Hi
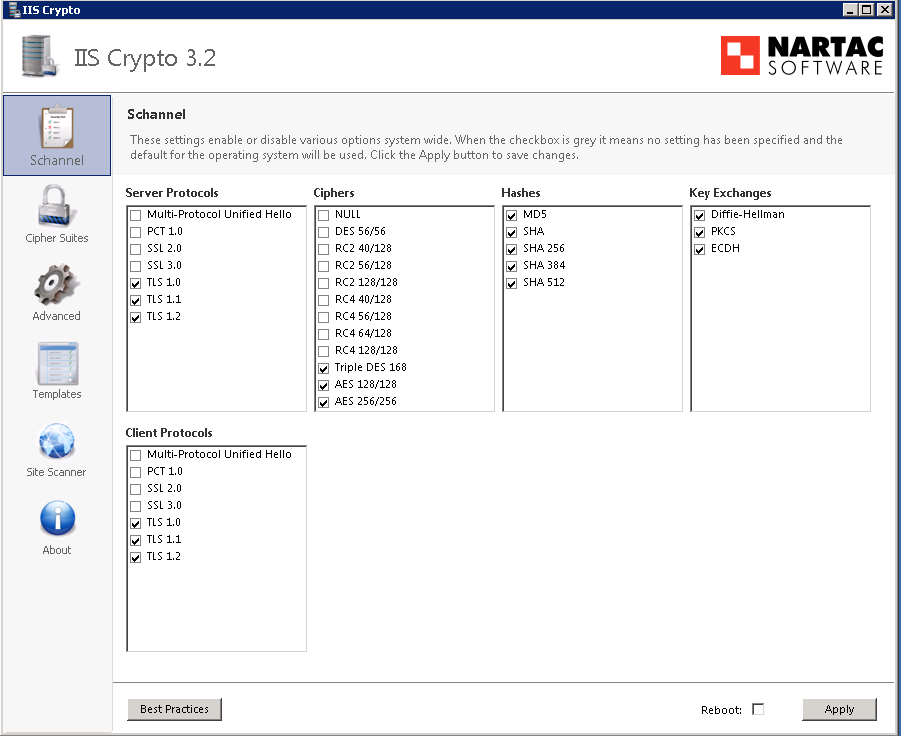
I have recently patched a SQL 2008 instance (On Windows Server 2008 R2) to 10.0.6556 which enabled TLS 1.2
When I try to connect from SSMS 18.1 it fails with
A connection was successfully established with the server, but then an error occurred during the login process. (provider: SSL Provider, error: 0 - An existing connection was forcibly closed by the remote host.) (.Net SqlClient Data Provider)
In the event viewer I see the following
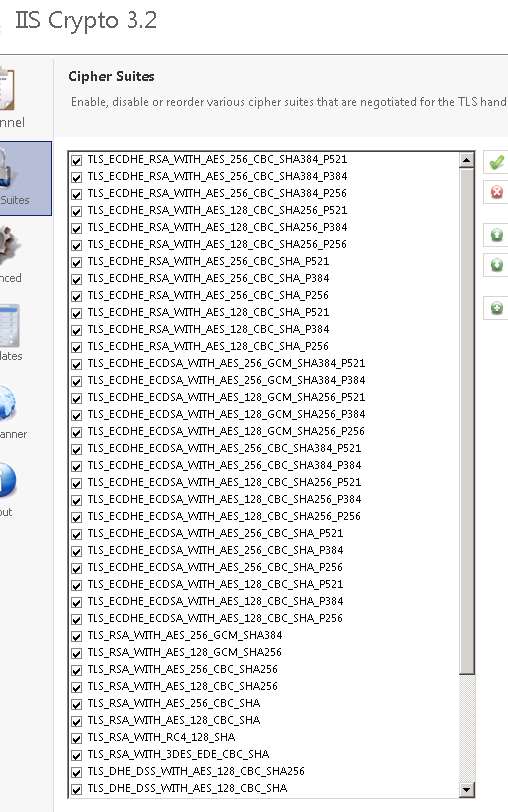
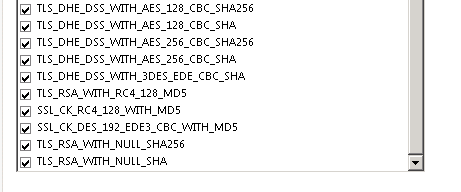
An TLS 1.2 connection request was received from a remote client application, but none of the cipher suites supported by the client application are supported by the server. The SSL connection request has failed.
Is there a quick fix for this? I have also patched a different Windows 2008 R2/SQL 2008 with the same CU update and it works fine.
I have tried most things I googled such as Windows patches or registry keys but it does not make a difference.
Some suggestions reference drivers or .net installations maybe?
Any help would be good.
Thanks
Sam