Hello @Bob Doyle
You can create custom policy that will prevent App Service Apps to be injected into a virtual network.
- Find an existing policy "App Service Apps should be injected into a virtual network"
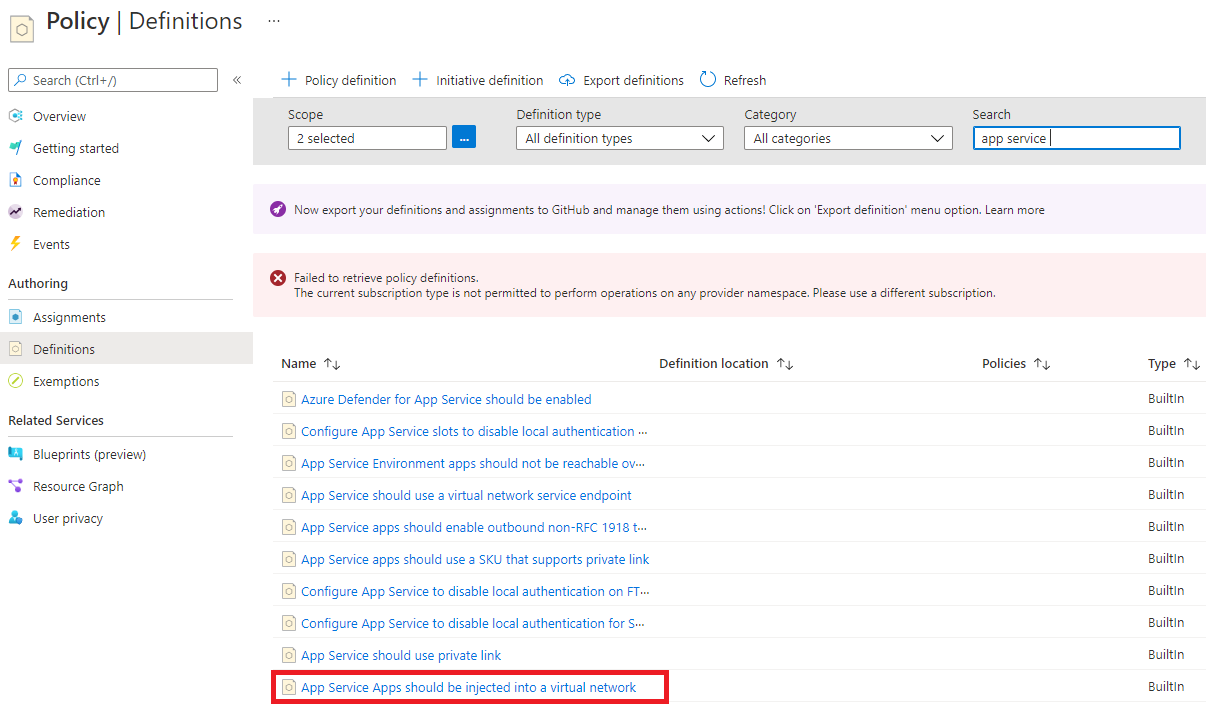
- Duplicate it
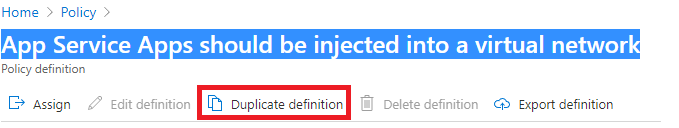
- And modify condition, to prevent App Service Apps to be injected into a virtual network {
"mode": "Indexed",
"policyRule": {
"if": {
"allOf": [
{
"field": "type",
"equals": "Microsoft.Web/sites"
},
{
"field": "Microsoft.Web/sites/virtualNetworkSubnetId",
"notEquals": ""
}
]
},
"then": {
"effect": "[parameters('effect')]"
}
},
"parameters": {
"effect": {
"type": "String",
"metadata": {
"displayName": "Effect",
"description": "Enable or disable the execution of the policy"
},
"allowedValues": [
"Audit",
"Deny",
"Disabled"
],
"defaultValue": "Audit"
}
}
}
https://learn.microsoft.com/en-us/azure/governance/policy/concepts/definition-structure
