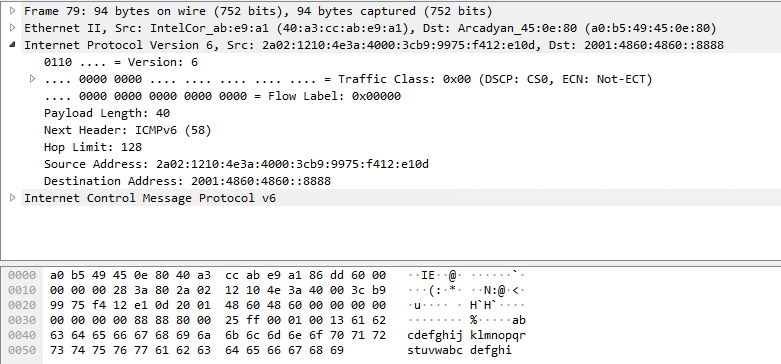
Hello @Steve Burns ,
You did not answer the question about 3rd party anti-virus/firewall software, but the pktmon output suggests that no such product is installed/active.
My next suggestion would have been to issue the commands pktmon start --capture --comp all --file-name ping.etl followed by ping -6 2001:4860:4860::8888, pktmon stop, pktmon etl2pcap ping.etl --out ping.pcapng and finally to analyse ping.pcapng with Wireshark.
If you have a copy of Microsoft Message Analyzer (MMA), there is no need to convert the .etl file to a .pcapng file.
The pktmon command captures data at each layer/filter in the network stack; in my test, the echo request is captured at 8 points in the stack and the echo reply at 10 points. When viewed with MMA a single ping looks like this:
