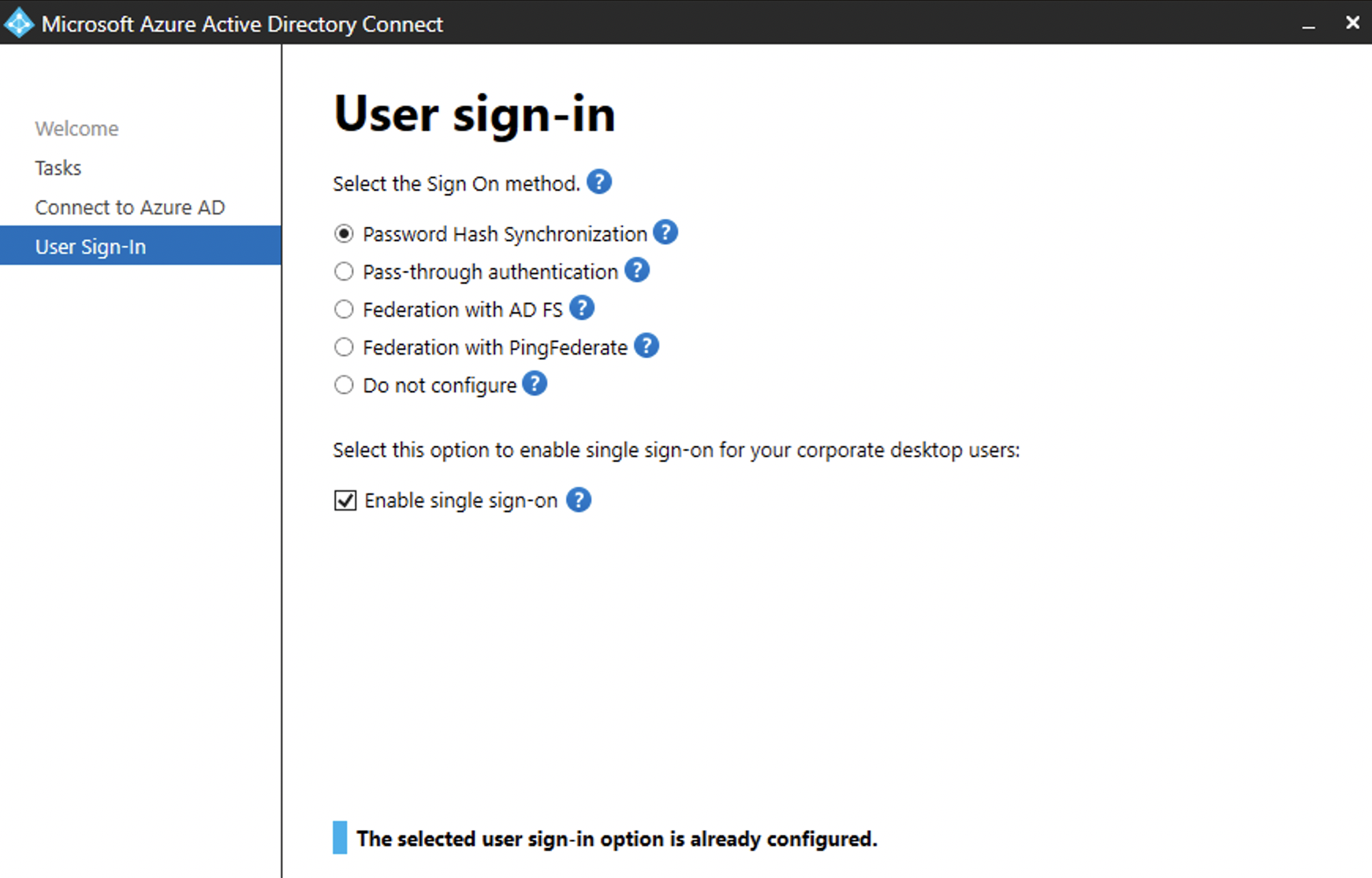
Azure AD - pass hash sync SSO -ok
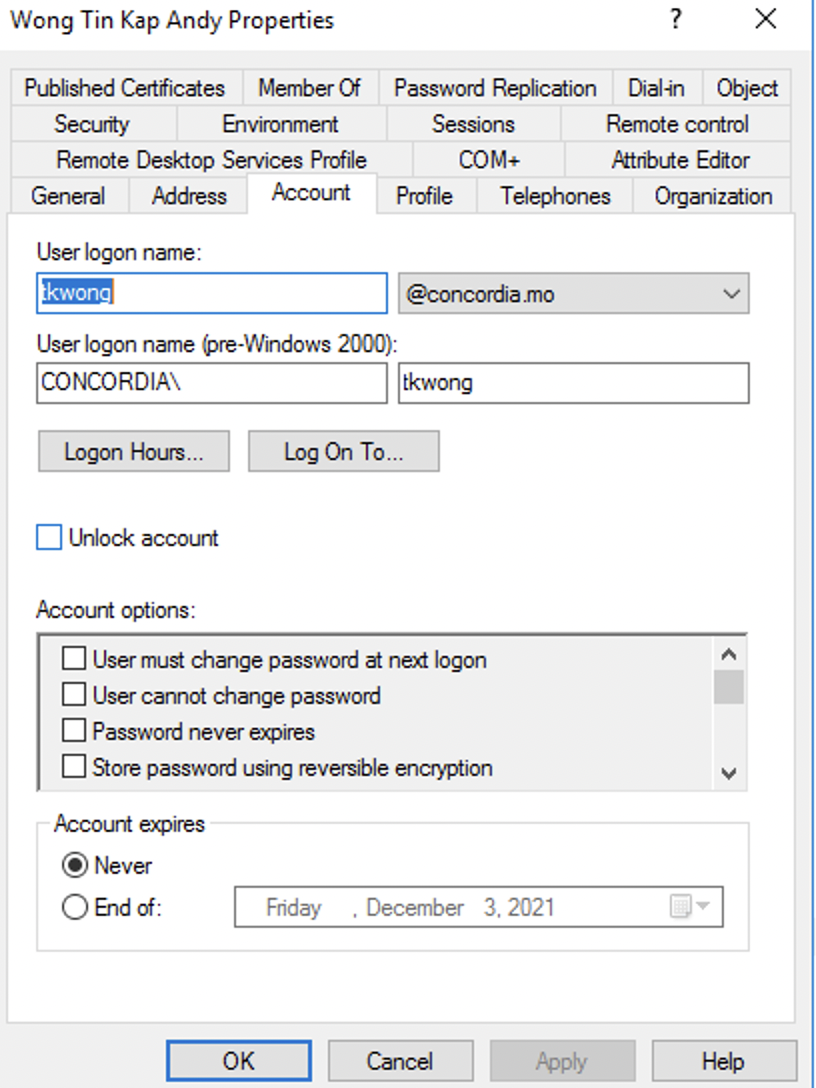
On-prem user - user can not change password - disabled -----ok
