Hello @Enes Sahin ,
Thanks for reaching out.
Your application can use keys for signing and encryption to keep the key management external from your application. Key Vault supports RSA and EC keys also supports Managed HSM RSA, EC, and symmetric keys.
You could use APIs and SDKs to interact with Azure key vault as explained here. The ENCRYPT and DECRYPT operation encrypts & decrypts a well-formed block of ciphertext using the target encryption key and specified algorithm.
Please find following examples for your reference:
https://learn.microsoft.com/en-us/rest/api/keyvault/keys/decrypt/decrypt#examples
https://learn.microsoft.com/en-us/rest/api/keyvault/keys/encrypt/encrypt#examples
ENCRYPT :
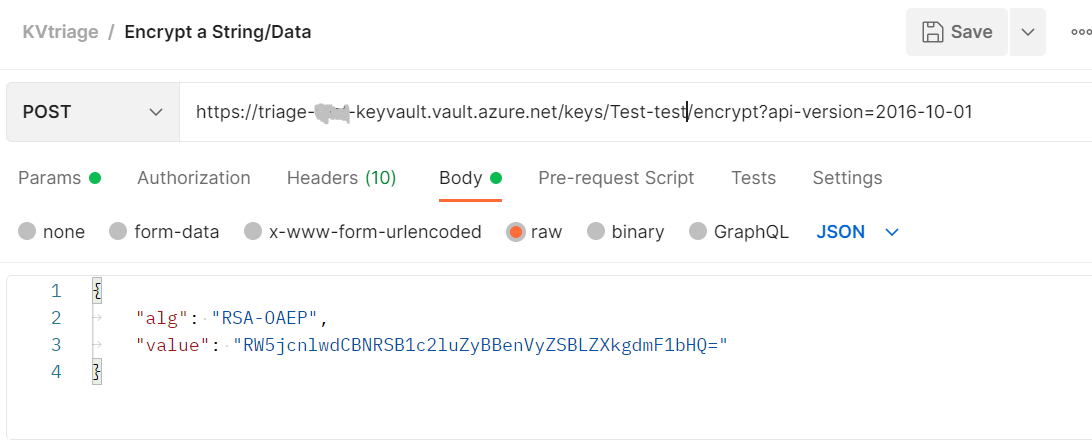
DECRYPT :
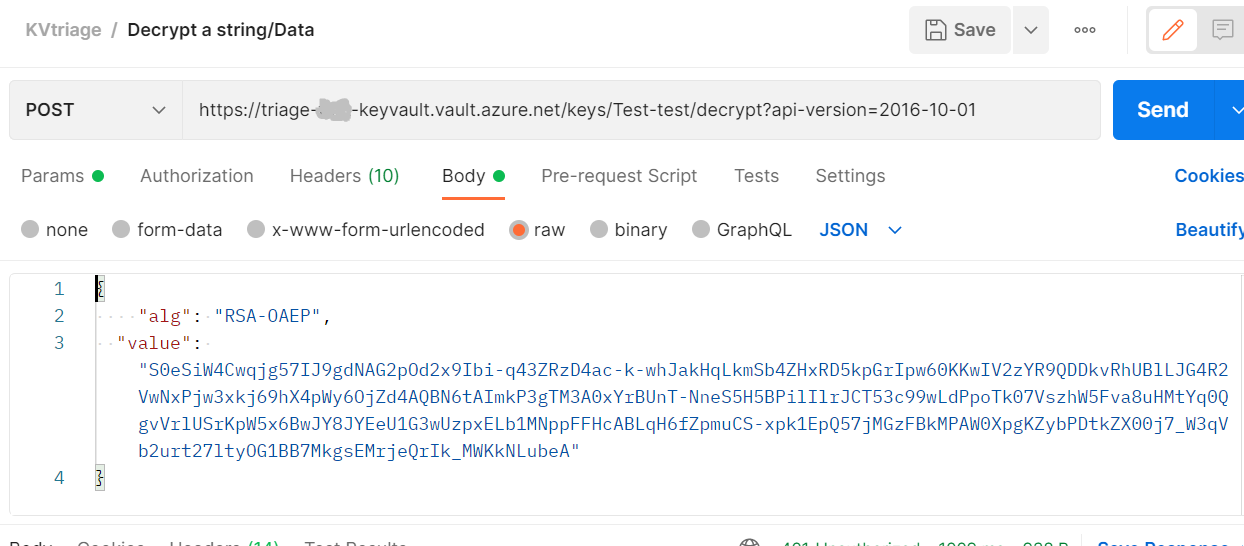
For more information, see About keys and Azure Key Vault developer's guide.
-----
Please "Accept the answer" if the information helped you. This will help us and others in the community as well.
