Hello @Maksym Kharchenko2 ,
Welcome to Microsoft Q&A Platform. Thank you for reaching out & hope you are doing well.
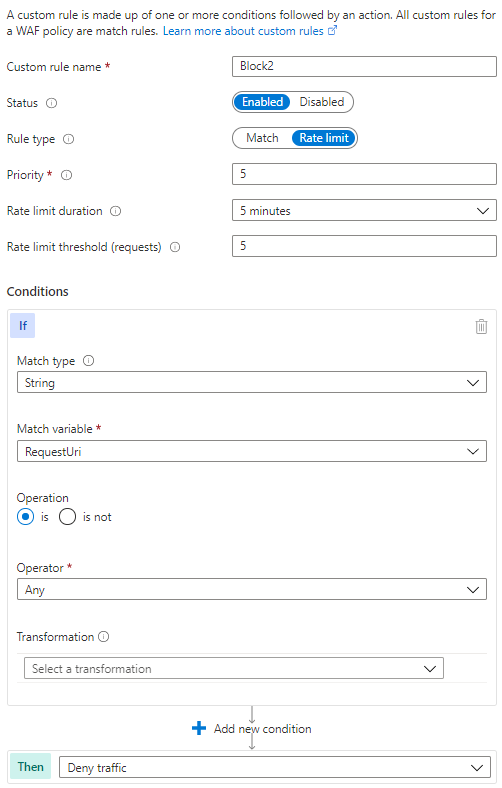
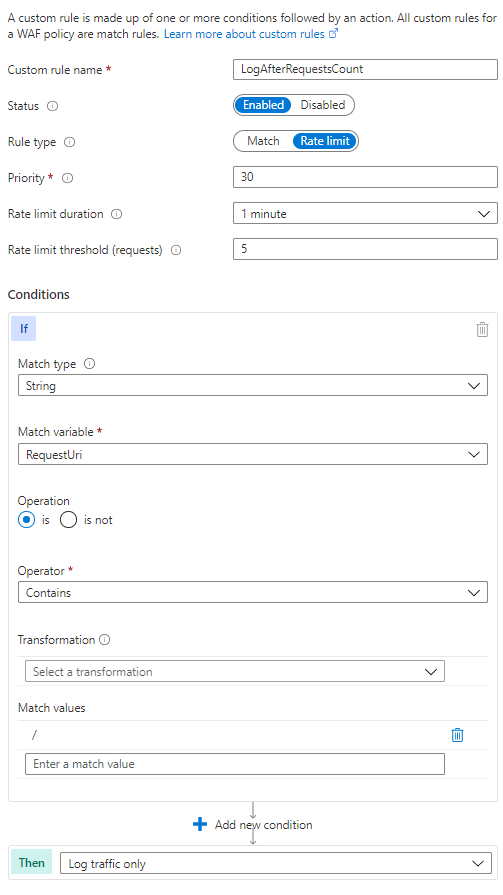
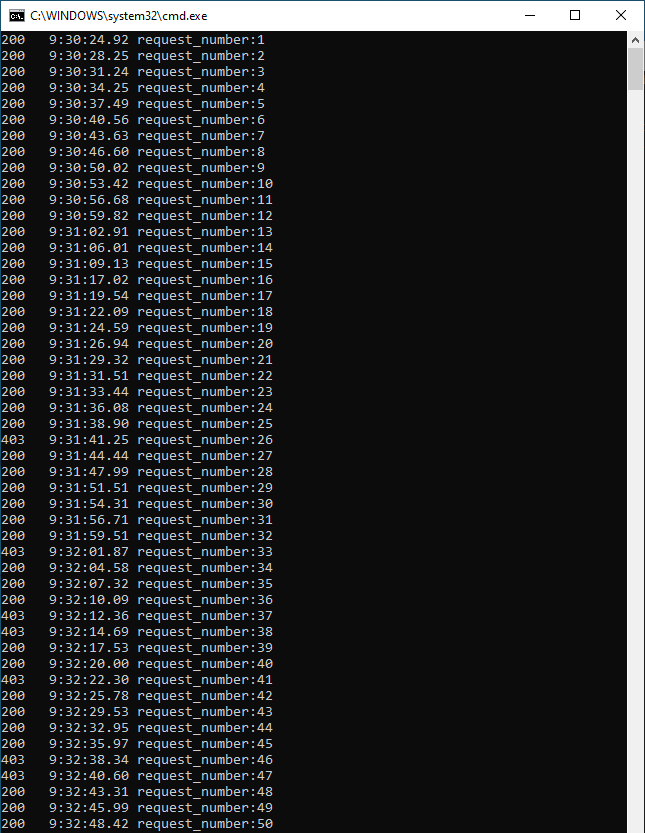
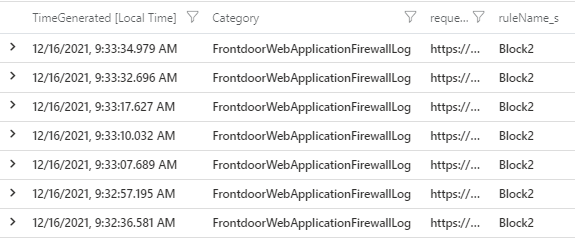
The rate limit feature is designed to filter attacks (DOS) and it's approximate by design. Putting a really low number (like 5 per minute) is not going to work well because the counting is done post-response (as well as the propagation within the environment). In other words, one particular server is never going to block the first request from a given Client IP address.
Our documentation also states this is intended for high traffic:
Rate limiting rules: A rate control rule is to limit abnormal high traffic from any client IP. You may configure a threshold on the number of web requests allowed from a client IP during a one-minute duration.
Refer : https://learn.microsoft.com/en-us/azure/web-application-firewall/afds/afds-overview
The system behaves this way because we are optimizing it for maximum performance (lowest latency and max throughput).
The rate limiting feature is optimized for DOS scenarios, so low thresholds may not start blocking traffic immediately once a client passes the threshold . An exact minimum threshold is not documented, but we generally recommend a setting it to a value of at least 30 or more (this is recommended by the WAF product group team). We have also requested them to update the documentation to include this information.
Could you try configuring the minimum threshold to 30 or more and try again?
Kindly let us know if the above helps or you need further assistance on this issue.
----------------------------------------------------------------------------------------------------------------
Please "Accept the answer" if the information helped you. This will help us and others in the community as well.