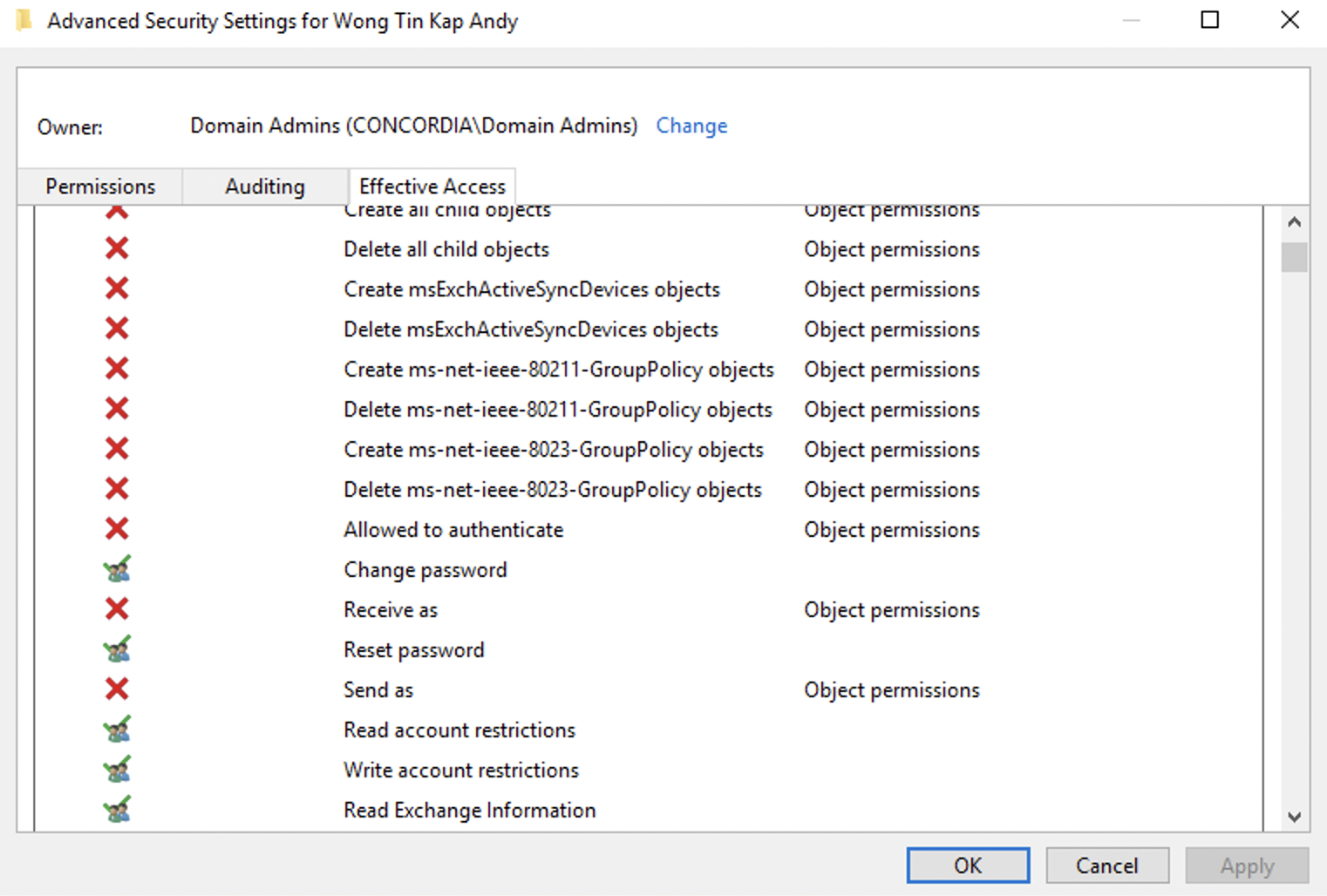
MSOL_XXXXX Account having reset password effective permission
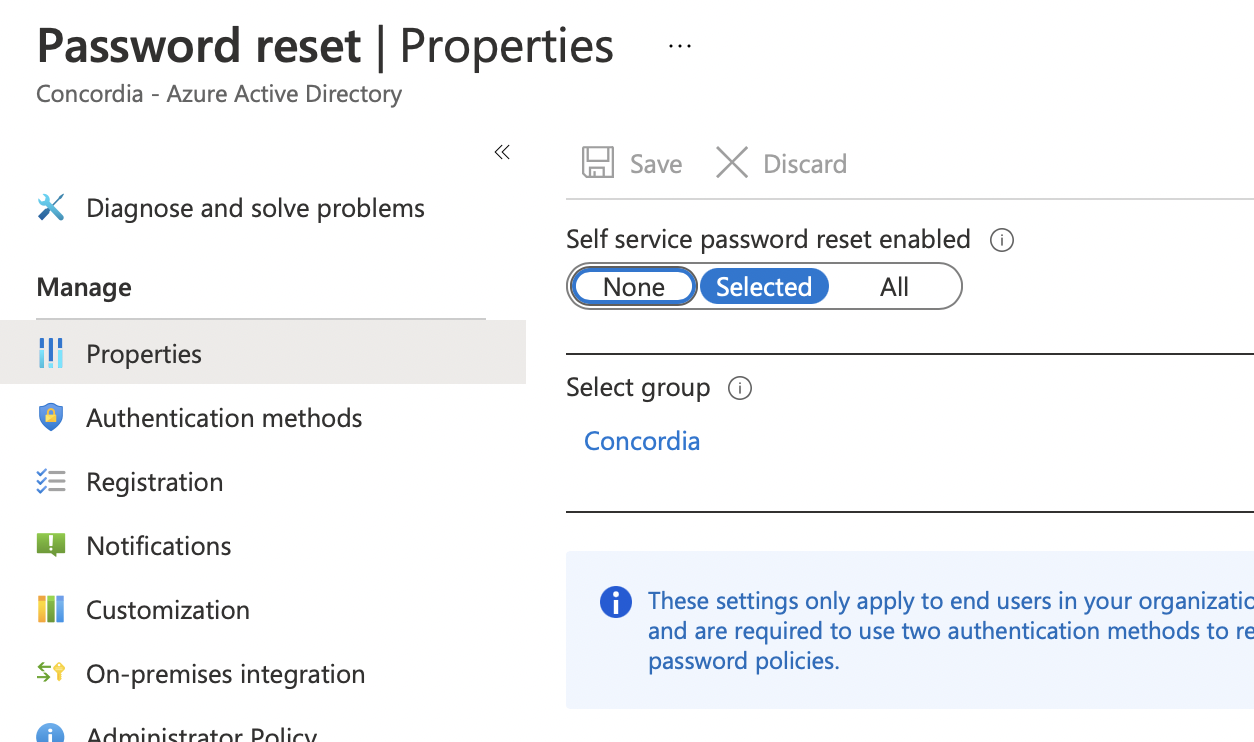
Azure AD password reset config select Group & The group