I am trying to write an app that retrieves any user info. allowed given an OID. I started with Example 1 here:
https://learn.microsoft.com/en-us/graph/api/user-get?view=graph-rest-1.0&tabs=http
In the process of recreating this request I've been stuck on getting an appropriate token. I want the scope to be User.ReadBasic.All because that appears the scope that will allow retrieval of some info. without Admin consent. In the above link I see that the User.ReadBasic.All scope is available for Delegated (work or school account).
Q. 1.:
I think I have a work account. Can someone tell me if that is not the case based on this screenshot?

I registered an app with User.ReadBasic.All permission as shown below:
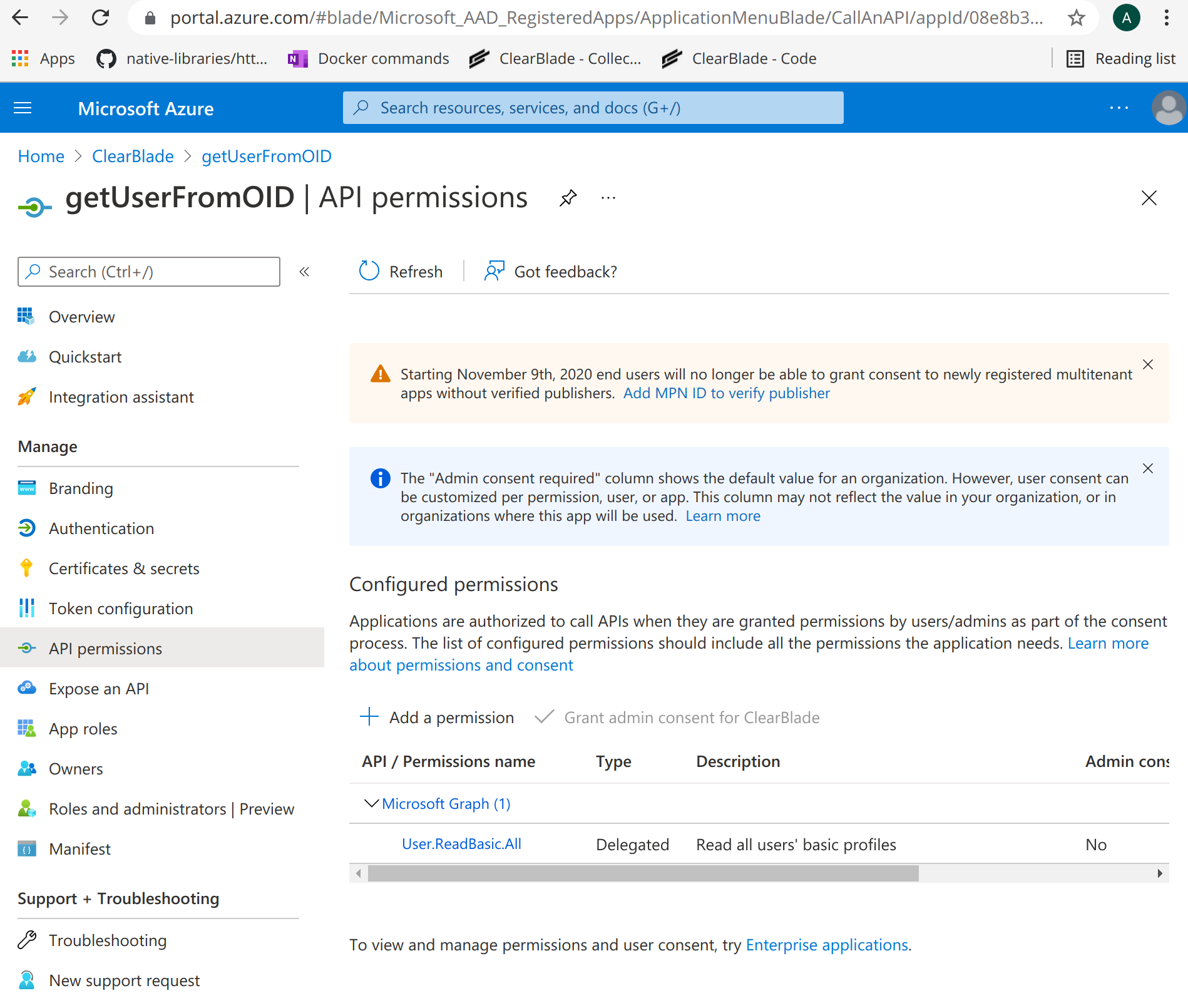
Not sure what the first link meant by leaving off User.ReadBasic.All from Application, but I see here I can add that permission to my app. So not sure if I'm misunderstanding something.
