Hi,
It is not good idea to disable 389 on domain controller. Based on my experience , disable the LDAP protocole , can impact client and member server because netlogon service need the port 389 to communicate with domain controller . Also when you join a new machine to domain netlogon service will need this port.
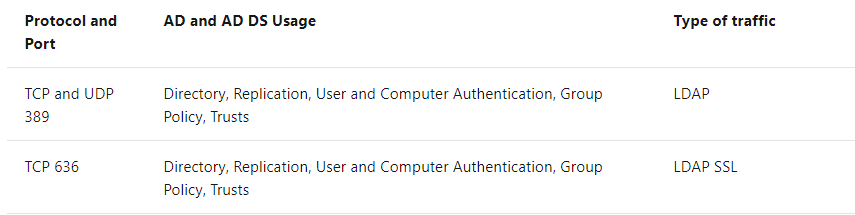
Below all required port for Netlogon service:
Application protocol Protocol Ports
NetBIOS Datagram Service UDP 138 ³
NetBIOS Name Resolution UDP 137 ³
NetBIOS Session Service TCP 139 ³
SMB TCP 445
LDAP UDP 389
RPC¹ TCP 135, random port number between 1024 - 65535
135, random port number between 49152 - 65535²
Blocking port 389 is a typical thing to do on an external firewall, but is not something you would do on a domain controller.
To get more details you can refer to the following links:
https://support.microsoft.com/en-us/help/832017/service-overview-and-network-port-requirements-for-windows
https://learn.microsoft.com/en-us/archive/blogs/pki/implementing-ldaps-ldap-over-ssl
Please don't forget to mark this reply as answer if it help you to fix your issue