Hi @Art Singlaterry
Agree with Andy's suggestions, and below are some additional information for your reference as well:
You could try creating a mailflow rule on O365, if the message is sent from external and domain contains “yourdomain.com”, then reject the email or forward it to someone for approval. After setting the rule, observe if the SPAM mail occurs again.
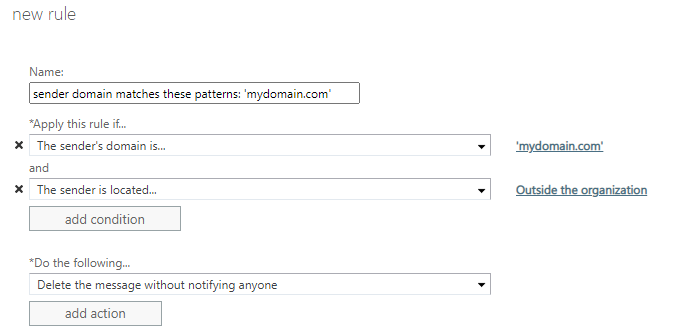
More details please see the link: Setting Up Domain Spoof Protection in Exchange 2013, Exchange 2016, or Microsoft 365
And a similar issue discussed here: Office365 email spoofed or MITM, it tells that the mails was spoofed since tehy are originating from a South Africa IP address.
We need to check the rules both on the workstation and OWA, also make sure MFA is enabled for your organization.
Please Note: Since the web site is not hosted by Microsoft, the link may change without notice. Microsoft does not guarantee the accuracy of this information.
If an Answer is helpful, please click "Accept Answer" and upvote it.
Note: Please follow the steps in our documentation to enable e-mail notifications if you want to receive the related email notification for this thread.


