Advised to post here by our account manager for feedback from the fast track team.
Requirements
- We want to improve our network security by denying public (internet) access to services such as SQL Server, Storage Accounts, CosmosDB and Key Vault.
- We would prefer to deny all Azure Services access expect via private link or specific network.
- We want to create network separation for our test and production applications when accessing services. For example, a test web app (app service) should not be able to connect to a production database, even if it is using a connection string with credentials.
We have come up with a proposed network design (below) by referring to the article https://learn.microsoft.com/en-us/azure/architecture/example-scenario/private-web-app/private-web-app
This will be a big change from our current situation, so we are seeking some feedback on our proposed approach before we commence work.
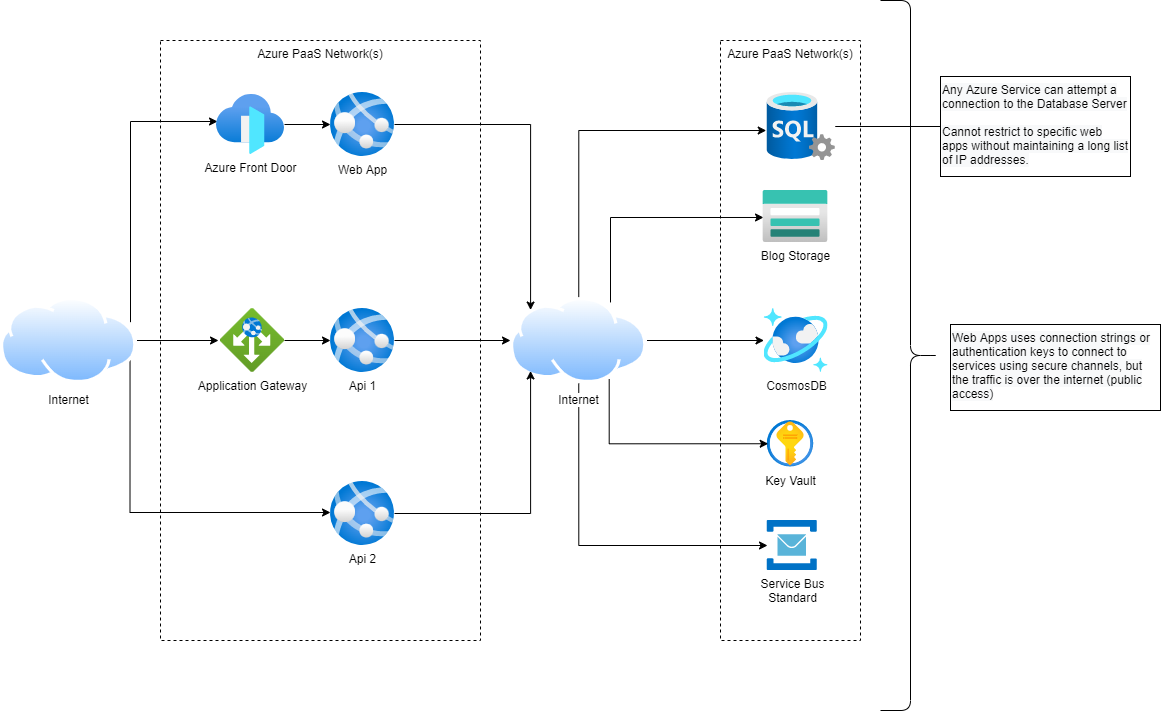
Current Networking for App Services (see diagram)
- Azure Front Door or Application Gateway sits in front of some web apps and services. Most apps are accessed directly.
- Web apps and services connect to Azure services (SQL Server, Storage Acccounts, CosmosDB, Key Vault and Service Bus) over the Internet, using secure protocols and connection strings / keys
- Azure services allow public (internet) access with no network restrictions or private links.
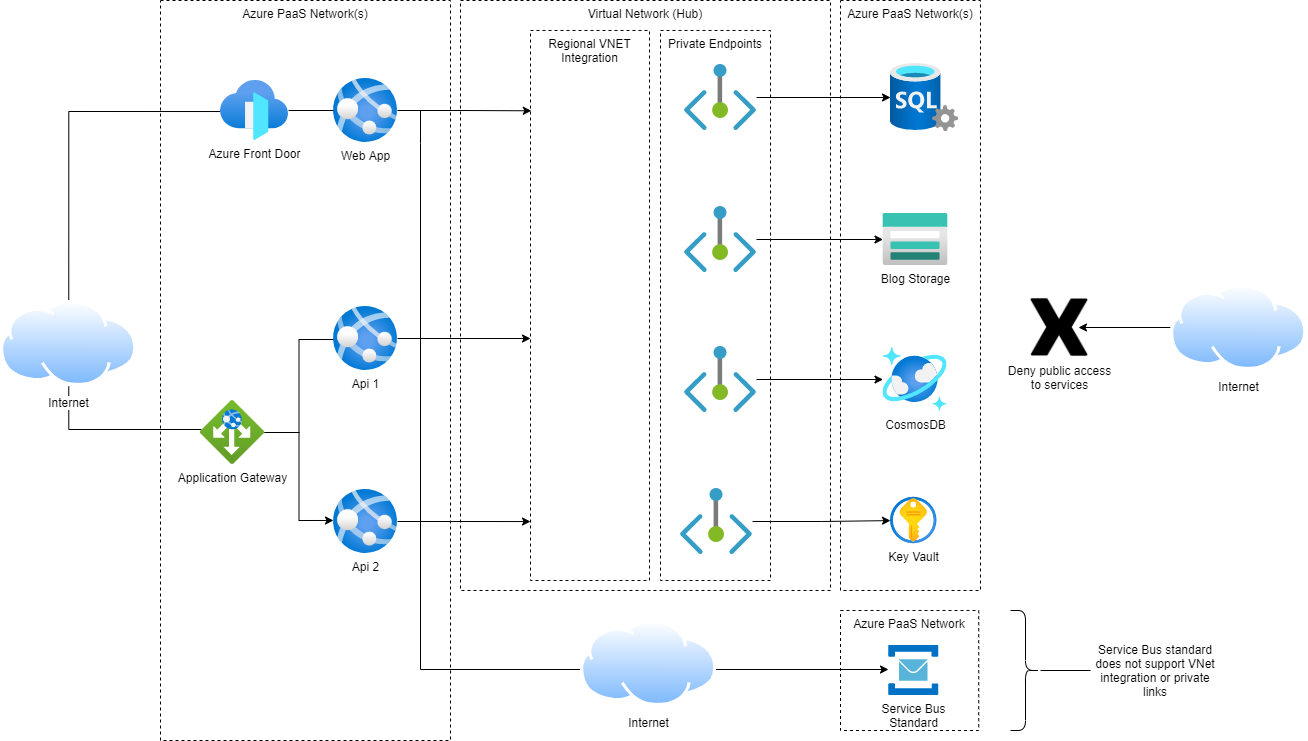
Proposed Networking for App Services (see diagram)
- Azure Front Door or Application Gateway sits in front of all web apps and services. We haven't done this previously due to cost. However, if we can reduce the cost by sharing AFD / App Gateway across multiple apps, it might be feasible.
- Use VNet integration for all web apps and services to a dedicated subnet in our VNet hub.
- Establish Private Links from the VNet Hub to each Azure Service (SQL Server, Storage Acccounts, CosmosDB, Key Vault and Service Bus).
- Configure Azure Services to deny public (internet) access. Only connections over private links are allowed.
- We use Service bus standard, which does not support VNet integration and Service bus premium is outside our budget. Apps would still need to connect to service bus over the internet.