I've had difficulty finding instructions or a step-by-step guide on how to configure an NPS server to work with anonymous identities when using PEAP authentication. I can find plenty of information on how to configure a client, but not the actual server side of things.
The only information I've been able to locate so far is at https://learn.microsoft.com/en-us/previous-versions/windows/it-pro/windows-server-2008-r2-and-2008/ff919512(v=ws.10) which states:
The NPS policy for 802.1X Wireless must be created by using NPS Connection Request Policy. If the NPS policy is created in by using NPS Network Policy, then identity privacy will not work.
Note
EAP identity privacy is provided by certain EAP methods where an empty or an anonymous identity (different from the actual identity) is sent in response to the EAP identity request. PEAP sends the identity twice during the authentication. In the first phase, the identity is sent in plain text and this identity is used for routing purposes, not for client authentication. The real identity – used for authentication - is sent during the second phase of the authentication, within the secure tunnel that is established in the first phase. If Enable Identity Privacy checkbox is selected, the username is replaced with the entry specified in the textbox. For example, assume Enable Identity Privacy is selected and the identity privacy alias anonymous is specified in the textbox. For a user with a real identity alias jdoe@ssss .com, the identity sent in first phase of authentication will be changed to anonymous@ssss .com. The realm portion of the 1st phase identity is not modified as it is used for routing purposes.
I currently have a single Connection Request policy
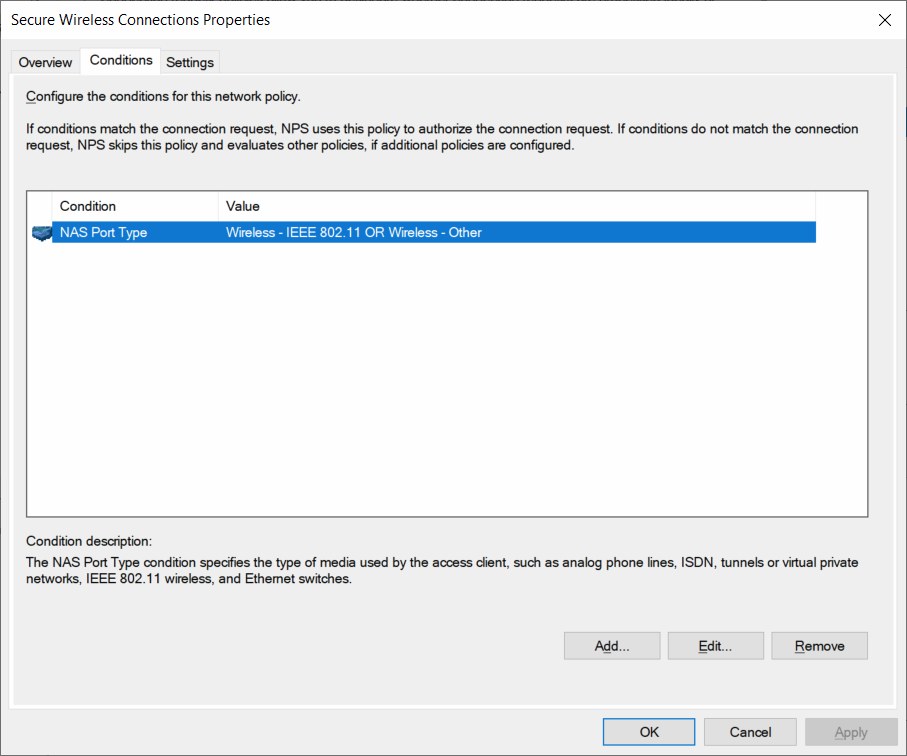
I also have a Network Policy to allow EAP-TLS and (P)EAP-MSCHAPv2:
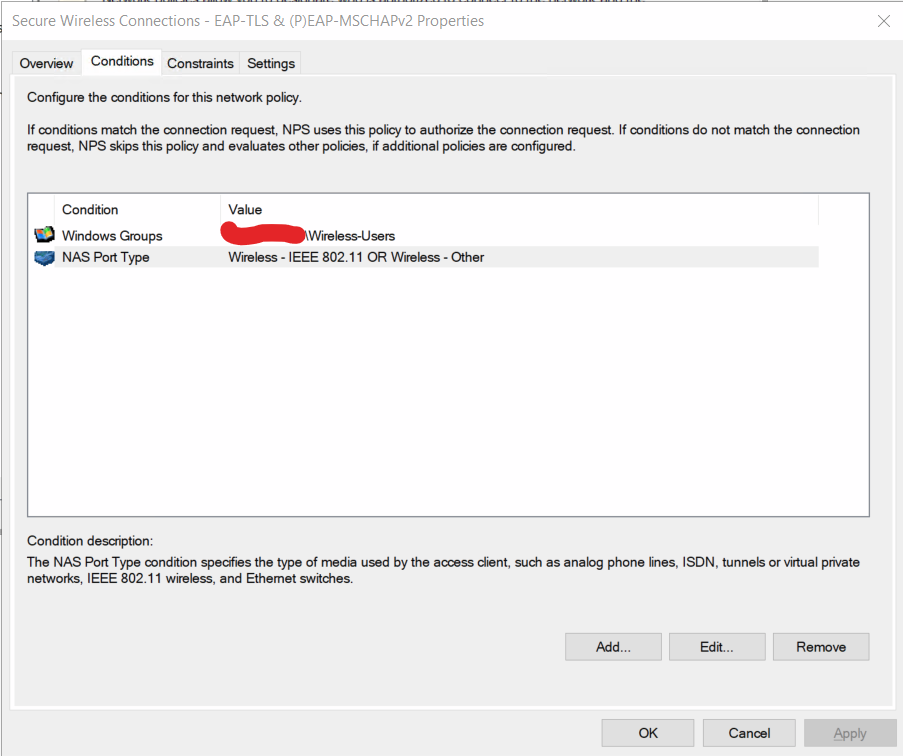
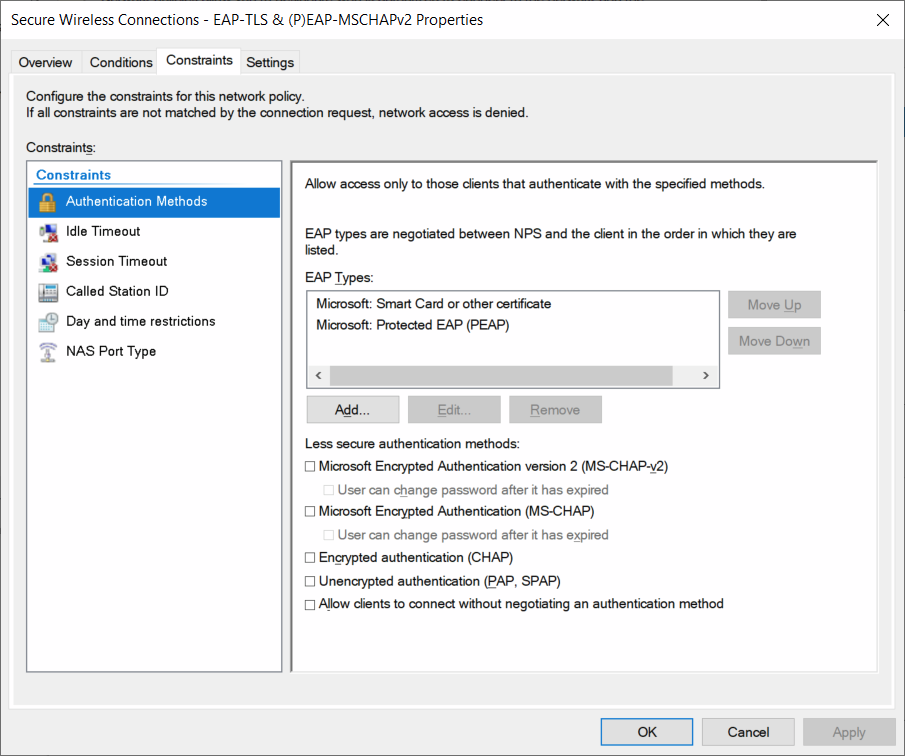
What modifications and additions do I need to make to the Connection Requets and Network policies on the NPS server to allow EAP identity privacy with (P)EAP-MSCHAPv2, whilst also still allowing EAP-TLS to work?





