I am creating industrial demo (some sort of substation imitation) in Hyper-V on Azure server.
Host OS - Windows Server 2016.
Several guest VMs (mostly Windows7) are connected by internal only virtual switch - flat network, most MACs and all IPs configured manually.
One of VMs generate IEC 61850-8-1 GOOSE (generic object oriented substation event) traffic on one of its NICs and should receive it on another (different MAC\IP connected to same V-switch). In addition, I need this traffic to be received by other VMs.
GOOSE is multicast and this previosly never caused problems - all demo works well on other virtualization platforms. (But now I need it in Hyper-V on Azure.)
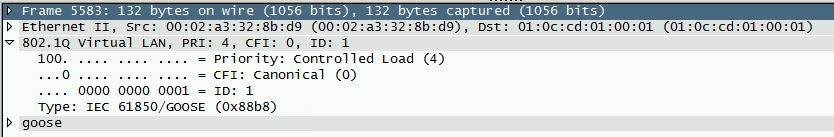
Also according to IEC 61850 standard all GOOSE packets are always tagged (by default with tag 0, but can be any other tag values) - this is used for prioritization in real switches.
The problem is that GOOSE does not reach the destination. Other unicast and multicast traffic from same NICs is OK, but not GOOSE.
With Wireshark I see GOOSE outgoing traffic on VM NICs, but no one VM in my network recieve this packets.
I assume that Hyper-V virtual switch for some reason drops tagged and at the same time multicast traffic.
I already some options and most of its combinations - nothing help:
- enabling MAC address spoofing
- changing NIC from standart Network Adapters to Legacy Network Adapters
- configuring VLANs on the V-switch
- switching VM NICs into trunk mode with Power Shell
- changing the GOOSE tag from default 0 to 1
Can someone explain how to solve this in Hyper-V and what could be the reason of GOOSE packets loss?