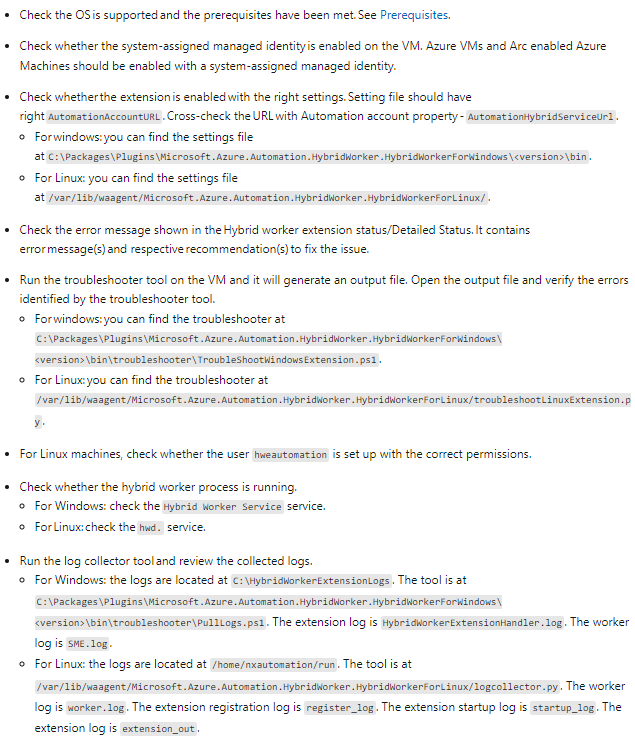
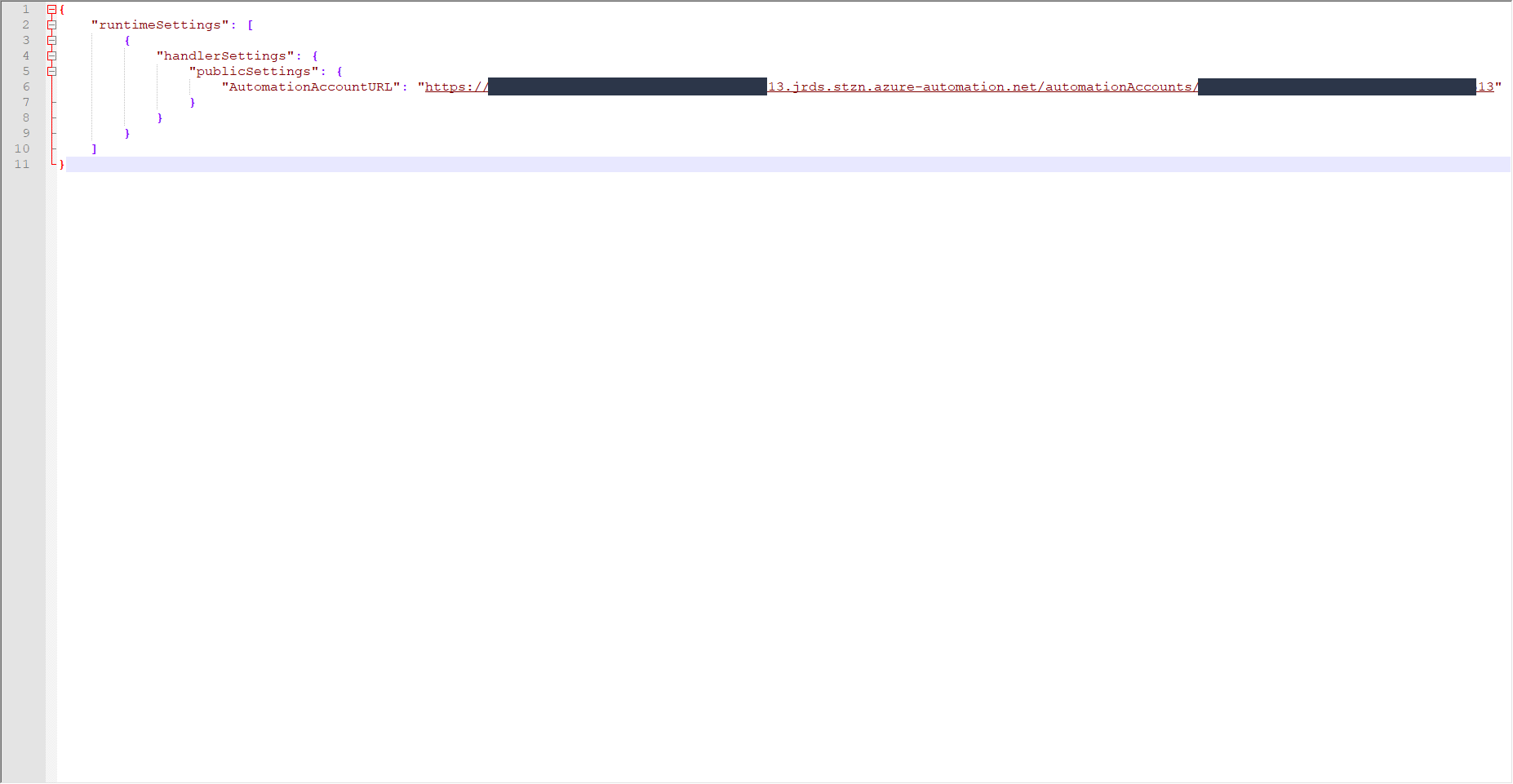
I deployed an Azure Automate Hybrid worker with Azure Arc. Azure Arc was deployed successfully and the server showed up.
