Hi, we have an old Azure AD Connect v.1.6.16.0 server (upgraded from DirSync) which we are trying to migrate to a new v.2.0.91.0 server using the swing method. I've been able to export the old config using the wizard and import it onto the new server fine. We've opted to use the same AD DS MSOL_**** and Azure AD Svc accounts, since they already have the necessary permissions in place. The new system is still is staging mode but it passes a full sync without any errors so both re-used connector accounts appear to be authing ok.
The issue Im having is configuring device writeback, something which is enabled on the old server and has not been brought across in the export. To enable on the new server Im using the GUI, Configure device options > Connect to Azure AD > select to Configure device writeback > upon selecting our Device writeback forest Im immediately shown the following error-
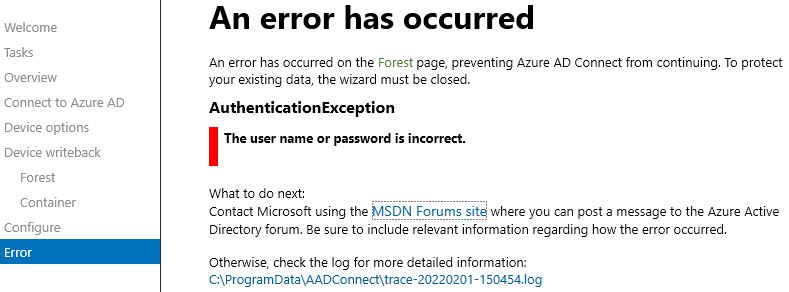
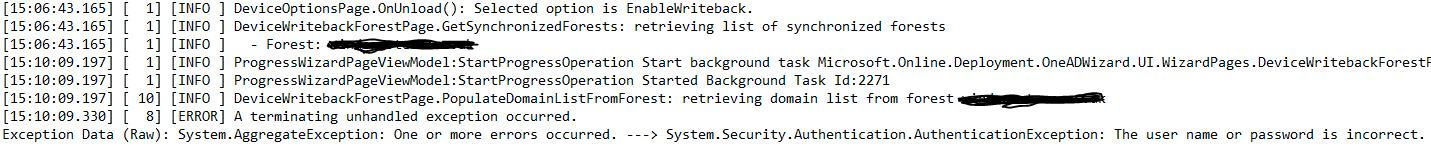
Looking in the log it's trying to retrieve the domain list from our forest (single domain) and then terminates.
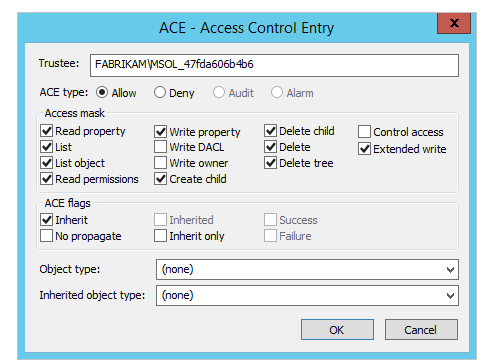
The log doesnt specify the account its tying to use but Im assuming its the AD DS MSOL_**** account which already has the necessary rights to the 'Device Registration Configuration' and 'RegisteredDevices' containers in AD. However, to make sure its not a permissions issue for that account Ive also tried adding it into domain admins and enterprise admins and re-running the process with the same result. I've checked our AD DS and there is only one MSOL_**** account, so its not a duplicate account issue, plus we only have one domain.
Im toying with either rolling back the server and doing an AD Connect re-install and using new creds for MSOL, or perhaps running the 'Initialize-ADSyncDeviceWriteBack' powershell script against the new server in the hopes it will fix it. Problem is I didnt do the install for our old DirSync/ADConnect environment so Im trying to fix this without breaking anything in the process :-) Any advice welcome.
Many thanks.