
Hello
Thank you for posting here.
1.On the machines that we can see these event ID (4663, 4658 and 5156), we can check the status of the related audit policy settings with the following command.
auditpol /get /category:*
For example:
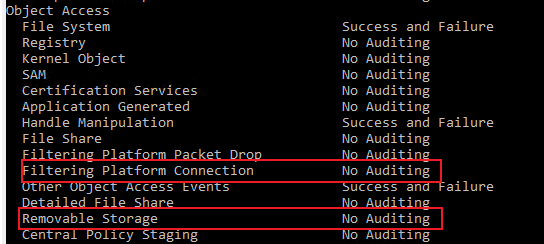
2.We can also check if we configured the related audit policy settings through gpresult file.
Logon the machine that we can see these event ID (4663, 4658 and 5156) with Administrator.
Open CMD (run as Administrator) and type gpresult /h C:\audit.html and click Enter.
And open the audit.html and check the audit settings (including domain policy settings and local policy settings) under “Computer Details”, check if there are settings “Audit Removable Storage” and “Audit Filtering Platform Connection”.
For example:
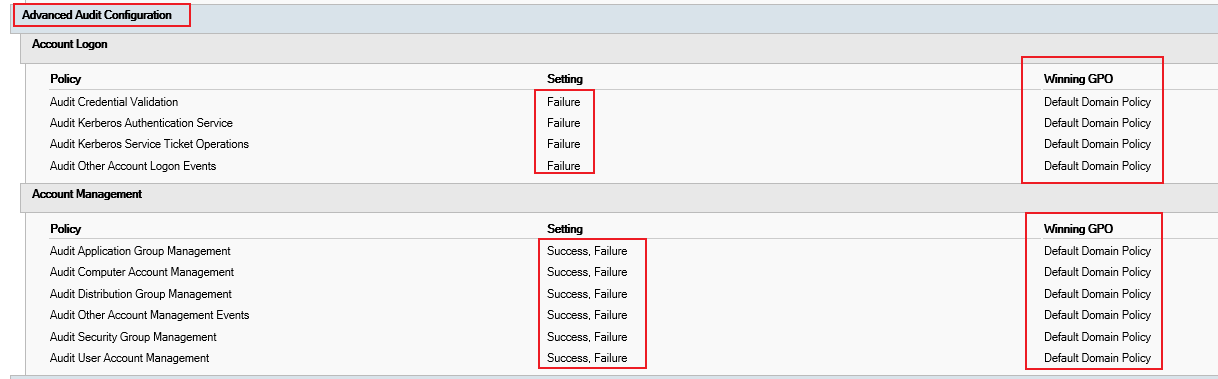
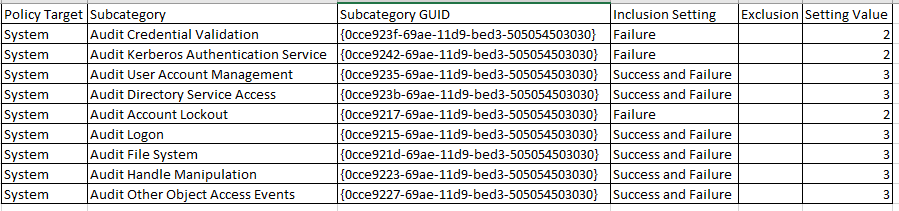
3.On one problematic server, we can try to check if we can see the related audit policy settings ( “Audit Removable Storage” and “Audit Filtering Platform Connection”) in the following path:
\a.local\SYSVOL\a.local\Policies{31B2F340-016D-11D2-945F-00C04FB984F9}\MACHINE\Microsoft\Windows NT\Audit.csv
C:\Windows\security\audit.csv
{31B2F340-016D-11D2-945F-00C04FB984F9} is the GUID of the default domain policy.
The audit.csv look just like this:
Best Regards,
Daisy Zhou