Hi @Mohd Arif ,
It looks like the firewall doesn't have the ports open to allow the workstation to talk to the domain controllers. Have a look at this article which lists the ports that need to be opened.
Gary.
This browser is no longer supported.
Upgrade to Microsoft Edge to take advantage of the latest features, security updates, and technical support.
The computer was in the normal network then I moved it to DMZ network and got this login error "The trust relationship between this workstation and the primary domain failed"



Hi @Mohd Arif ,
It looks like the firewall doesn't have the ports open to allow the workstation to talk to the domain controllers. Have a look at this article which lists the ports that need to be opened.
Gary.
I was thinking the same but since I am able to rejoin the computer in the domain, I was confused.
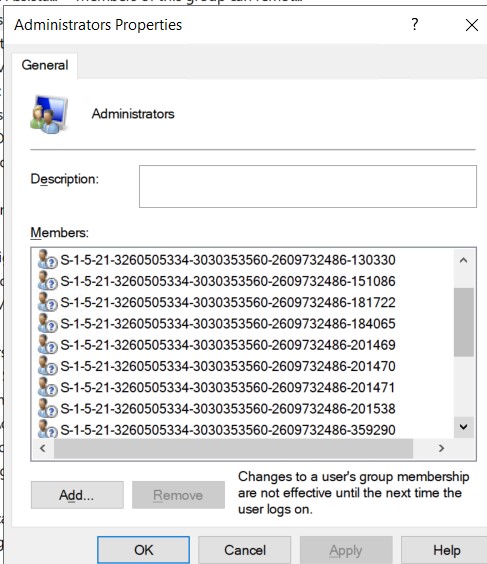
So now even firewall rules are in place as MS doc. I ran portquery application "Domain and Trusts", I see all the required ports are open except 636 is looking as filtered. but 389 is listening. But weird things is that, my DC is not able to translate my local administrator group member's name, I see only SIDs. I think something is causing communication issue between client and DC.
UDP and TCP Port 135 for domain controllers-to-domain controller and client to domain controller operations.
UDP Port 389 for LDAP to handle normal queries from client computers to the domain controllers.
TCP and UDP Port 464 for Kerberos Password Change
TCP and UDP Port 53 for DNS from client to domain controller and domain controller to domain controller.
UDP Port 88 for Kerberos authentication
TCP Port 139 and UDP 138 for File Replication Service between domain controllers.
TCP and UDP Port 445 for File Replication Service
TCP Port 3268 and 3269 for Global Catalog from client to domain controller.