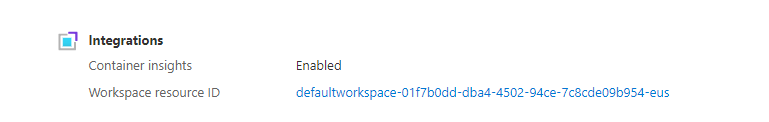
There are no other vnets created in my subscription, I deleted all the resource groups, but still I am getting below error while deploying the template.
{
"status": "Failed",
"error": {
"code": "ServiceCidrOverlapExistingSubnetsCidr",
"target": "networkProfile.serviceCIDR",
"message": "The specified service CIDR 10.0.0.0/16 is conflicted with an existing subnet CIDR 10.0.0.0/16"
}
}
My template:
{
"$schema": "https://schema.management.azure.com/schemas/2019-04-01/deploymentTemplate.json#",
"contentVersion": "1.0.0.0",
"parameters": {
"clusterName": {
"type": "string",
"defaultValue": "aks101cluster",
"metadata": {
"description": "The name of the Managed Cluster resource."
}
},
"osDiskSizeGB": {
"type": "int",
"defaultValue": 0,
"maxValue": 1023,
"minValue": 0,
"metadata": {
"description": "Disk size (in GB) to provision for each of the agent pool nodes. This value ranges from 0 to 1023. Specifying 0 will apply the default disk size for that agentVMSize."
}
},
"agentVMSize": {
"type": "string",
"defaultValue": "Standard_B4ms",
"metadata": {
"description": "The size of the Virtual Machine."
}
},
"kubernetesVersion": {
"type": "string",
"defaultValue": "1.7.7",
"metadata": {
"description": "The version of Kubernetes."
}
},
"networkPlugin": {
"type": "string",
"defaultValue": "azure",
"allowedValues": ["azure", "kubenet"],
"metadata": {
"description": "Network plugin used for building Kubernetes network."
}
},
"enableRBAC": {
"type": "bool",
"defaultValue": true,
"metadata": {
"description": "Boolean flag to turn on and off of RBAC."
}
},
"enablePrivateCluster": {
"type": "bool",
"defaultValue": false,
"metadata": {
"description": "Enable private network access to the Kubernetes cluster."
}
},
"enableHttpApplicationRouting": {
"type": "bool",
"defaultValue": true,
"metadata": {
"description": "Boolean flag to turn on and off http application routing."
}
},
"enableAzurePolicy": {
"type": "bool",
"defaultValue": false,
"metadata": {
"description": "Boolean flag to turn on and off Azure Policy addon."
}
},
"networkPolicy": {
"type": "string",
"defaultValue": "azure",
"metadata": {
"description": "Network policy used for building Kubernetes network."
}
},
"serviceCidr": {
"type": "string",
"defaultValue": "10.0.0.0/16",
"metadata": {
"description": "A CIDR notation IP range from which to assign service cluster IPs."
}
},
"dnsServiceIP": {
"type": "string",
"defaultValue": "10.0.0.10",
"metadata": {
"description": "Containers DNS server IP address."
}
},
"dockerBridgeCidr": {
"type": "string",
"defaultValue": "172.17.0.1/16",
"metadata": {
"description": "A CIDR notation IP for Docker bridge."
}
}
},
"variables": {
"location": "[resourceGroup().location]",
"dnsPrefix": "[toLower(format('{0}-{1}', parameters('clusterName'), uniqueString(resourceGroup().id, parameters('clusterName'))))]",
"virtualNetworkName": "MyVNET"
},
"functions": [],
"resources": [
{
"type": "Microsoft.ContainerService/managedClusters",
"apiVersion": "2020-09-01",
"dependsOn": [
"[resourceId('Microsoft.Network/virtualNetworks', variables('virtualNetworkName'))]"
],
"name": "[parameters('clusterName')]",
"location": "[variables('location')]",
"identity": {
"type": "SystemAssigned"
},
"properties": {
"kubernetesVersion": "[parameters('kubernetesVersion')]",
"enableRBAC": "[parameters('enableRBAC')]",
"dnsPrefix": "[variables('dnsPrefix')]",
"agentPoolProfiles": [
{
"name": "agentpool",
"osDiskSizeGB": "[parameters('osDiskSizeGB')]",
"count": 1,
"enableAutoScaling": true,
"minCount": 1,
"maxCount": 2,
"vmSize": "[parameters('agentVMSize')]",
"osType": "Linux",
"mode": "System",
"storageProfile": "ManagedDisks",
"type": "VirtualMachineScaleSets",
"availabilityZones": ["1", "2", "3"],
"vnetSubnetID": "[resourceId('Microsoft.Network/virtualNetworks/subnets', variables('virtualNetworkName'), 'default')]"
}
],
"networkProfile": {
"loadBalancerSku": "standard",
"networkPlugin": "[parameters('networkPlugin')]",
"networkPolicy": "[parameters('networkPolicy')]",
"serviceCidr": "[parameters('serviceCidr')]",
"dnsServiceIP": "[parameters('dnsServiceIP')]",
"dockerBridgeCidr": "[parameters('dockerBridgeCidr')]"
},
"apiServerAccessProfile": {
"enablePrivateCluster": "[parameters('enablePrivateCluster')]"
},
"addonProfiles": {
"httpApplicationRouting": {
"enabled": "[parameters('enableHttpApplicationRouting')]"
},
"azurepolicy": {
"enabled": "[parameters('enableAzurePolicy')]"
}
}
},
"tags": {
"Owner": "uday",
"purpose": "automation of server"
}
},
{
"apiVersion": "2020-11-01",
"name": "[variables('virtualNetworkName')]",
"type": "Microsoft.Network/virtualNetworks",
"location": "[variables('location')]",
"properties": {
"subnets": [
{
"name": "default",
"id": "[resourceId('Microsoft.Network/virtualNetworks/subnets', variables('virtualNetworkName'), 'default')]",
"properties": {
"addressPrefix": "[parameters('serviceCidr')]"
}
}
],
"addressSpace": {
"addressPrefixes": ["10.0.0.0/8"]
}
},
"tags": {}
}
],
"outputs": {
"controlPlaneFQDN": {
"type": "string",
"value": "[reference(resourceId('Microsoft.ContainerService/managedClusters', parameters('clusterName'))).fqdn]"
}
}
}
Please suggest how to fix this.