contains the testing user ----ok
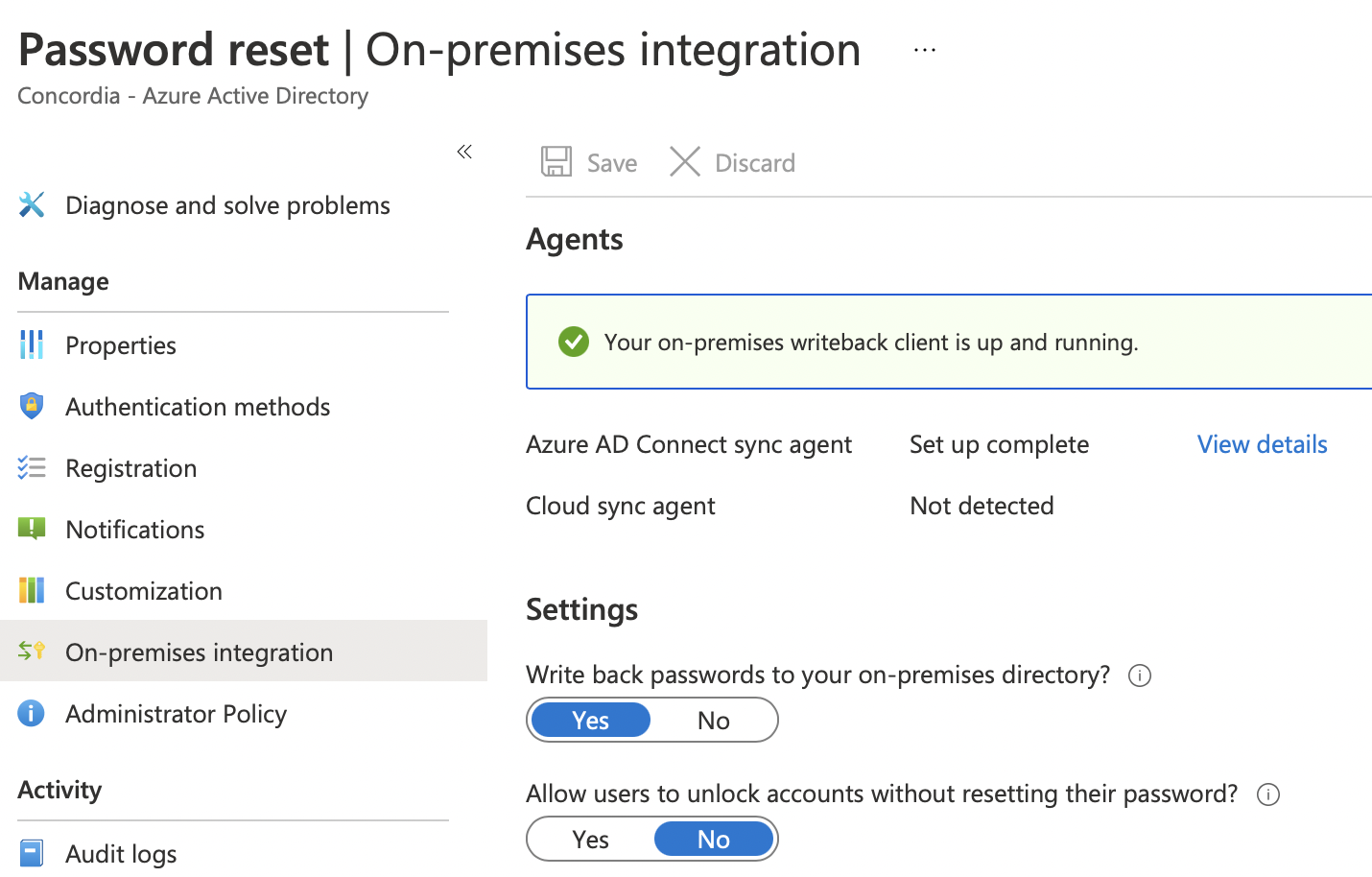
Azure AD Connect installed on windows2016 server Password WriteBack configured----ok
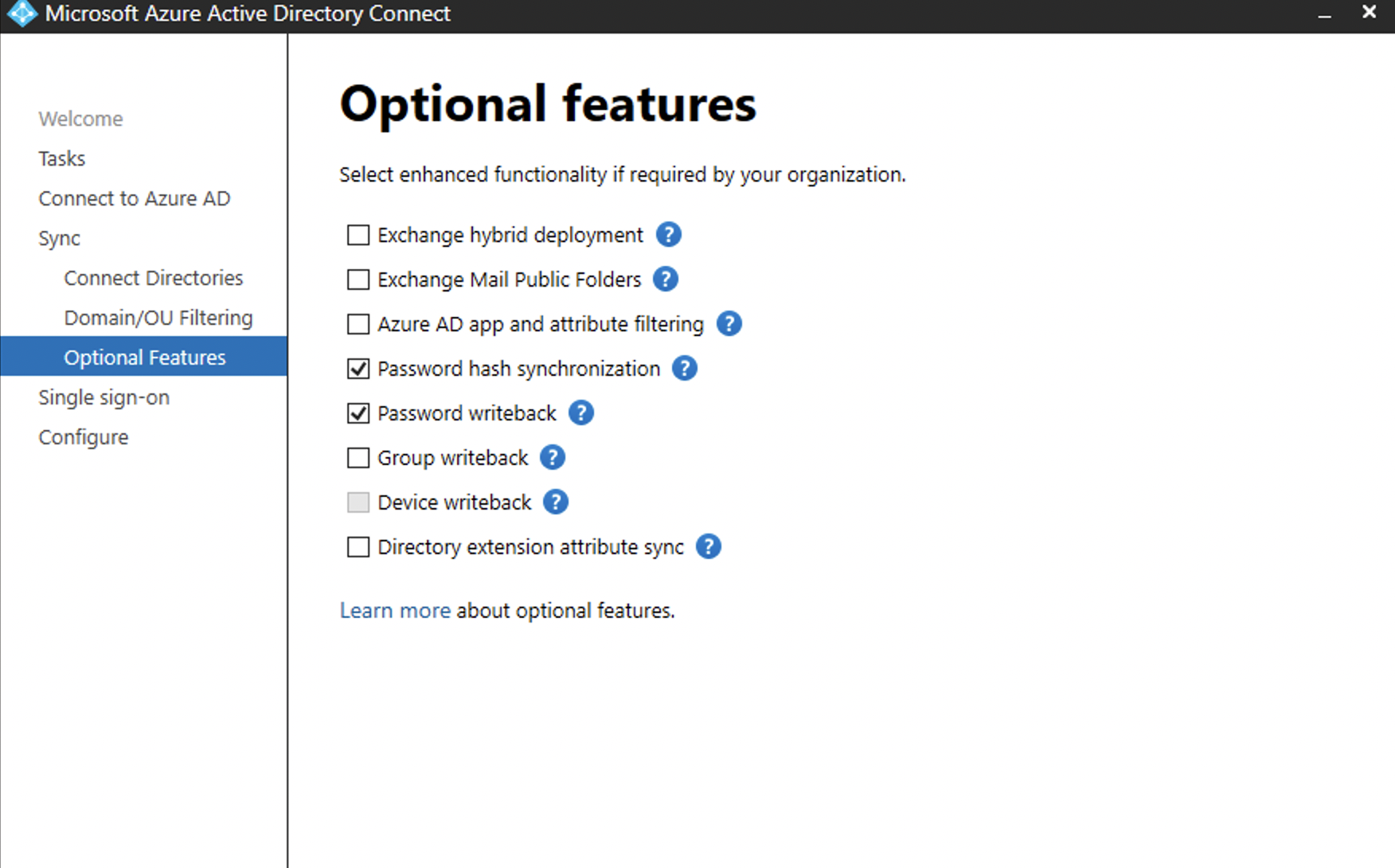
Azure AD Writeback password setting on-----ok
Tried and rollback action
---------------------------
Tried Reset testing user password
Tried add MSOL_account to domain admin
Tried disable Writeback password on Azure AD Connect and enable Writeback setting.
Tried on azure AD connect change connect to different AD Server.
However, all fails.
How I can resolve the issue