You are looking in the right place. So the MDMwinsoverGP appears to be configuring correctly. Don't use the CSPs for setting FW. Use Endpoint Security for that. Can you revert to your original Endpoint Security profiles and share the status? See if you can provide the MDM diagnostic report as well.
Intune Policy CSP - ControlPolicyConflict
Tools used:
Intune / endpoint.microsoft.com
Active Directory
All clients are Windows 10 (v1909) or above
I am looking to migrate from our existing On-Prem Sophos antivirus solution to Intune controlled Endpoint Security. As part of the process I need to enable the Defender Antivirus & Firewall services prior to the removal of the current solution, which as per MS documentation should be enabled but remain dormant. Currently there is a group policy in place that disables both the pre-mentioned services. As I have clients working from home that do not have a connection to the on prem Active Directory, I can't exclude them from the GPO that disables the Defender services and have this become active.
To combat this, I have used Intune to enable the MDM policy conflict as per this: https://learn.microsoft.com/en-us/windows/client-management/mdm/policy-csp-controlpolicyconflict
This is via an Intune custom configuration profile assigned to a dynamic group (all windows 10 devices). Config profile is as follows:
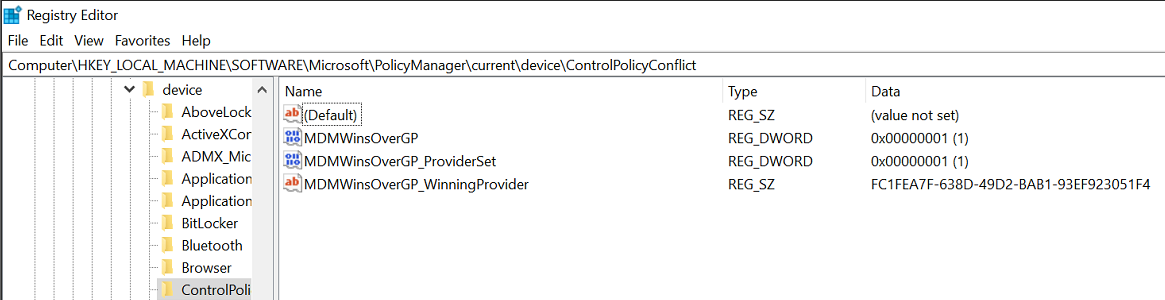
Name: MDMWinsOverGP
OMA-URI: ./Device/Vendor/MSFT/Policy/Config/ControlPolicyConflict/MDMWinsOverGP
Data Type: Integer
Value: 1
I have then configured all relevant Endpoint Security Policies. Unfortunately the firewall policies refuse to take place. So, to try an combat this, I have put in place a Config profile to enable the firewall. This has 3 Custom OMA-URI settings, each as follows:
Name: WinFirewall_DomainProf
OMA-URI: ./Vendor/MSFT/Firewall/MdmStore/DomainProfile/EnableFirewall
Data Type: Boolean
Value: True
Name: WinFirewall_PrivateProf
OMA-URI: ./Vendor/MSFT/Firewall/MdmStore/PrivateProfile/EnableFirewall
Data Type: Boolean
Value: True
Name: WinFirewall_PublicProf
OMA-URI: ./Vendor/MSFT/Firewall/MdmStore/PublicProfile/EnableFirewall
Data Type: Boolean
Value: True
Unfortunately the profile does not over write the GPO and when looking at the device status of my test group assigned to the Firewall policies, all I get is a deployment status of "Conflict" and the firewall stays disabled. As part of my testing I have removed the existing Antivirus solution, but the result stays the same.
GPO -> Firewall = Disabled
Intune -> Firewall = Enabled
MDMWinsOverGP = 1
Result: Firewall stays disabled, GPO wins.
Is there another angle I can take here without getting 2000 devices back on premise or some more troubleshooting that may shed some light on this?
Microsoft Security | Intune | Other
4 answers
Sort by: Most helpful
-
-
 Rahul Jindal [MVP] 10,911 Reputation points MVP
Rahul Jindal [MVP] 10,911 Reputation points MVP2021-12-02T23:18:09.847+00:00 Is MDMWinsOverGP applying correctly? Have you checked in Device management event viewer log?
-
Convolute NZ 1 Reputation point
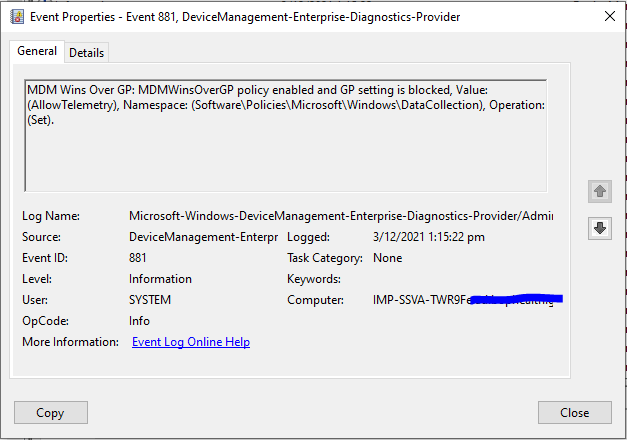
2021-12-03T00:22:19.31+00:00 Taken from the Event Viewer -> DeviceManagement-Enterprise-Diagnostics-Provider - I assume this is the log I am to check? As a side note, I haven't seen one reference to my firewall OMA-URI Firewall policy.
-
 Jason Sandys 31,411 Reputation points Microsoft Employee Moderator
Jason Sandys 31,411 Reputation points Microsoft Employee Moderator2021-12-07T17:01:10.807+00:00 This policy setting only applies to other settings within the Policy CSP. The settings you have above are not in the Policy CSP but are in the Firewall CSP and thus not affected by this policy.
I strongly discourage the use of the MDMWinsOverGPO setting. You should control settings using targeting and not an arbitration mechanism on the device; i.e., if a device should have a setting, don't target the device with the setting at all. This is fairly easy to do in group policy using WMI filtering, security/permissions, and OU assignment.