
Hey @KKlouzal , did you enroll your user for a client authentication cert? WH4B requires the user to complete MFA before it will issue the user with a WHFB sign on cert.
This browser is no longer supported.
Upgrade to Microsoft Edge to take advantage of the latest features, security updates, and technical support.
ADFS has been setup on Windows Server 2019 and Automatic Device Registration has been setup in our ADFS server.
The goal is to get 100% on-prem Windows Hello For Business working using Certificate Authentication to satisfy the MFA requirement.
Clients appear to be receiving certificates from the ADFS server:
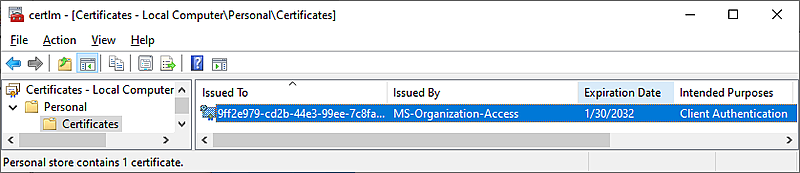
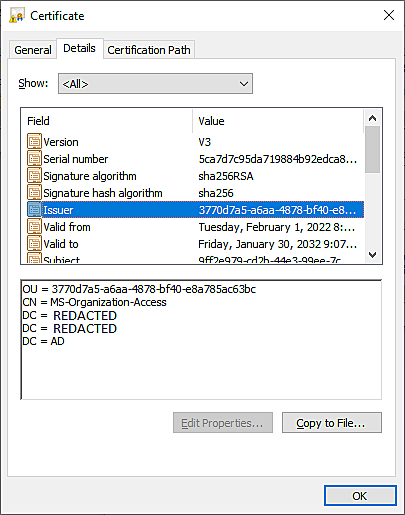
Being issued from 'MS-Organization-Access'.
Note the order of OU,CN,DC,DC,DC appears to be incorrect. Our domain is OU CN AD REDACTED REDACTED not OU CN REDACTED REDACTED AD
Nonetheless clients do not appear to trust these certificates nor does WHFB provisioning allow us to set a pin:
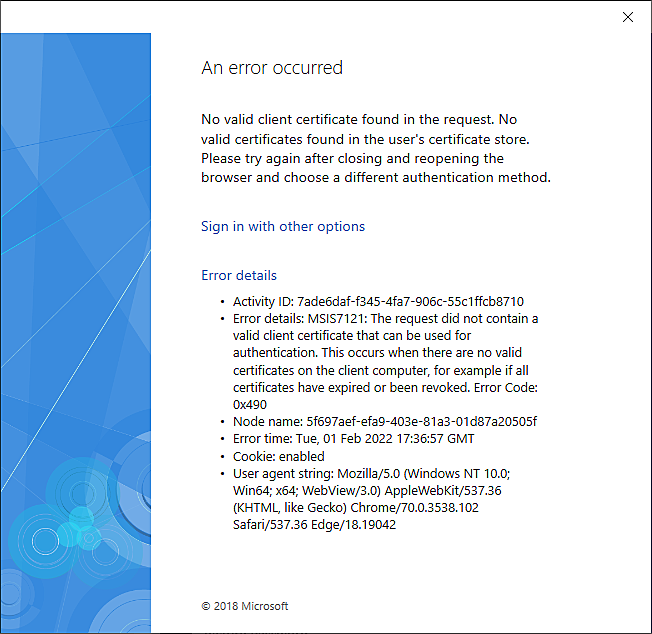
MSIS7121: The request did not contain a valid client certificate that can be used for authentication. This occurs when there are no valid certificates on the client computer, for example if all certificates have expired or been revoked. Error Code: 0x490
Looking further into this, AD FS Event Logs show two back to back errors when the clients experience this issue:
Event ID 1021:
Encountered error during OAuth token request.
Additional Data
Exception details:
Microsoft.IdentityServer.Web.Protocols.OAuth.Exceptions.OAuthInteractionRequiredException: MSIS9452: Interaction is required by the token broker to resolve the issue. The request requires fresh authentication.
at Microsoft.IdentityServer.Web.Protocols.OAuth.OAuthToken.OAuthTokenProtocolHandler.HandleJWTBearerAccessTokenRequest(OAuthJWTBearerRequestContext jwtBearerContext, SessionSecurityToken ssoSecurityToken)
at Microsoft.IdentityServer.Web.Protocols.OAuth.OAuthToken.OAuthTokenProtocolHandler.ProcessJWTBearerRequest(OAuthJWTBearerRequestContext jwtBearerContext)
Followed by Event ID 364:
Encountered error during federation passive request.
Additional Data
Protocol Name:
OAuthAuthorizationProtocolRelying Party:
urn:ms-drs:434DF4A9-3CF2-4C1D-917E-2CD2B72F515AException details:
Microsoft.IdentityServer.NoValidCertificateException: MSIS7121: The request did not contain a valid client certificate that can be used for authentication. This occurs when there are no valid certificates on the client computer, for example if all certificates have expired or been revoked.
