One option may be to move roles off, demote, reboot, promo the problematic one again.
--please don't forget to upvote and Accept as answer if the reply is helpful--
This browser is no longer supported.
Upgrade to Microsoft Edge to take advantage of the latest features, security updates, and technical support.
Hi.
Customer has an environment with an AD forest consisting of root and child domain, each has 2 DCs.
Both DCs in the child domain (but not those in the root) contain KDC errors claiming there's a duplicate SPN of cifs\dc1.<rootNS> for a domain controller in the root domain.
Exact error:
The KDC encountered duplicate names while processing a Kerberos authentication request. The duplicate name is cifs/dc1.<rootNS> (of type DS_SERVICE_PRINCIPAL_NAME). This may result in authentication failures or downgrades to NTLM. In order to prevent this from occurring remove the duplicate entries for cifs/dc1.<rootNS> in Active Directory.
However, I haven't been able to find any duplicates using:
As a note, none of the DCs actually have a cifs/ SPN registered, which makes it even more confusing.
Furthermore, as stated above, setspn -X doesn't show any duplicates in either domains, but a forest-wide search using setspn -X -F finds number of duplicate SPNs for the problematic DC (but only when running the search from the child domain), however none of them are cifs/.
Here's the list:
Operation will be performed forestwide, it might take a while.
Processing entry 0
HOST/dc1.<rootNS> is registered on these accounts:
CN=dc1\0ACNF:481721ed-bfa1-4146-a190-1a279501cab6,CN=Computers,dc=rootdomain,dc=local
CN=dc1,OU=Domain Controllers,dc=rootdomain,dc=localHOST/dc1 is registered on these accounts:
CN=dc1\0ACNF:481721ed-bfa1-4146-a190-1a279501cab6,CN=Computers,dc=rootdomain,dc=local
CN=dc1,OU=Domain Controllers,dc=rootdomain,dc=localRestrictedKrbHost/dc1 is registered on these accounts:
CN=dc1\0ACNF:481721ed-bfa1-4146-a190-1a279501cab6,CN=Computers,dc=rootdomain,dc=local
CN=dc1,OU=Domain Controllers,dc=rootdomain,dc=localTERMSRV/dc1 is registered on these accounts:
CN=dc1\0ACNF:481721ed-bfa1-4146-a190-1a279501cab6,CN=Computers,dc=rootdomain,dc=local
CN=dc1,OU=Domain Controllers,dc=rootdomain,dc=localRestrictedKrbHost/dc1.<rootNS> is registered on these accounts:
CN=dc1\0ACNF:481721ed-bfa1-4146-a190-1a279501cab6,CN=Computers,dc=rootdomain,dc=local
CN=dc1,OU=Domain Controllers,dc=rootdomain,dc=localTERMSRV/dc1.<rootNS> is registered on these accounts:
CN=dc1\0ACNF:481721ed-bfa1-4146-a190-1a279501cab6,CN=Computers,dc=rootdomain,dc=local
CN=dc1,OU=Domain Controllers,dc=rootdomain,dc=local
So, eventlog complains about non-existent SPN, domain-wide search finds no duplicates, forest-wide does, the object (account), which the duplicate references (the renamed CNF object), doesn't exist.
Any ideas?
One option may be to move roles off, demote, reboot, promo the problematic one again.
--please don't forget to upvote and Accept as answer if the reply is helpful--

Hi @MarkosP
The reason you are not seeing an CIFS SPN entry is because there are a number of common SPN services that are mapped back to the host SPN entry. The services that are mapped back to the host SPN is defined by the sPNMappings attribute of the CN=Directory Service,CN=Windows NT,CN=Services,DC=<domain> object.
This the default list of services that are defined in the sPMMappings attribute and are mapped back to host SPN: alerter,appmgmt,cisvc,clipsrv,browser,dhcp,dnscache,replicator,eventlog,eventsystem,policyagent,oakley,dmserver,dns,mcsvc,fax,msiserver,ias,messenger,netlogon,netman,netdde,netddedsm,nmagent,plugplay,protectedstorage,rasman,rpclocator,rpc,rpcss,remoteaccess,rsvp,samss,scardsvr,scesrv,seclogon,scm,dcom,cifs,spooler,snmp,schedule,tapisrv,trksvr,trkwks,ups,time,wins,www,http,w3svc,iisadmin,msdtc
In your case, I would check if the HOST/dc1 SPN has been registered against multiple computer accounts using the GC with a search from the forest root down. NetTools does provide the SPN option to do this search and list which accounts the SPN has been assigned.
The other thing of note is that you have a Conflict object for dc01 in your root domain, these are caused when the same object is created at the same time on two different DCs and then causes a conflict object to be created when the DC replicate, as the DCs don't know which one is meant to be master, so it keeps a copy as a conflict object. I would look to clean up these objects as they may be causing your problem. If you can confirm that there has been no updates to this object since it was created, it would be safe to delete the object. If you are a little nervous about deleting it, I would suggest that you clear the serviceprincipalname attribute to see if it fixes your problem.
Gary.

Hi @MarkosP
If the issue is only occurring in the child domain and you have multiple DCs in the domain, you could remove the GC, wait 60 mins, and then reboot the DC, then re-enable the GC, repeat on each DC in turn, this will force the GC partition to be resynced from the root domain.
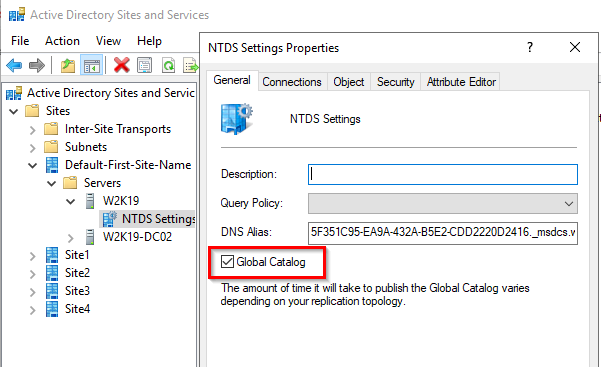
Gary.
Thanks, I'll try the idea with removing/adding GC.
I've tried dumping the database per the article and only put "serviceprincipalname" (without the quotes) in the attributes field, but it didn't work - I clicked the Go button, but it didn't generate any ntds.dmp in the NTDS folder (or elsewhere).
As for the selective search ... did you mean something like Get-ADObject -LDAPFilter "(serviceprincipalname=host/dc1*)" -SearchBase 'dc=rootdomain,dc=local' -SearchScope Subtree ? That still returns only the correct DC object.