Hi Piaudonn,
Situation
As previous capture are all setup at on-premise exchange server 2019, our portal using AD FS OAuth Single sign-on was successfully done and clears the authentication state well after Single logout, that meant when enter again AD FS OAuth is ready for next login.
Problem
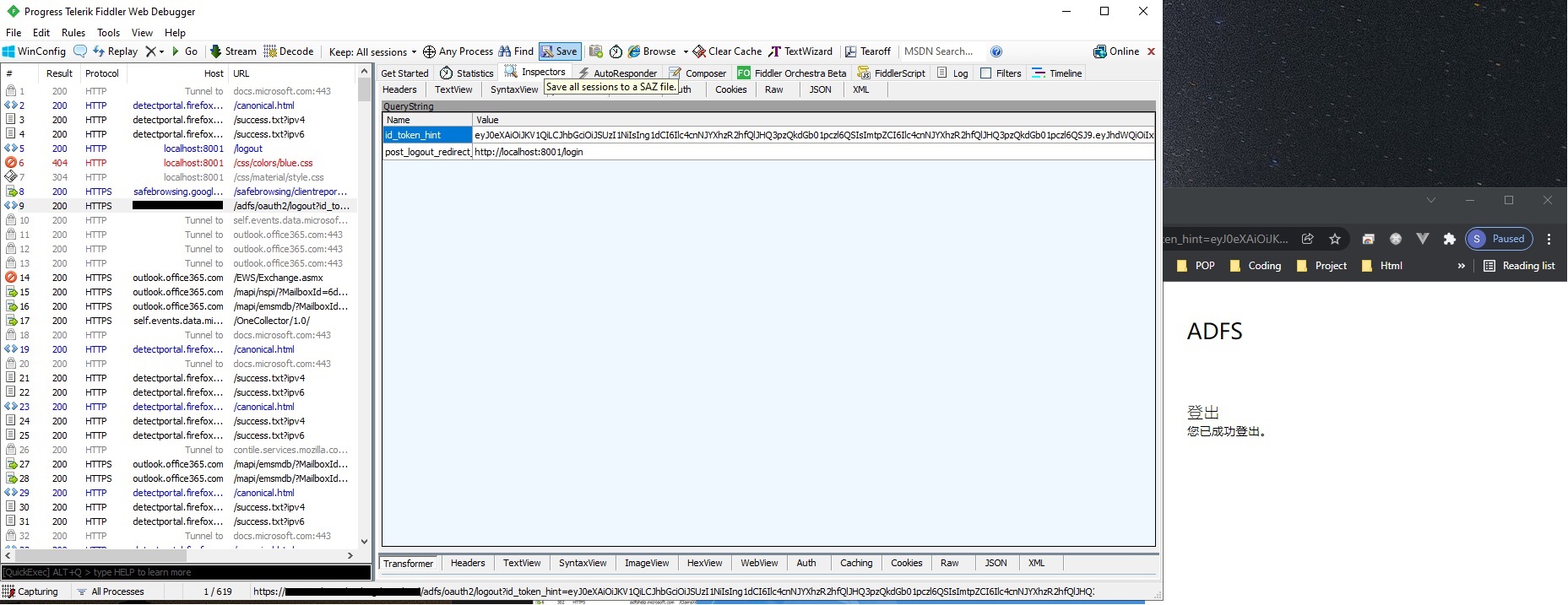
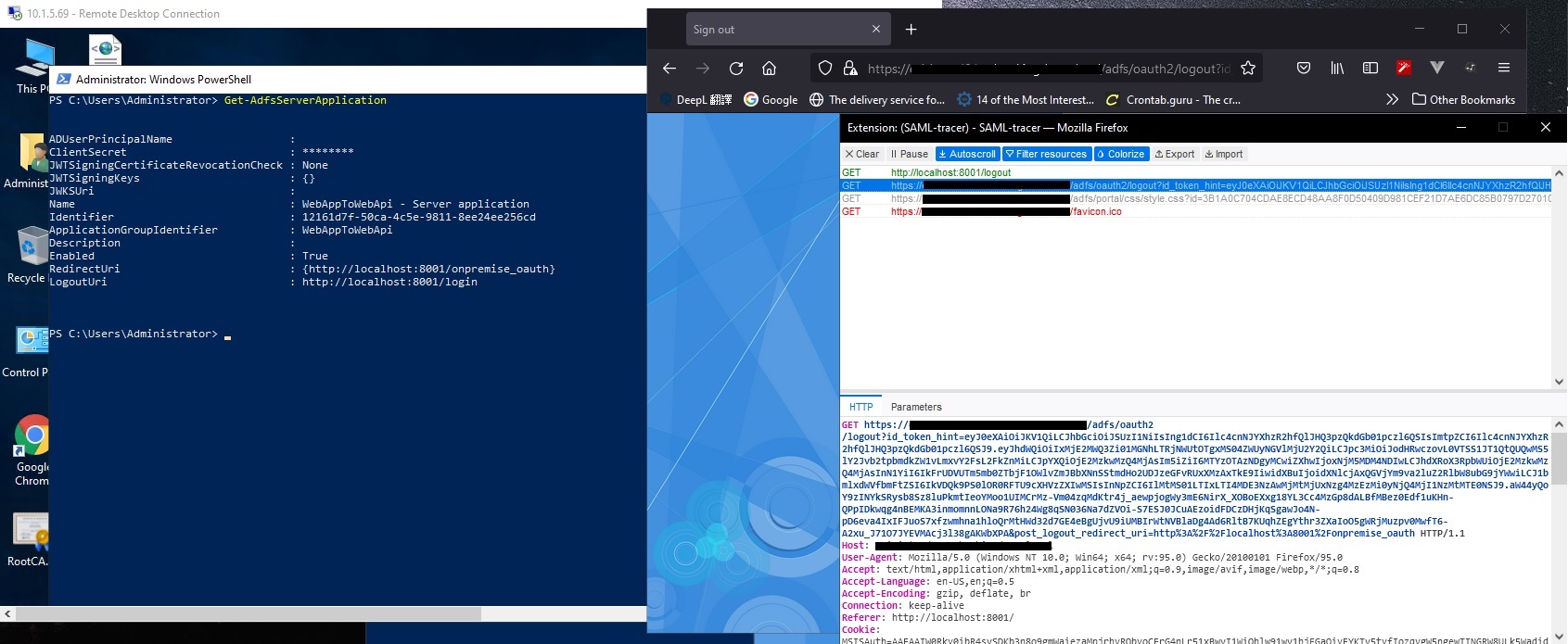
When we given parameter id_token_hint and post_logout_redirect_uri to AD FS Single logout, but not redirect action to our portal( parameter setup in LogoutUri in photo 2 ). Only hold as AD FS login page ( Because of tiny difference from graph OAuth that graph will redirect back to our portal ).
So, is that important of our server hostname (remove data) is using?
If yes, i will clone the environment for testing this case.
Enclosed below capture with missing :
Photo 1 : On-premise AD FS server 2019 Hotfix state :
Photo 2 : On-premise AD FS server 2019 LogoutUri :
Regards,
Carl