Hi all,
Server 2019, MECM 2017 based- environment.
Get the following error in the dmpdownloader.log.... all other functions (such as deployment, OSD, SUP etc) all working fine.
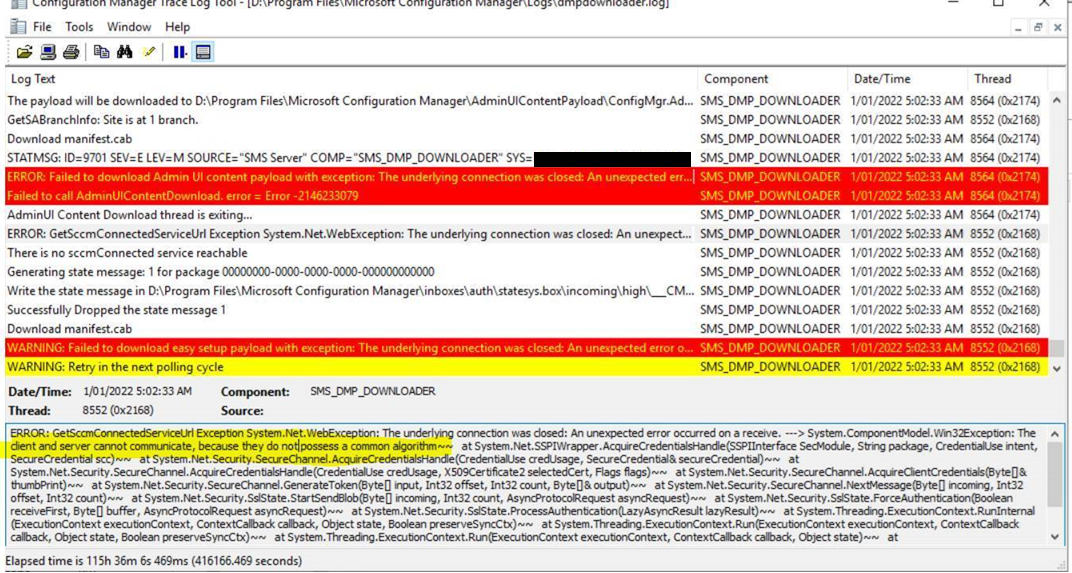
ciphers and older versions have been disabled using IIS crypto with the following settings:
<?xml version="1.0" encoding="utf-8"?>
<iisCryptoTemplate version="3">
<header>
<name>Best Practices</name>
<author>Nartac Software</author>
<lastUpdated>2021-09-22T05:44:40.022859Z</lastUpdated>
<description>This template sets your server to use the best practices for TLS. It aims to be compatible with as many browsers as possible while disabling weak protocols and cipher suites.</description>
<builtIn>false</builtIn>
</header>
<schannel>
<clientProtocols>
<templateItem name="Multi-Protocol Unified Hello" value="0" />
<templateItem name="PCT 1.0" value="0" />
<templateItem name="SSL 2.0" value="0" />
<templateItem name="SSL 3.0" value="0" />
<templateItem name="TLS 1.0" value="0" />
<templateItem name="TLS 1.1" value="-1" />
<templateItem name="TLS 1.2" value="-1" />
</clientProtocols>
<serverProtocols>
<templateItem name="Multi-Protocol Unified Hello" value="0" />
<templateItem name="PCT 1.0" value="0" />
<templateItem name="SSL 2.0" value="0" />
<templateItem name="SSL 3.0" value="0" />
<templateItem name="TLS 1.0" value="0" />
<templateItem name="TLS 1.1" value="-1" />
<templateItem name="TLS 1.2" value="-1" />
</serverProtocols>
<ciphers>
<templateItem name="NULL" value="0" />
<templateItem name="DES 56/56" value="0" />
<templateItem name="RC2 40/128" value="0" />
<templateItem name="RC2 56/128" value="0" />
<templateItem name="RC2 128/128" value="0" />
<templateItem name="RC4 40/128" value="0" />
<templateItem name="RC4 56/128" value="0" />
<templateItem name="RC4 64/128" value="0" />
<templateItem name="RC4 128/128" value="0" />
<templateItem name="Triple DES 168" value="-1" />
<templateItem name="AES 128/128" value="-1" />
<templateItem name="AES 256/256" value="-1" />
</ciphers>
<hashes>
<templateItem name="MD5" value="-1" />
<templateItem name="SHA" value="-1" />
<templateItem name="SHA 256" value="-1" />
<templateItem name="SHA 384" value="-1" />
<templateItem name="SHA 512" value="-1" />
</hashes>
<keyExchanges>
<templateItem name="Diffie-Hellman" value="-1" />
<templateItem name="PKCS" value="-1" />
<templateItem name="ECDH" value="-1" />
</keyExchanges>
</schannel>
<advanced>
<templateItem name="Override Enabled" value="0" />
<templateItem name="DHE Minimum Key Length" value="2048" />
<templateItem name="FIPS Algorithm Policy" value="0" />
</advanced>
<cipherSuites>
<templateItem name="Configured Cipher Suites" value="TLS_ECDHE_RSA_WITH_AES_256_GCM_SHA384,TLS_ECDHE_RSA_WITH_AES_128_GCM_SHA256,TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA384,TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA256,TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA,TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA,TLS_ECDHE_ECDSA_WITH_AES_256_GCM_SHA384,TLS_ECDHE_ECDSA_WITH_AES_128_GCM_SHA256,TLS_ECDHE_ECDSA_WITH_AES_256_CBC_SHA384,TLS_ECDHE_ECDSA_WITH_AES_128_CBC_SHA256,TLS_ECDHE_ECDSA_WITH_AES_256_CBC_SHA,TLS_ECDHE_ECDSA_WITH_AES_128_CBC_SHA,TLS_RSA_WITH_AES_256_GCM_SHA384,TLS_RSA_WITH_AES_128_GCM_SHA256,TLS_RSA_WITH_AES_256_CBC_SHA256,TLS_RSA_WITH_AES_128_CBC_SHA256,TLS_RSA_WITH_AES_256_CBC_SHA,TLS_RSA_WITH_AES_128_CBC_SHA" minimumOSVersion="Windows2016" />
</cipherSuites>
</iisCryptoTemplate>
Once the IISCrypto settings are set back to default - the error goes away.
Given that "everything else" seems to work - it seems strange that this one service would use an older TLS version or cipher suite.