@Jake Bloomfield , Apologies for the delay on this. I checked on this and found that this can occur if you do not have "Azure Multi-Factor Auth Client" application registered within your tenant . This is a first party application provided from Microsoft but sometime due to transient issues it may not be present in a tenant . In order to check the same , you can use the following powershell cmdlet .
Connect-MsolService
Get-MsolServicePrincipal -AppPrincipalId 981f26a1-7f43-403b-a875-f8b09b8cd720
Or you can check the same from the portal as shown in the picture.
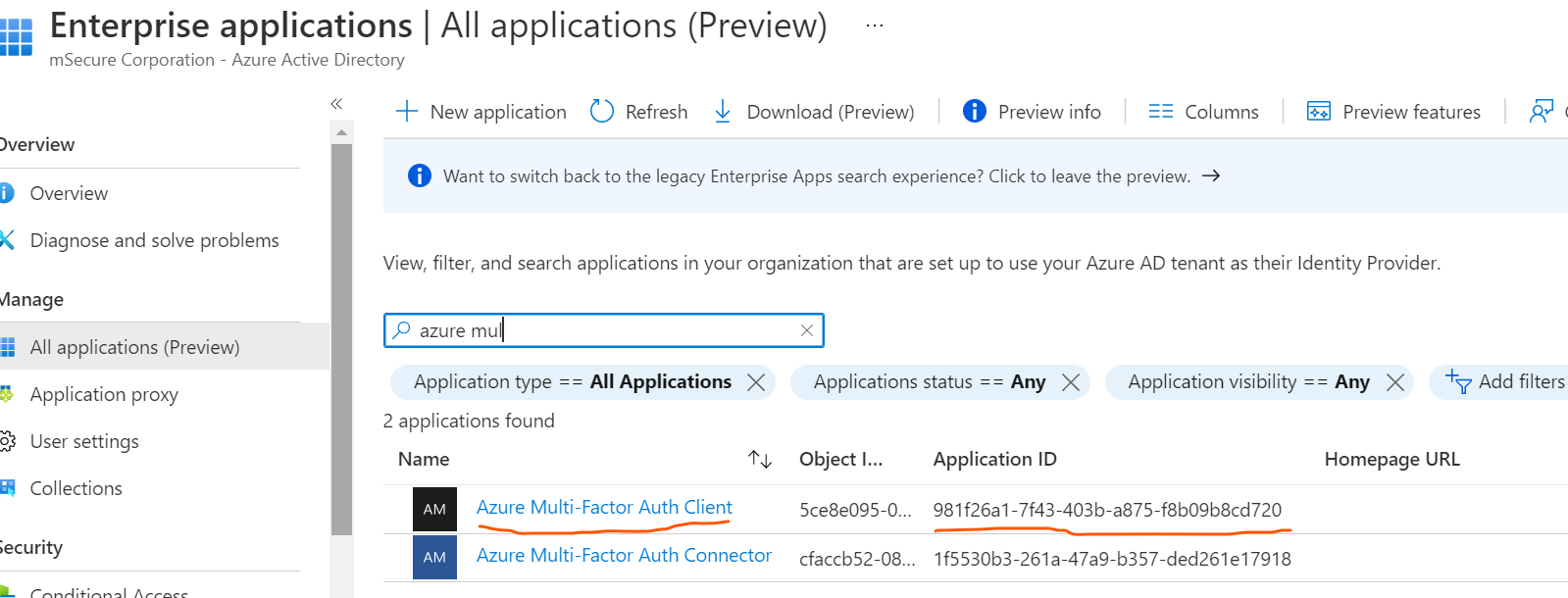
Go to https://aad.portal.azure.com > "Enterprise Applications" > Search for "Azure Multi-Factor Auth Client" > Check properties for this app > Confirm if the service principal is enabled or disabled > Click on the application entry > Go to Properties of the app > If the option "Enabled for users to sign-in? is set to No in Properties of this app , please set it to Yes.
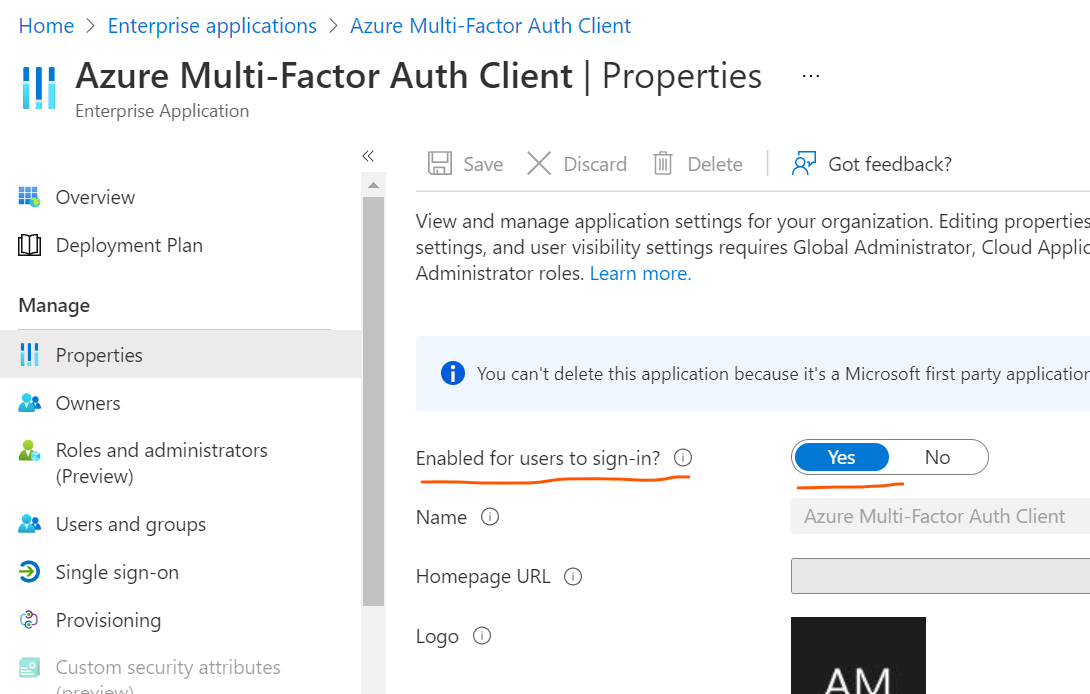
If this app is not present , Please try to run the following cmdlet using a global admin credentials on the Azure AD powershell prompt .
Connect-MsolService
New-msolServicePrincipal -AppPrincipalId 981f26a1-7f43-403b-a875-f8b09b8cd720 -DisplayName "Azure Multi-Factor Auth Client"
Now run \AzureMfaNpsExtnConfigSetup.ps1 .
This should work.
Regards,
Shashi
 so that it can be beneficial to others in the community searching for similar solutions.
so that it can be beneficial to others in the community searching for similar solutions.