I copied the scope URL https://graph.microsoft.com/User.ReadBasic.All as per here:
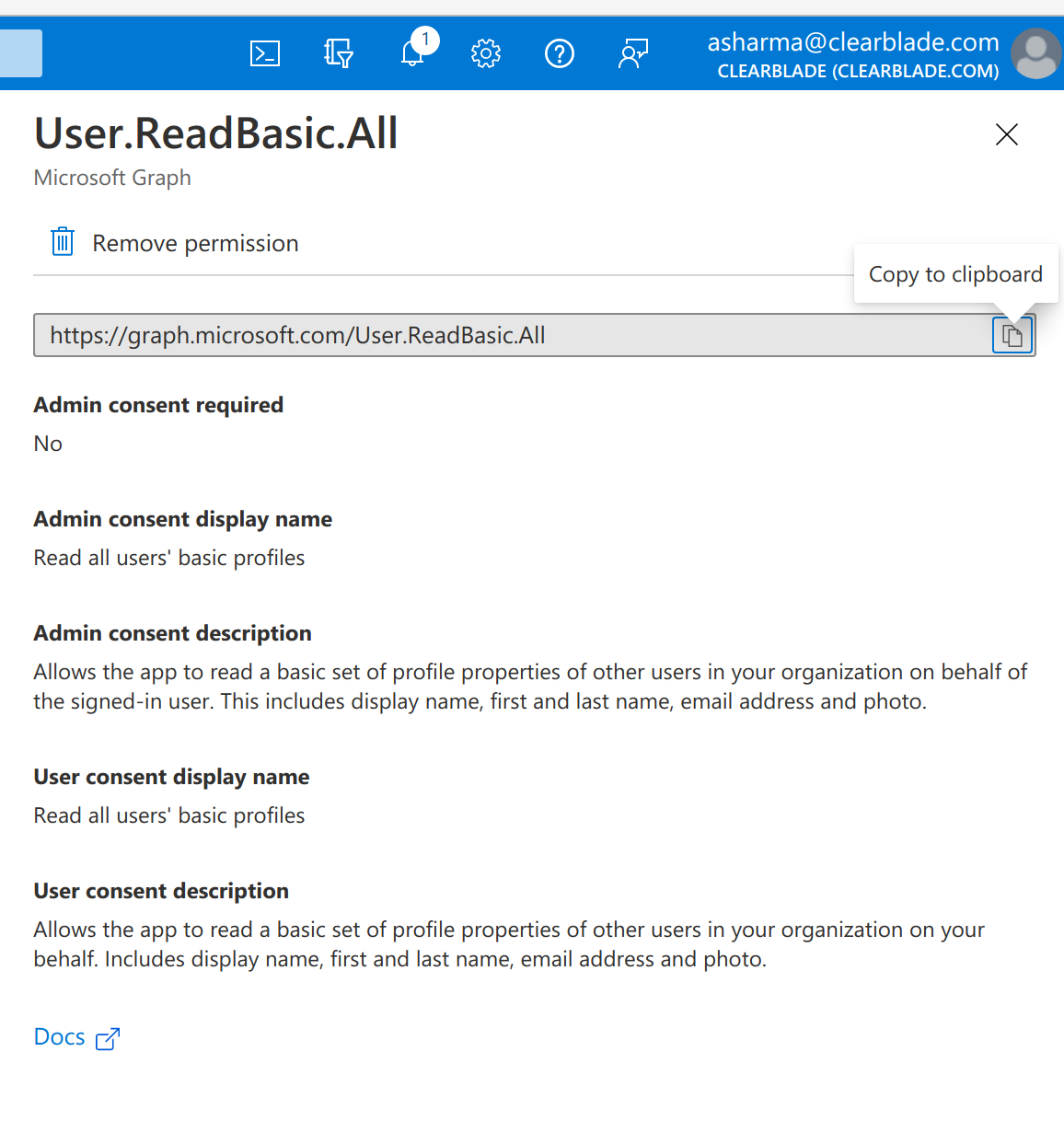
Next I retrieved a token using this link:
https://learn.microsoft.com/en-us/graph/auth-v2-service
I tried to use &scope=https%3A%2F%2Fgraph.microsoft.com%2FUser.ReadBasic.All but that returned no token. I see that I can ONLY use &scope=https%3A%2F%2Fgraph.microsoft.com%2F.default to get a token.
When I use this token to hit the v1.0/users endpoint from the first link the response contains code Authorization_RequestDenied and message Insufficient privileges to complete the operation.
