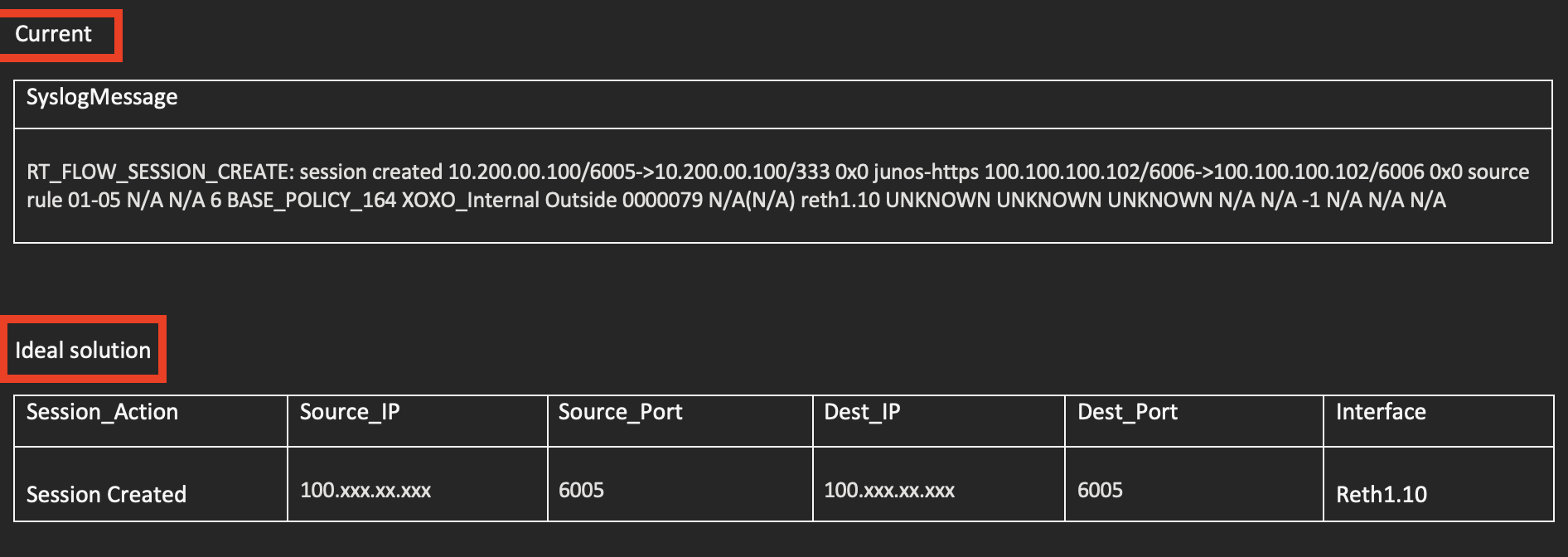
The format of the Syslog message will vary by device vendor. The built-in alert rules and workbooks will parse this data as needed.
For your own hunting a Syslog parser usually begins by filtering out messages from a specific vendor. Then a series or parse() or split() operations are used to break the message down into more useful columns. These queries are typically saved as a user KQL function for easier reuse.
You might try checking the Sentinel GitHub repo for parser examples. There are also several analytic rules that have good Syslog parser examples.
I also recommend looking into the Sentinel ASIM project. This is an effort to improve Sentinel data normalization. Initially the project has produced several functions than can be used in the place of a table to render parsed tables. https://learn.microsoft.com/en-us/azure/sentinel/normalization