@Anonymous Using the pod identity project enables authentication against supporting Azure services. For your own services or applications without managed identities for Azure resources, you can still authenticate using credentials or keys. Key vault can be used to store these secret contents.
When applications need a credential, they communicate with the digital vault, retrieve the latest secret contents, and then connect to the required service. The simplified workflow for retrieving a credential from Azure Key Vault using pod managed identities is shown in the following diagram:
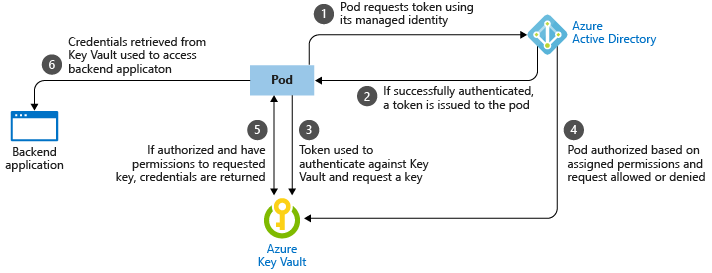
With Key Vault, you store and regularly rotate secrets such as credentials, storage account keys, or certificates. You can integrate Azure Key Vault with an AKS cluster using the Azure Key Vault provider for the Secrets Store CSI Driver. The Secrets Store CSI driver enables the AKS cluster to natively retrieve secret contents from Key Vault and securely provide them only to the requesting pod. You can use a pod managed identity to request access to Key Vault and retrieve the secret contents needed through the Secrets Store CSI Driver.
You can read more about it here.
Your application can directly access the Secrets via Application since Managed Identity enable the application to have required access.
Fetching secret from Keyvault is dynamic process so whever you update secret it will be updated in mounted volume.
Hope it helps!!!
Please 'Accept as answer' if it helped, so that it can help others in the community looking for help on similar topics

