@Hai Dang Huy Thank you for reaching out with your question. We understand that you would like to use Microsoft Defender for Cloud to ensure your Azure Storage account is protected.
The functionality to secure Azure Storage with Microsoft Defender for Cloud is Generally Available (GA). This means you can start your implementation of it.
Please note that at this time, the implementation contains Hash reputation based Malware detection. As called out here, there is not direct in-memory scanning. This means there are a few limitations which are (source):
- Hash reputation isn't deep file inspection - Microsoft Defender for Storage uses hash reputation analysis supported by Microsoft Threat Intelligence to determine whether an uploaded file is suspicious. The threat protection tools don’t scan the uploaded files; rather they analyze the telemetry generated from the Blobs Storage and Files services. Defender for Storage then compares the hashes of newly uploaded files with hashes of known viruses, trojans, spyware, and ransomware.
- Hash reputation analysis isn't supported for all files protocols and operation types - Some, but not all, of the telemetry logs contain the hash value of the related blob or file. In some cases, the telemetry doesn't contain a hash value. As a result, some operations can't be monitored for known malware uploads. Examples of such unsupported use cases include SMB file-shares and when a blob is created using Put Block and Put Block List.
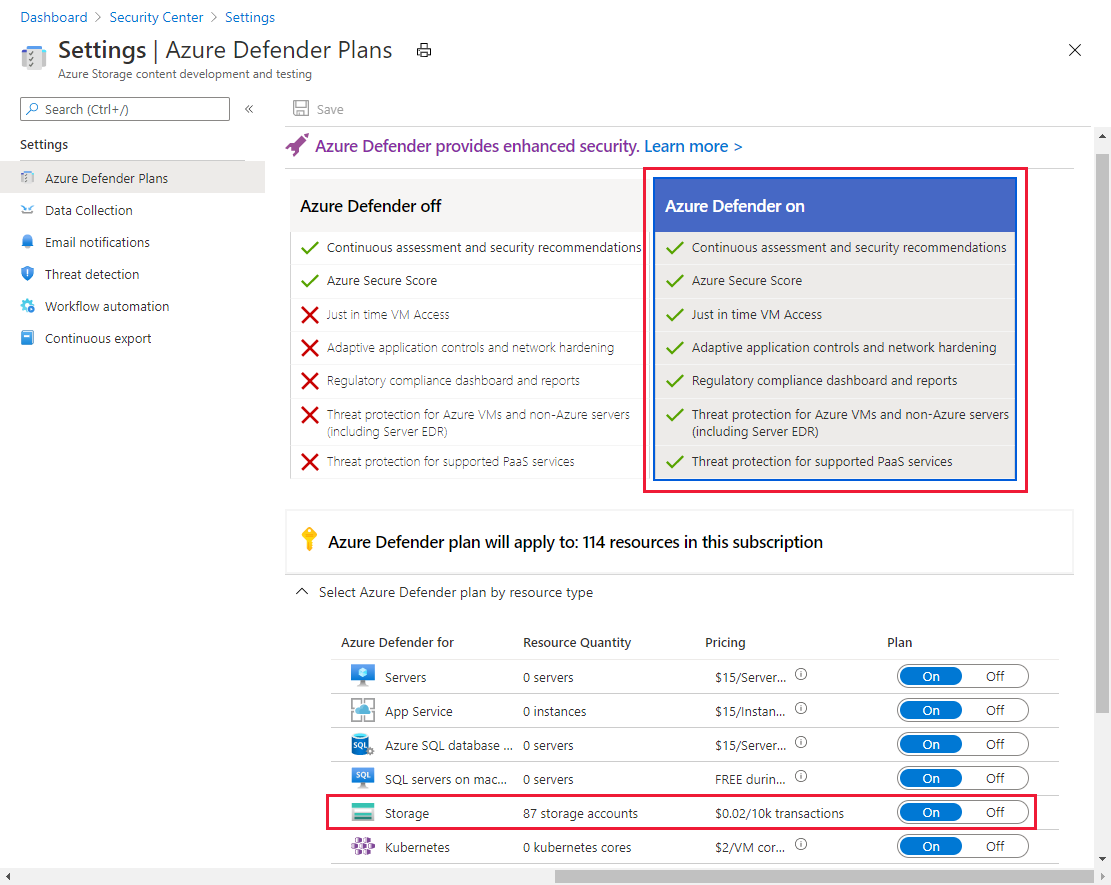
In order to enable Microsoft Defender for Cloud please follow these steps (source):
- Launch Microsoft Defender for Cloud in the Azure portal.
- From Defender for Cloud's main menu, select Environment settings.
- Select the subscription for which you want to enable or disable Microsoft Defender for Cloud.
- Select Enable all Microsoft Defender plans to enable Microsoft Defender for Cloud in the subscription.
- Under Select Microsoft Defender plans by resource type, locate the Storage row, and select Enabled in the Plan column.
- Save your changes.
Lastly, here is some additional reading on this functionality. Please let us know if you have further questions or concerns.