I did try going through the "Get Authorization" step here and got through the Consent dialog and then try the above again, but same result:
https://learn.microsoft.com/en-us/graph/auth-v2-user
I followed the suggestion from CarlZhao-MSFT here:
https://learn.microsoft.com/en-us/answers/questions/577832/unable-to-list-users-from-graph-authorization-requ.html
I parsed my token and I see that there is no scp item:
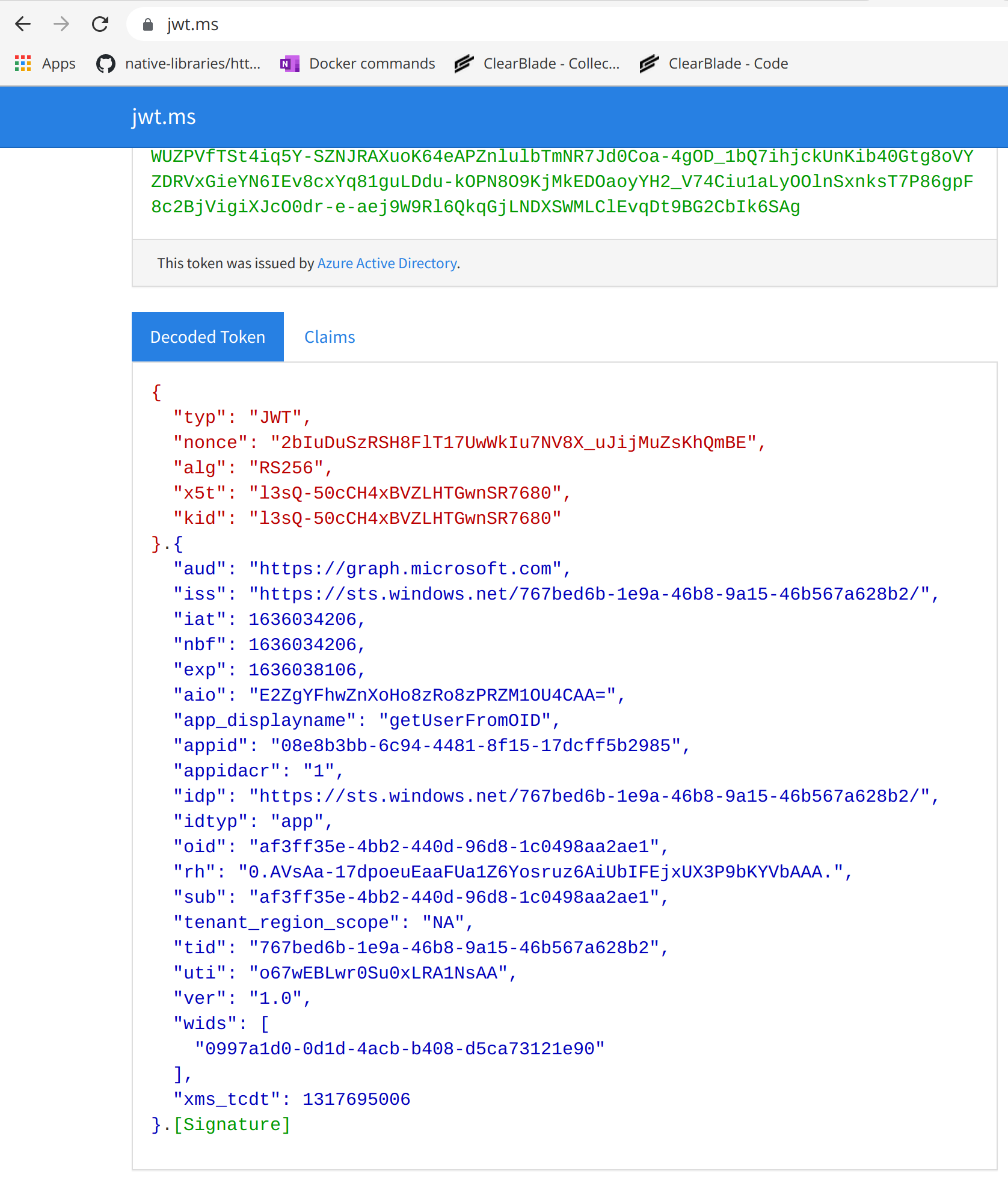
Hence I asked Q. 1 above.
Q. 2:
Is there another reason there is no "scp": "User.ReadBasic.All" item in my parsed JWT?
Q. 3:
My goal is to have an app retrieve ANY info. at all given an OID without Admin consent. Is that possible? If so what should I do differently?






