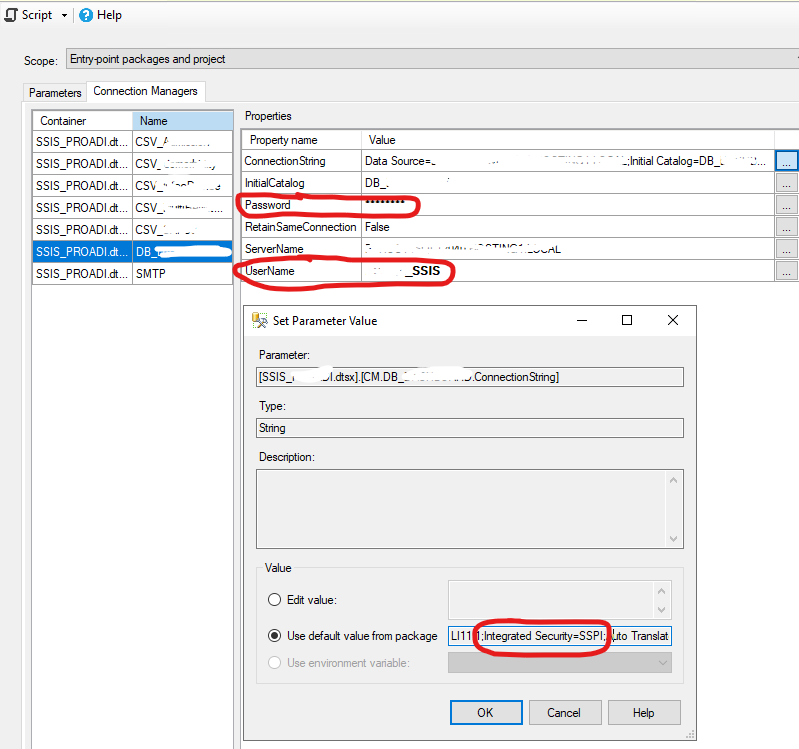
An OLE DB record is available. Source: "Microsoft SQL Server Native Client 11.0" Hresult: 0x80040E4D Description: "Login failed for user 'domain\hostname$'.".
This happens because SQL Server Agent runs under an account local to the machine, for instance NT Service\SQLSERVERAGENT, and you are using integrated security. Since that account does not exist on the other machine, the login will be for the machine account.. (The one with $ at the end.) Normally, you don't create logins for machine accounts.
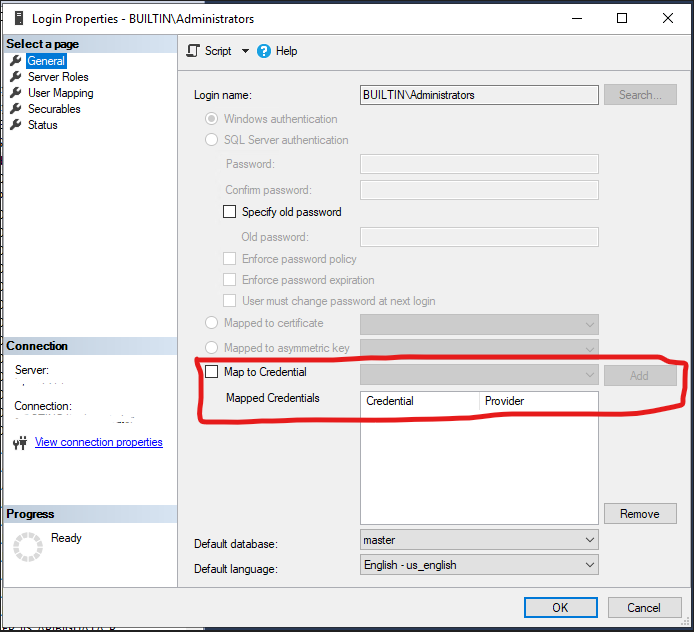
When you set up proxy accounts with Agent, that is a typically a Windows domain account, so that Agent spawns a subprocess with that account, logging on to Windows with the stored credentials. Because this is a true Windows login, that process can now successfully log in with Integrated Security. I describe the steps to do this here: https://www.sommarskog.se/perm-hijack.html#agentjobs.
Now, you are talking about a proxy using SA, which is an SQL login, so I am not sure we are talking about the same thing. I will need to add the caveat that I don't know SSIS, so if this is a proxy specific to SSIS, there maybe something I have missed.
Nevertheless, I like to answer your doubts:
1 - Why do we need to use the (SA) account?
You would need to use SA, only if the package needs to perform actions that requires membership in the sysadmin role.
I did not watch the video, as it was a tad long for me. But I sampled a few seconds some minutes into the presentation, and I noticed that the presenter talked about using sa. Maybe he used sa as an example to keep things simple? (Not a very good idea in my opinion.)
2 - Can you do the mapping using an unprivileged account?
Of course.
3 - If privileges are needed, which ones are needed?
That depends on what the package is doing. Access to the database in question seems obvious. SELECT, INSERT etc permissions on tables may. Or only permissions to run stored procedures.