I was able to add the server to the hybrid runbook worker group. The extension was successfully installed and is visible in the Azure Arc portal.
But as soon as I try to run any runbook on the server the following eventlog is logged:
Exception in the JobRuntimeDataService SandboxHub implementation [accountId={75fb789b-3594-49b2-bd25-78a070826513}][sandboxId={ff659a0d-c4af-4292-8d43-60175d2f3cd2}][methodName=GetJobAction][exception=JobRuntimeData.Client.JobRuntimeDataServiceClientException: Bad Request {"Message":"Could not authenticate. Certificate is not attached to request."}
[JobRuntimeData.Common.TransientFaultHandling.HttpRequestWithStatusException: Bad Request {"Message":"Could not authenticate. Certificate is not attached to request."}]
at JobRuntimeData.Client.JwtTokenAuthorizationHeaderBuilder.GetAuthorizationHeader() in X:\bt\1222199\repo\src\Shared\JobRuntimeData.Client\JwtTokenAuthorizationHeaderBuilder.cs:line 56
at JobRuntimeData.Client.JobRuntimeDataServiceClient.AddAuthentication(WebClient webClient) in X:\bt\1222199\repo\src\Shared\JobRuntimeData.Client\JobRuntimeDataServiceClient.cs:line 465
at JobRuntimeData.Client.JobRuntimeDataServiceClient.Get[T](String suffixUri, IDictionary`2 queryParameters, IDictionary`2 headers) in X:\bt\1222199\repo\src\Shared\JobRuntimeData.Client\JobRuntimeDataServiceClient.cs:line 353
at JobRuntimeData.Client.Operations.JobOperations.JobOperations.GetJobActions(Guid accountId, Guid sandboxId) in X:\bt\1222199\repo\src\Shared\JobRuntimeData.Client\Operations\JobOperations\JobOperations.cs:line 62
at Orchestrator.Runtime.JobRuntimeDataProvider.JobRuntimeDataProvider.GetJobAction(Guid sandboxId) in X:\bt\1222199\repo\src\Shared\Orchestrator.Runtime\JobRuntimeDataProvider\JobRuntimeDataProvider.cs:line 70
at Orchestrator.Runtime.JobRuntimeDataProvider.JobRuntimeDataProviderExceptionHandler.GetJobAction(Guid sandboxId) in X:\bt\1222199\repo\src\Shared\Orchestrator.Runtime\JobRuntimeDataProvider\JobRuntimeDataProviderExceptionHandler.cs:line 71
inner exception -> JobRuntimeData.Common.TransientFaultHandling.HttpRequestWithStatusException: Bad Request {"Message":"Could not authenticate. Certificate is not attached to request."}
at JobRuntimeData.Client.ImdsClient.<InvokeRequest>d__10`1.MoveNext() in X:\bt\1222199\repo\src\Shared\JobRuntimeData.Client\ImdsClient.cs:line 111
--- End of stack trace from previous location where exception was thrown ---
at System.Runtime.ExceptionServices.ExceptionDispatchInfo.Throw()
at System.Runtime.CompilerServices.TaskAwaiter.HandleNonSuccessAndDebuggerNotification(Task task)
at JobRuntimeData.Client.ImdsClient.<GetMsiTokenAsync>d__9`1.MoveNext() in X:\bt\1222199\repo\src\Shared\JobRuntimeData.Client\ImdsClient.cs:line 0
--- End of stack trace from previous location where exception was thrown ---
at System.Runtime.ExceptionServices.ExceptionDispatchInfo.Throw()
at System.Runtime.CompilerServices.TaskAwaiter.HandleNonSuccessAndDebuggerNotification(Task task)
at JobRuntimeData.Client.JwtTokenAuthorizationHeaderBuilder.<>c.<GetAuthorizationHeader>b__12_0() in X:\bt\1222199\repo\src\Shared\JobRuntimeData.Client\JwtTokenAuthorizationHeaderBuilder.cs:line 46
at JobRuntimeData.Common.TransientFaultHandling.RetryPolicy.ExecuteAction[TResult](Func`1 func) in X:\bt\1222199\repo\src\Shared\JobRuntimeData.Common\TransientFaultHandling\RetryPolicy.cs:line 137
at JobRuntimeData.Client.JwtTokenAuthorizationHeaderBuilder.GetAuthorizationHeader() in X:\bt\1222199\repo\src\Shared\JobRuntimeData.Client\JwtTokenAuthorizationHeaderBuilder.cs:line 46
]
I am not using any Run-As credentials so there is no certificate involved there.
Someone has any idea what is missing now?