Hi,
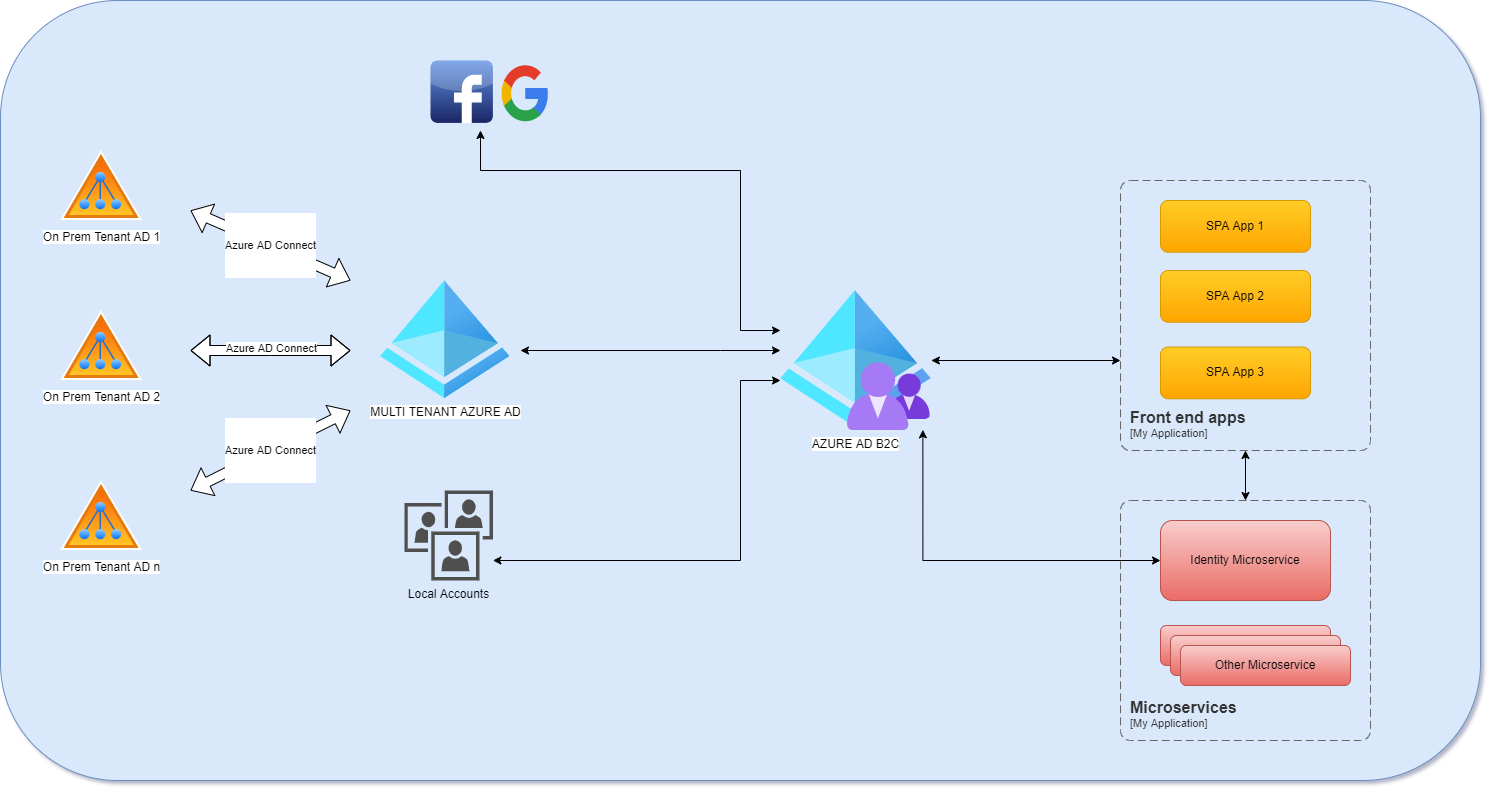
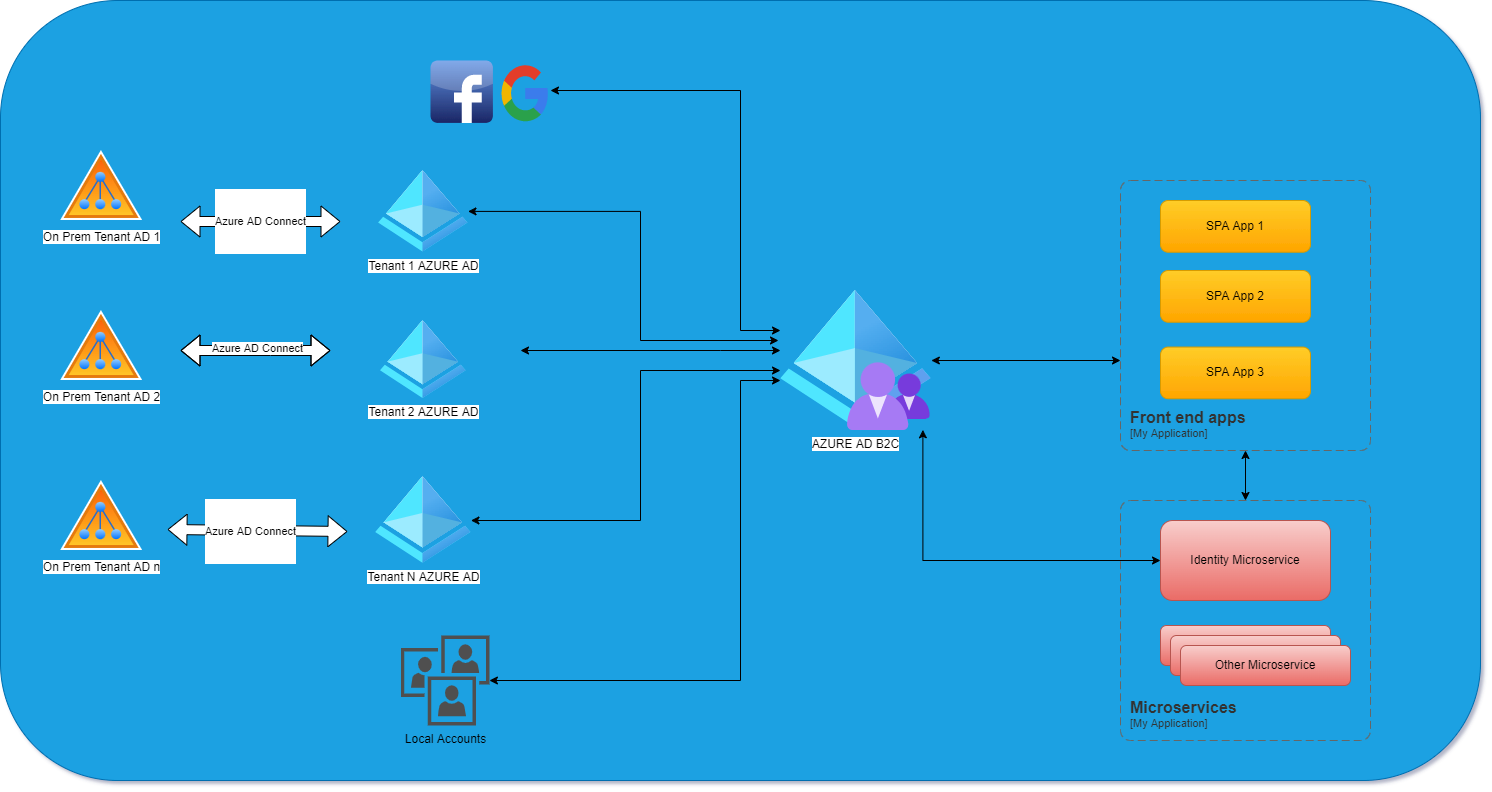
The topologies you have shared are supported however there are few things you have to be aware of. Let me discuss the requirements you have shared:
- SSO to multiple SPA applications connecting to microservices. - Yes this is possible to be achieved, with Azure AD B2C you can configure SSO between multiple SPA applications. However, you have to remember that if a single SPA application has to connect to multiple microservices (Web APIs), secured by the Azure AD B2C, you will need to use access tokens to securely access these microservices. It means that on the SPA side you will need to implement mechanism for getting access tokens using different scopes for currently authenticated user. Sometimes people register all the APIs under one application registration in the Azure AD B2C however this is not recommended practices and should be applied only when you do not have any other options to use. Please also note that Azure AD B2C does not support "on-behalf-of" flow yet so it means that you cannot call "API A" with one access token and exchange this token for the access token to call call "API B" directly.
- Support SSO login using on-prem active directory credentials(business IDs). - This should work when you have Azure Active Directory with AD Connect and its connected with your on-prem AD (as you presented in your diagram). The end result will be that user will click login button on the custom policy and then will be redirected to the Azure AD tenant federated with your Azure AD B2C tenant. From there user can use on-prem account.
- Support login using local accounts in my existing database. - This is tricky part. If you have users in your existing database it is worth to consider migration of this accounts to the Azure AD B2C. If for any reason you cannot do it, then you could implement "on the fly" credentials check in the custom policies. In such flow, once user provided username and password, you could call your "credentials check" API to see if credentials match values in the database.
- Support social login (Google and Facebook). - Yes, these identity providers are supported with the Azure AD B2C.
I hope this helped.