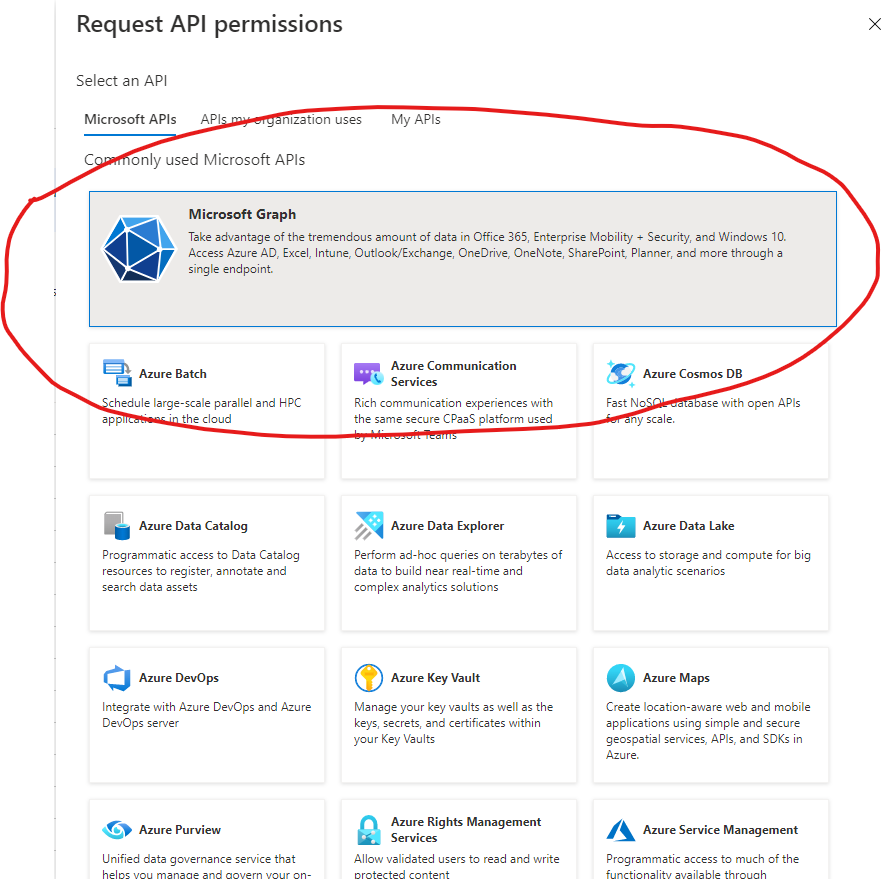
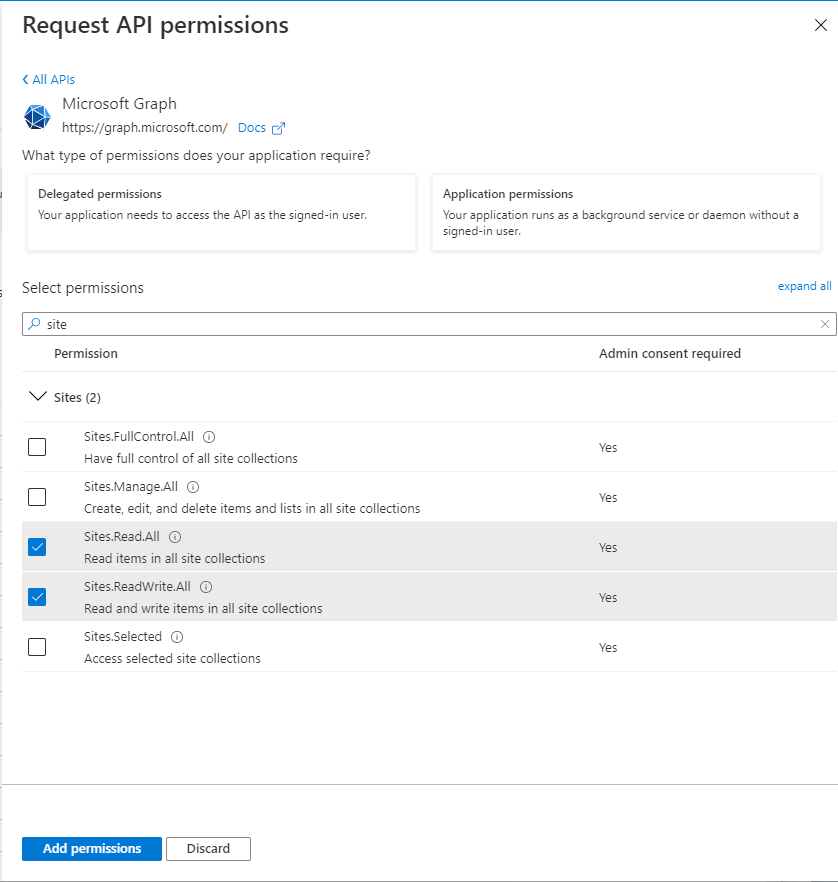
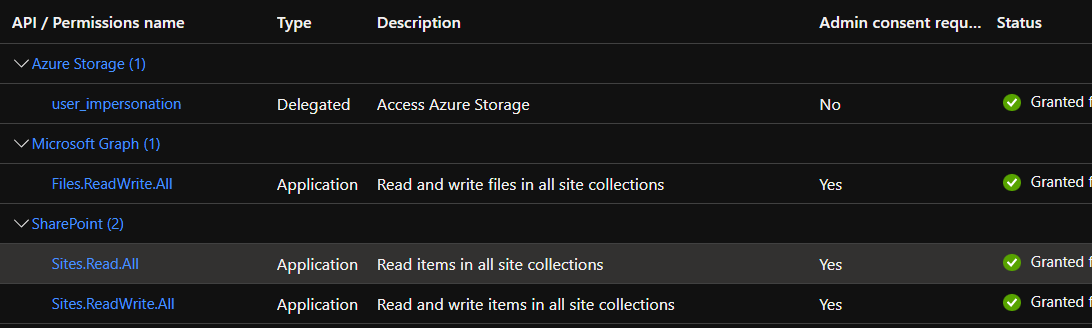
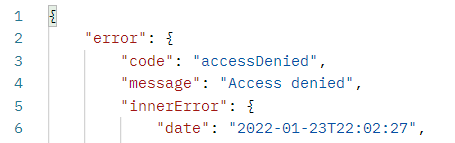
Hi @Shuzmm ,
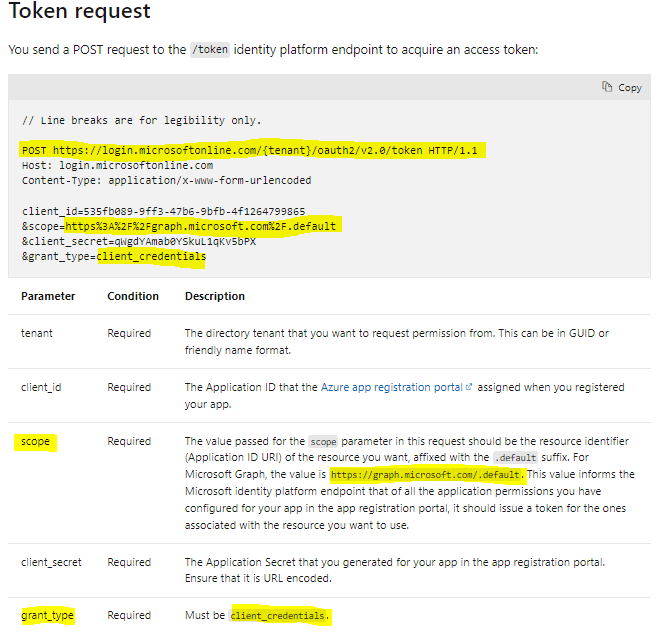
Thanks for your clarification in the comments section. You can consider using OAuth 2.0 client credentials grant flow to acquire the application access token. As mentioned in this documentation, In the OAuth 2.0 client credentials grant flow, you use the Application ID and Application Secret values that you saved when you registered your app to request an access token directly from the Microsoft identity platform /token endpoint.
