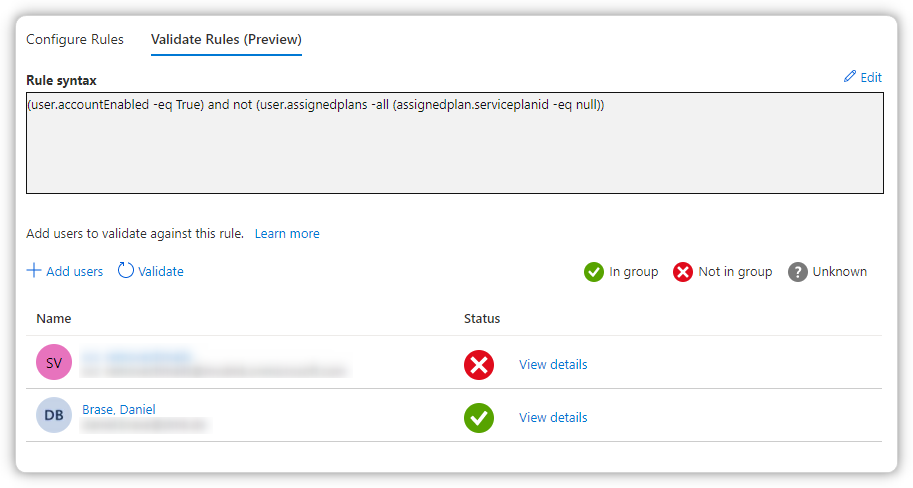
Hi guys,
I'm trying to create a dynamic security group with only licensed users. I've already found this and some other examples to get this working. To test around I started with this filter:
(user.accountEnabled -eq True) and (user.assignedplans -any (assignedplan.serviceplanid -eq "3e26ee1f-8a5f-4d52-aee2-b81ce45c8f40"))
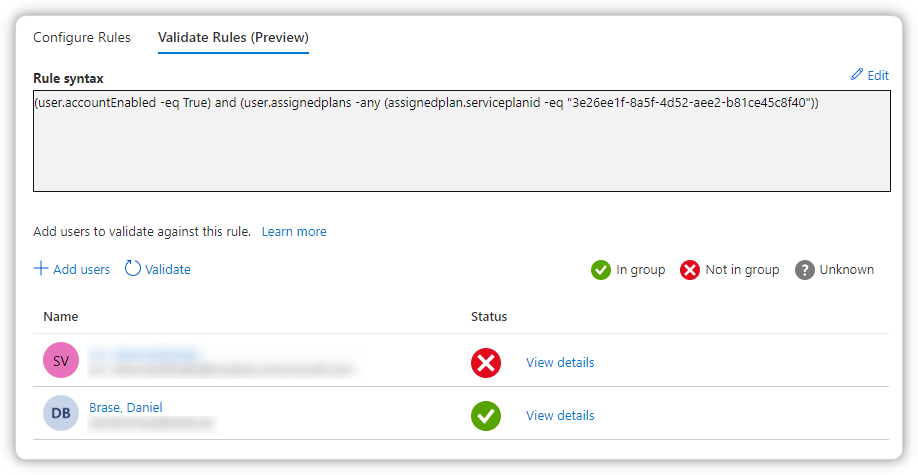
This works generally, but I want a rule with any plan and not a specific one. So I tried this one:
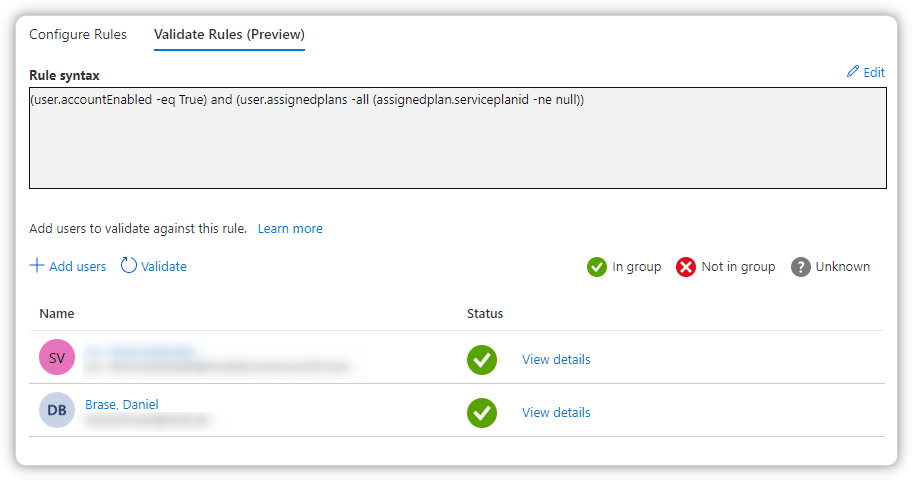
(user.accountEnabled -eq True) and (user.assignedplans -all (assignedplan.serviceplanid -ne null))
But that doesn't work in my case:
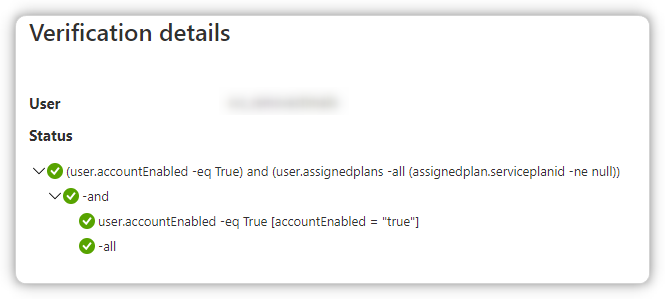
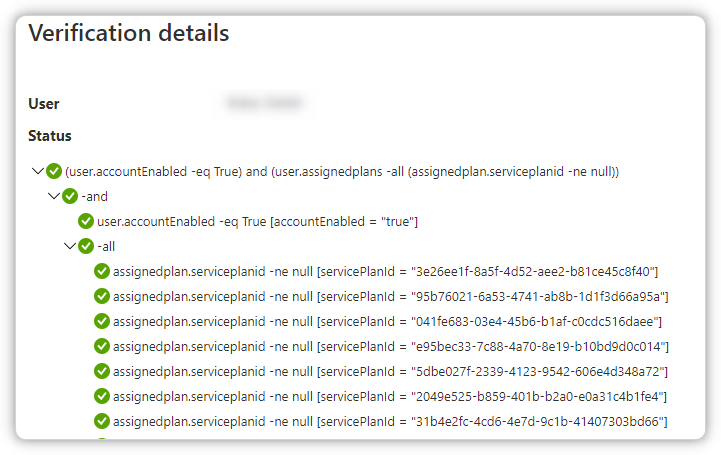
This is also working but I want it vice versa:
(user.accountEnabled -eq True) and (user.assignedplans -any (assignedplan.serviceplanid -eq null)
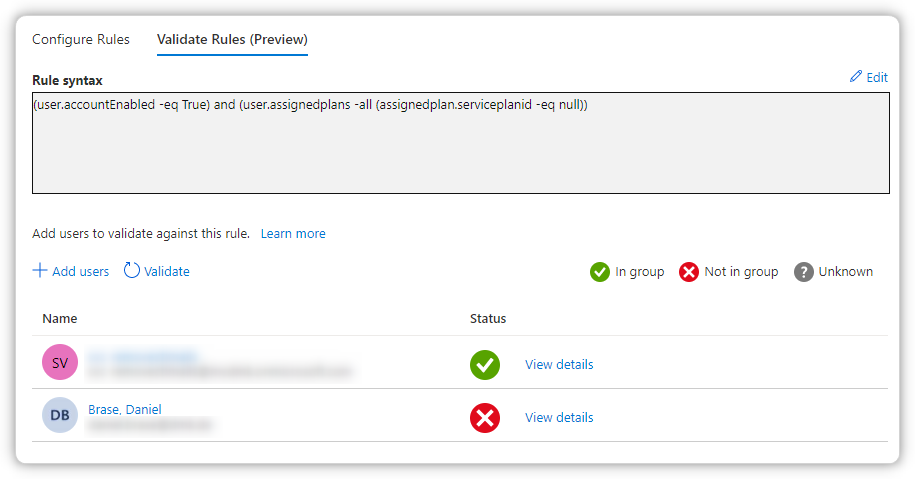
Maybe someone has a hint.
Thanks, Daniel.