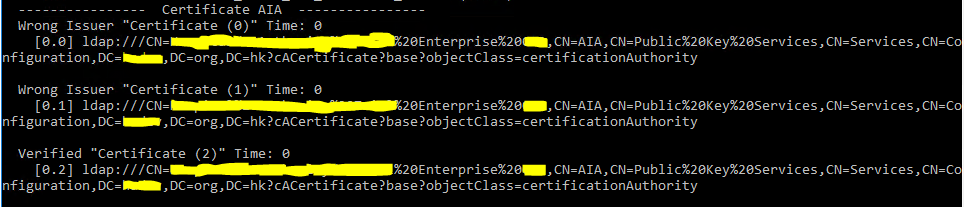
AIA entry may store multiple certificates, this is why you may see multiple entries during validation: certutil enumerates all certificates in the entry and tries to find matching. So it is totally possible to see multiple AIA entries in certutil even if only single URL is specified in cert's AIA extension.
There are two scenarios that may cause this observation:
- You have renewed your CA with new key pair twice. In this case, you should not take any actions. It is perfectly legit and expected behavior.
- someone played with CA in the past and used same name for CA and didn't clean up AD after tests. To test this, open PKIView.msc MMC snap-in, right-click on root node and select Manage AD Containers and switch to AIA tab. Evaluate every certificate and find any that should not be there by comparing them with certificates stored on your CA (in CA properties). If there are certificates left from testing -- you can remove them.