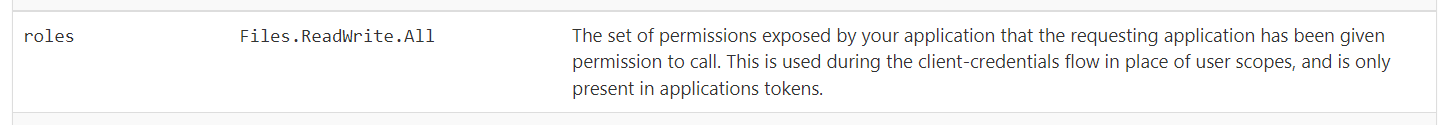
The value passed for the scope parameter in this request should be the resource identifier (Application ID URI) of the resource you want, affixed with the .default suffix. For Microsoft Graph, the value is https://graph.microsoft.com/.default. This value informs the Microsoft identity platform endpoint that of all the application permissions you have configured for your app in the app registration portal, it should issue a token for the ones associated with the resource you want to use.
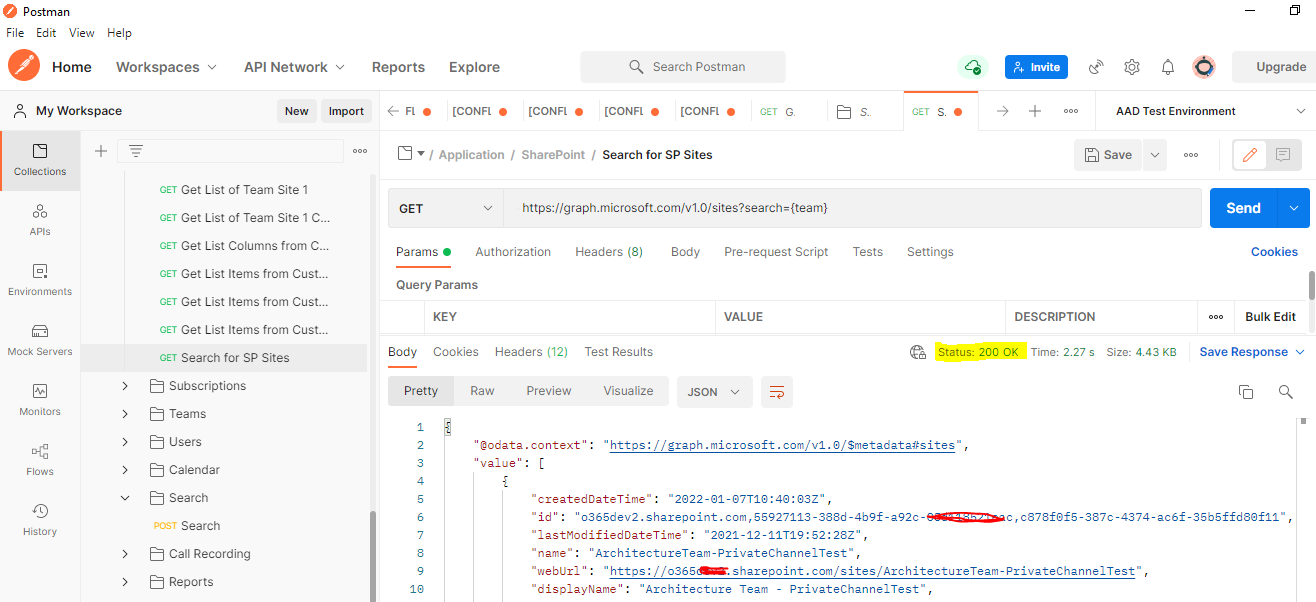
You can also consider using Postman API tool for API endpoint testing such as getting the application access token and runing the various microsoft API queries.
Please refer this documentation for more information on this :
https://learn.microsoft.com/en-us/graph/auth-v2-service?view=graph-rest-1.0
https://learn.microsoft.com/en-us/azure/active-directory/develop/v2-oauth2-client-creds-grant-flow
Hope this helps.
If the answer is helpful, please click "Accept Answer" and kindly upvote it ,so that it will be helpful to the other community users. If you have any further questions about this answer, please click "Comment".