@Steven Stanley It looks like your devices got Auto-enrolled to Microsoft Endpoint manager (Formally Microsoft Intune) and some policies are being applied from there when you did a hybrid Azure AD joined.
The autoenrollment into Intune setting can be found at : https://learn.microsoft.com/en-us/mem/autopilot/windows-autopilot-hybrid#set-up-windows-automatic-enrollment
Coming to your questions :
1) On a windows 10 machine, go to Settings - Accounts - Access work or School Account -
Click on the registered account that you see and then click on Info. That will show all the policies and applications coming from Microsoft Intune.
2) Create the Advanced diagnostic report from same page after clicking Info, it will show you the authority of the policy coming down.
Use this link to find the place where you need to export it from.
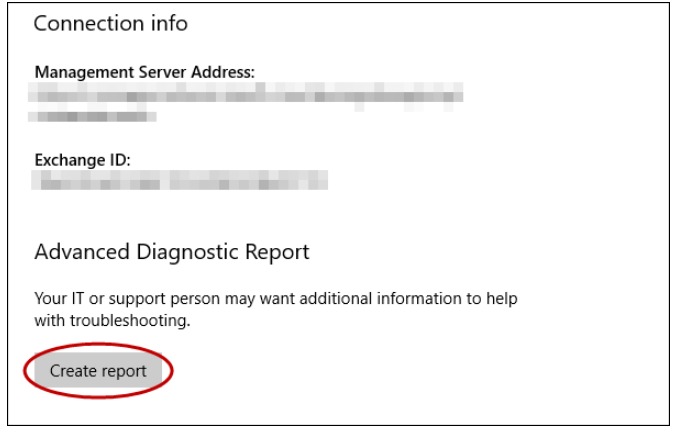
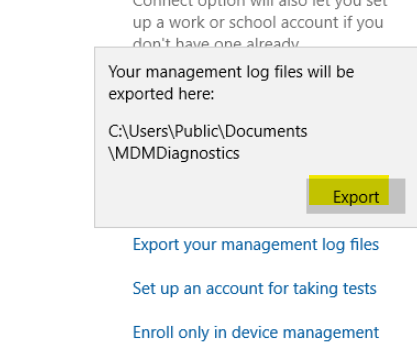
Do let me know if this helps, we can discuss further if you need something else.
Please remember to "Accept Answer" if any answer/reply helped, so that others in the community facing similar issues can easily find the solution.