Error Code: 0x490at Microsoft.IdentityServer.Web.Authentication.TlsClientAuthenticationHandler.ThrowCertificateErrorException(Int32 errorCode)
at Microsoft.IdentityServer.Web.Authentication.TlsClientAuthenticationHandler.ProcessIntranetRequest(ProtocolContext context, WrappedHttpListenerRequest request)
at Microsoft.IdentityServer.Web.Authentication.TlsClientAuthenticationHandler.Process(ProtocolContext context)
at Microsoft.IdentityServer.Web.Authentication.AuthenticationOptionsHandler.Process(ProtocolContext context)
at Microsoft.IdentityServer.Web.PassiveProtocolTlsClientListener.OnGetContext(WrappedHttpListenerContext context)
dsregcmd /status:
+----------------------------------------------------------------------+
| Device State |
+----------------------------------------------------------------------+AzureAdJoined : NO EnterpriseJoined : YES DomainJoined : YES DomainName : REDACTED Device Name : STATION-6.AD.REDACTED.REDACTED+----------------------------------------------------------------------+
| Device Details |
+----------------------------------------------------------------------+DeviceId : 0af67b26-f33d-4e8d-922c-e8eae002251b Thumbprint : REDACTED_86DD9DeviceCertificateValidity : [ 2022-02-03 20:20:08.000 UTC -- 2032-02-01 20:30:08.000 UTC ]
KeyContainerId : 91e9a8c3-2e20-4165-a05c-9d67627597d5
KeyProvider : Microsoft Software Key Storage Provider
TpmProtected : NO
DeviceAuthStatus : FAILED. Error:80070047+----------------------------------------------------------------------+
| Tenant Details |
+----------------------------------------------------------------------+TenantName : TenantId : 383a3889-5bc9-47a3-846c-2b70f0b7fe0e Idp : login.windows.net AuthCodeUrl : https://fs.ad.REDACTED.REDACTED/adfs/oauth2/authorize AccessTokenUrl : https://fs.ad.REDACTED.REDACTED/adfs/oauth2/token MdmUrl : MdmTouUrl : MdmComplianceUrl : SettingsUrl : JoinSrvVersion : 1.0 JoinSrvUrl : https://fs.ad.REDACTED.REDACTED/EnrollmentServer/device/ JoinSrvId : urn:ms-drs:434DF4A9-3CF2-4C1D-917E-2CD2B72F515A KeySrvVersion : 1.0 KeySrvUrl : https://fs.ad.REDACTED.REDACTED/EnrollmentServer/key/ KeySrvId : urn:ms-drs:434DF4A9-3CF2-4C1D-917E-2CD2B72F515A WebAuthNSrvVersion : 1.0 WebAuthNSrvUrl : https://fs.ad.REDACTED.REDACTED/webauthn/383a3889-5bc9-47a3-846c-2b70f0b7fe0e/ WebAuthNSrvId : urn:ms-drs:434DF4A9-3CF2-4C1D-917E-2CD2B72F515A DeviceManagementSrvVer : 1.0 DeviceManagementSrvUrl : https://fs.ad.REDACTED.REDACTED/manage/383a3889-5bc9-47a3-846c-2b70f0b7fe0e/ DeviceManagementSrvId : urn:ms-drs:434DF4A9-3CF2-4C1D-917E-2CD2B72F515A+----------------------------------------------------------------------+
| User State |
+----------------------------------------------------------------------+NgcSet : NO WorkplaceJoined : NO WamDefaultSet : YES WamDefaultAuthority : organizations WamDefaultId : https://login.microsoft.com WamDefaultGUID : {B16898C6-A148-4967-9171-64D755DA8520} (AzureAd)+----------------------------------------------------------------------+
| SSO State |
+----------------------------------------------------------------------+AzureAdPrt : NO AzureAdPrtAuthority : EnterprisePrt : YESEnterprisePrtUpdateTime : 2022-02-04 14:44:32.000 UTC
EnterprisePrtExpiryTime : 2022-02-18 14:44:32.000 UTC
EnterprisePrtAuthority : https://fs.ad.REDACTED.REDACTED:443/adfs+----------------------------------------------------------------------+
| Diagnostic Data |
+----------------------------------------------------------------------+AadRecoveryEnabled : NO Executing Account Name : REDACTED\REDACTED, REDACTED@AD.REDACTED.REDACTED KeySignTest : PASSED+----------------------------------------------------------------------+
| IE Proxy Config for Current User |
+----------------------------------------------------------------------+Auto Detect Settings : YES Auto-Configuration URL : Proxy Server List : Proxy Bypass List :+----------------------------------------------------------------------+
| WinHttp Default Proxy Config |
+----------------------------------------------------------------------+Access Type : DIRECT+----------------------------------------------------------------------+
| Ngc Prerequisite Check |
+----------------------------------------------------------------------+IsDeviceJoined : YES IsUserAzureAD : YES PolicyEnabled : YES PostLogonEnabled : YES DeviceEligible : YES SessionIsNotRemote : YES CertEnrollment : enrollment authority AdfsRefreshToken : YES AdfsRaIsReady : YES LogonCertTemplateReady : YES ( StateReady ) PreReqResult : WillProvision
I am not sure why this is happening, any help would be greatly appreciated, it's been quite the ordeal getting things setup to this point..
https://community.spiceworks.com/topic/2347157-whfb-adfs-user-device-registration-event-errors?from_forum=210
https://community.spiceworks.com/topic/2346957-2019-whfb-on-prem-certificate-trust-set-adfscertificateauthority-fails?from_forum=210


Hey @KKlouzal , did you enroll your user for a client authentication cert? WH4B requires the user to complete MFA before it will issue the user with a WHFB sign on cert.