@Shevchenko, Vladimir
Thank you for your post!
Adding onto what @Marilee Turscak-MSFT mentioned and to hopefully point you in the right direction. You can leverage AIP-based Conditional Access policies to prevent permanent employees from opening AIP protected files from their home computers. Because multiple Conditional Access policies may apply to an individual user at any time, all policies that apply must be satisfied. For example, if one policy requires multi-factor authentication (MFA) and another requires a compliant device, you must complete MFA, and use a compliant device.
With this in mind, you can create two conditional access policies, the first policy will leverage the Filter for Devices feature which will create a rule to block any device(s) that isn't compliant with one of the supported operators and device properties. The second Conditional Access policy will filter based off the specific Named Location for example, your Corp IP address. Both of these policies together, will only allow access to compliant devices that are connect to the Corp VPN/Network.
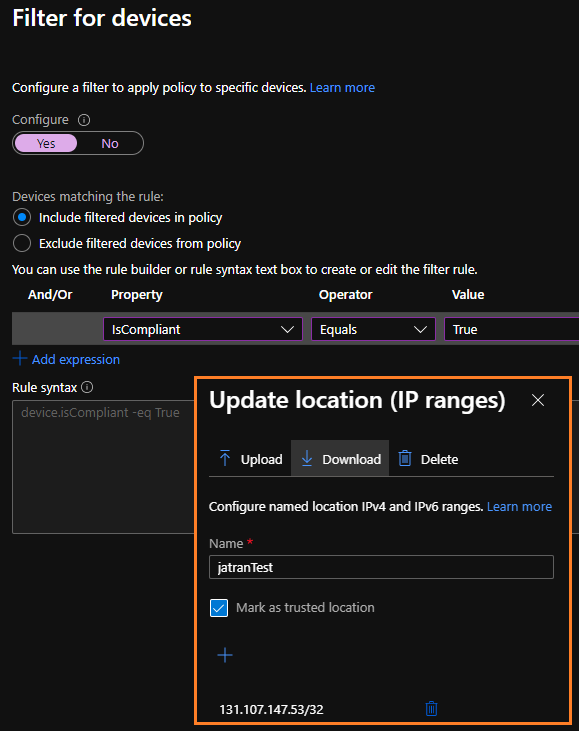
Additional Links:
Create a Conditional Access policy
Building a Conditional Access policy
Conditional Access: Block access by location
Conditional Access: Require compliant or hybrid Azure AD joined device
If you have any other questions, please let me know.
Thank you for your time and patience throughout this issue.
----------
Please remember to "Accept Answer" if any answer/reply helped, so that others in the community facing similar issues can easily find the solution.
