Hello @tim yang ,
Thank you for posting here.
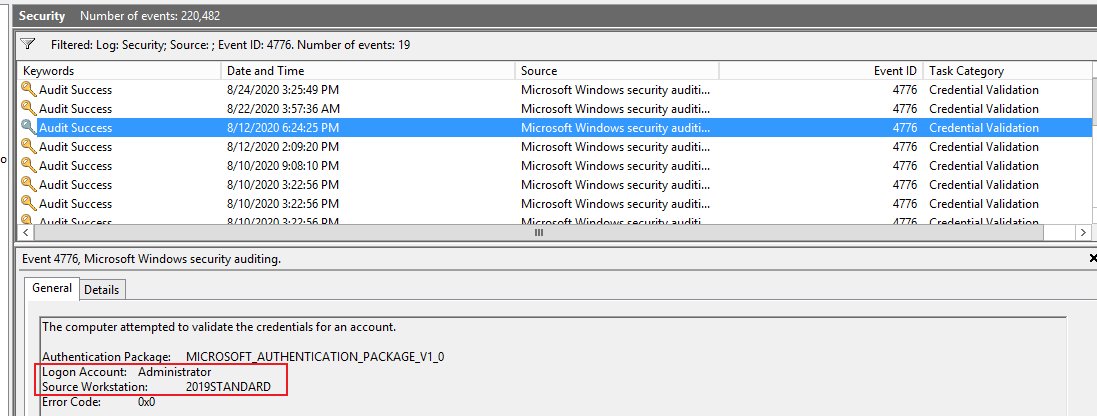
Based on the description "if i only have computer name or ip address in AD , how can i the username which i logon this computer", do you mean if i only have computer name or ip address in AD , how can i find the username which i logon this computer? If so, what logon type do you want to find?
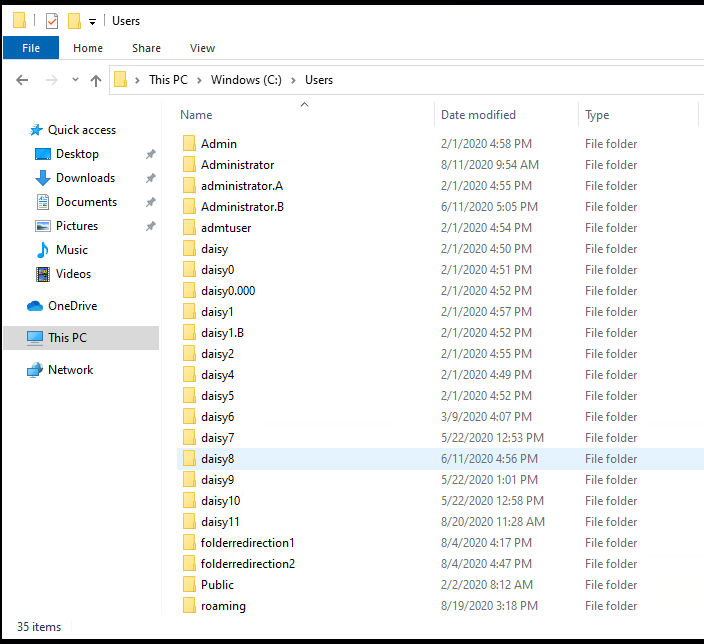
1. If we want to find logon type 2 (Interactive Local interactive login. The most common way to log in.), we can logon this computer with one account (domain user account or domain Administrator account, local account or local Administrator account), then check the user profile in C:\Users.
For example:
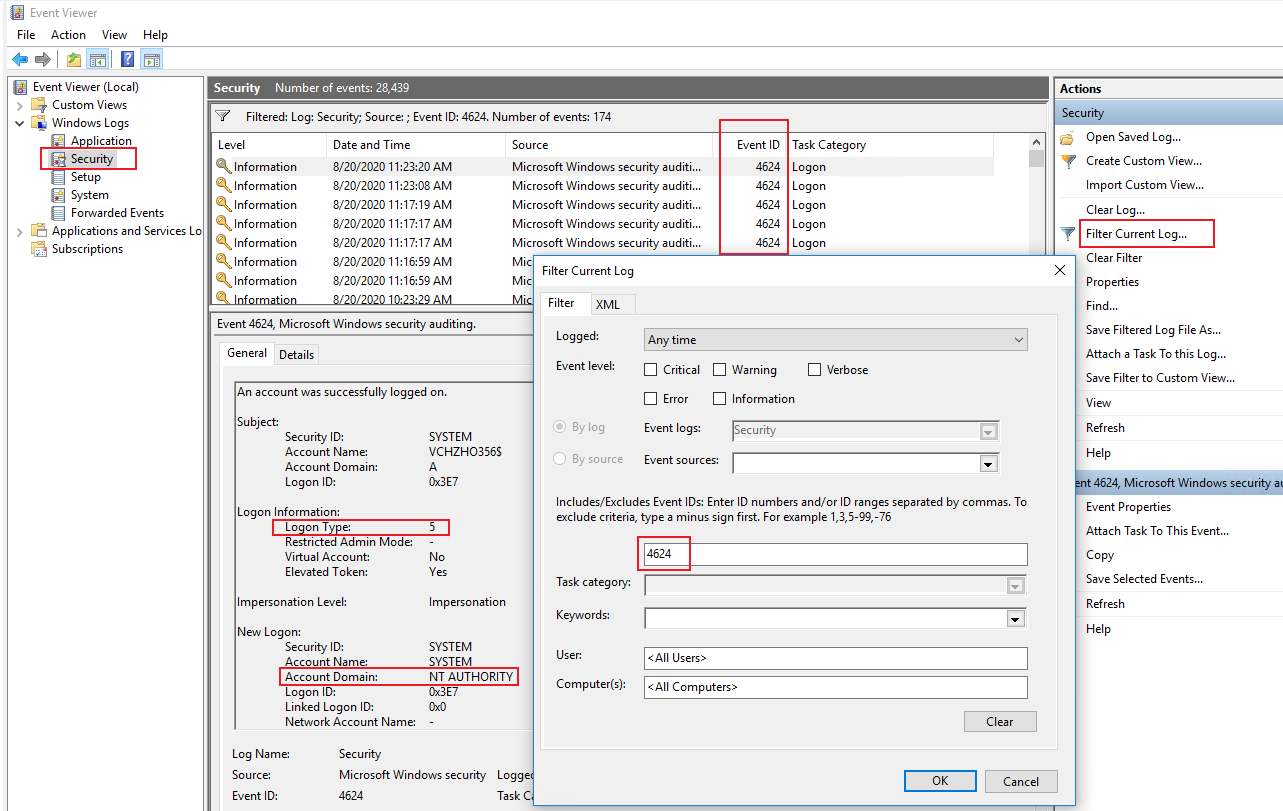
2. If we want to find different logon types, we can logon this computer with Administrator account, then check the Security log under
Event Viewer\Windows Logs\Security.
We can see many Event ID 4624 (including different kinds of logon type).
For example:
For event ID 4624, we can refer to the link below.
4624(S): An account was successfully logged on.
(I am sorry, I was denied to put the corresponding link, we can search the title I mentioned to see the link if needed.)
For logon type, we can refer to the link below.
Audit logon events
(I am sorry, I was denied to put the corresponding link, we can search the title I mentioned to see the link if needed.)
Hope the information is helpful. If anything is unclear, please feel free to let us know.
Best Regards,
Daisy Zhou