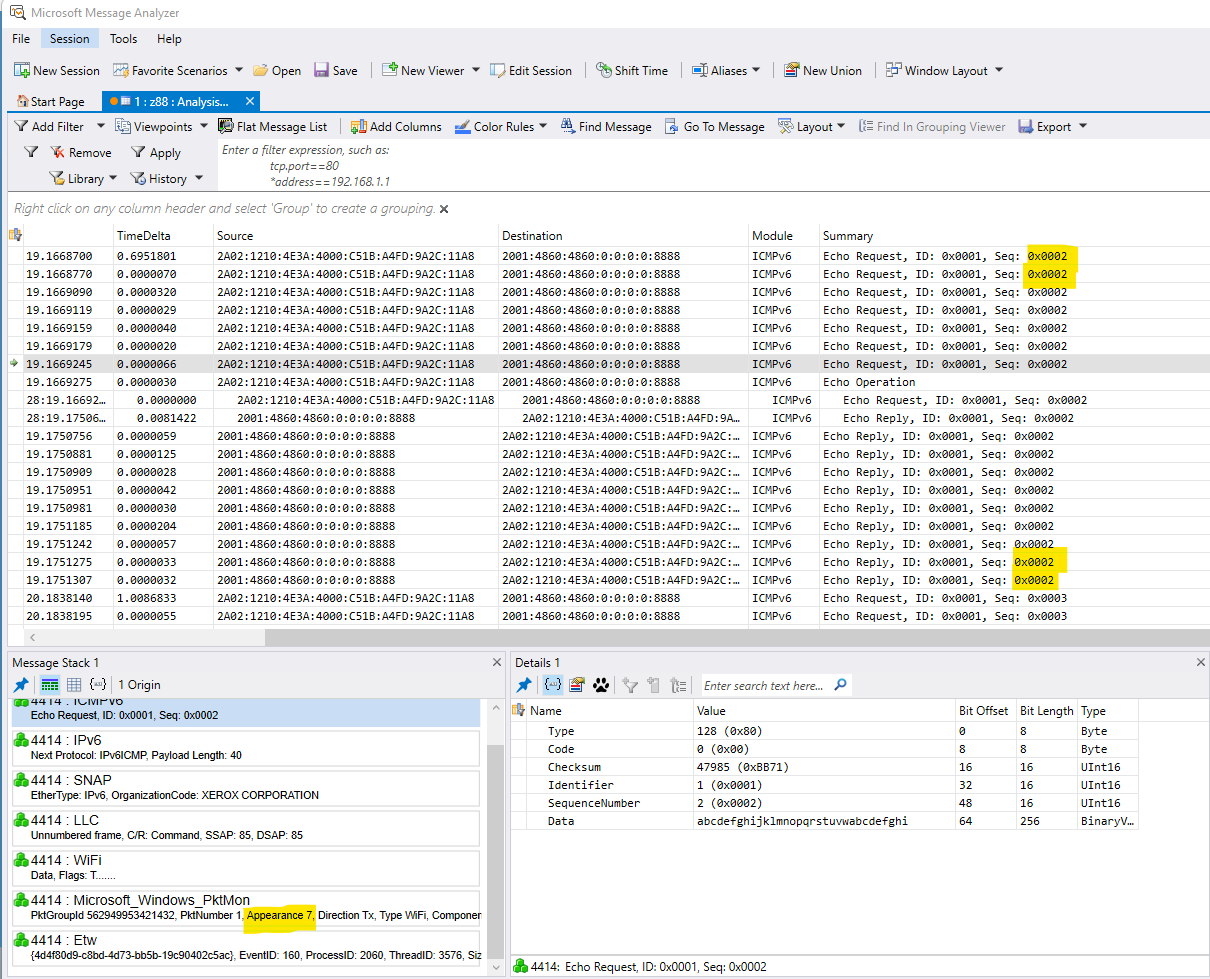
If the packet is being modified, this should show at which stage the modification occurs.
Unfortunately, when I use the etl2pcap conversion and view the .pcapng file with Wireshark, the display is more confusing:
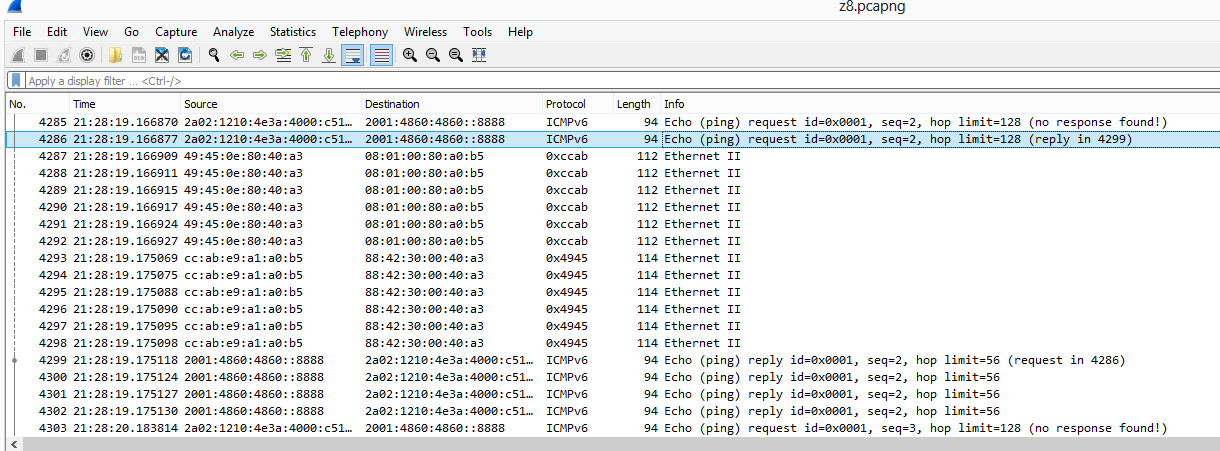
The problem is that the captured data at each level in the stack varies between a "generic" "Ethernet" style format (simple source, destination, protocol type header) and an actual data link header (802.11 wireless format in my example). Depending on your scenario (perhaps simple "Ethernet" format throughout), you may or may not encounter this problem.
In any event, I suggest that you try this and let us know your results.
Gary