When making a POST request with the following details:
URL:
https://login.microsoftonline.com/{my tenant id}/oauth2/v2.0/token
Headers:
Content-Type: application/x-www-form-urlencoded
Content-Length: XXX
Host: login.microsoftonline.com
Body (x-www-form-urlencoded):
username: my Azure admin email address
password: {my_password}
grant_type: password
scope: api://xxxxxxxx-xxxx-xxx-xxxx-xxxxxxxxxxxx/.default
client_id: {my_app_id}
response_type: token
client_secret: {my_app_secret}
tenant: {my_azure_tenant}
I'm receiving the Response:
{
"error": "invalid_grant",
"error_description": "AADSTS50034: The user account {EmailHidden} does not exist in the {azure_tenant} directory. To sign into this application, the account must be added to the directory.\r\nTrace ID: 23e024ac-9edf-44c6-b697-1892d5300900\r\nCorrelation ID: fd944f28-fce6-4ea2-9a80-1e96f15e26c5\r\nTimestamp: 2022-01-04 14:07:09Z",
"error_codes": [
50034
],
"timestamp": "2022-01-04 14:07:09Z",
"trace_id": "23e024ac-9edf-44c6-b697-1892d5300900",
"correlation_id": "fd944f28-fce6-4ea2-9a80-1e96f15e26c5",
"error_uri": "https://login.microsoftonline.com/error?code=50034"
}
However, upon trying to query the API for my UPN, by using:
https://graph.microsoft.com/beta/users?$select=userPrincipalName,onPremisesSamAccountName
I am getting the same email address as the UPN.
Therefore, I cannot proceed to making a proper request for receiving an auth token.
This auth token needs to be generated for usage in the Graph Exploer and in Postman, for modeling the API requests for our application.
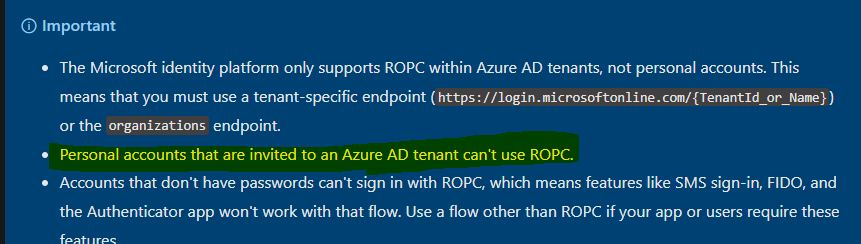
Perhaps the issue is that we don't yet have a verified domain in Azure. However, is this absolutely necessary in order to generate this auth token, so that we can use it to make app requests without requiring user login to our app?
What steps do we need to follow, in order to resolve this?