Recently added a public SSL Cert to an Exchange 2016 server however the server doesn't want to let go of the self assigned cert for SMTP.
Via EMC I've assigned the new cert to SMTP and IIS. Now there are checks in the boxes however the boxes are grayed out. Not a big deal since that's what I want.
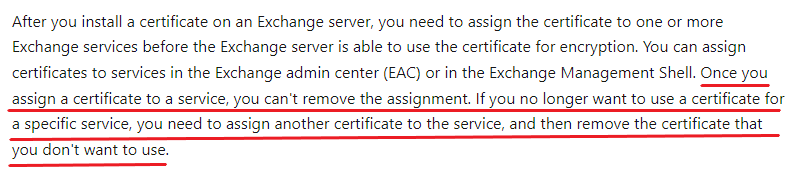
However, also in EMC the default self assigned cert has grayed out check boxes for SMTP, IMAP, POP, and IIS. I don't care about IMAP and POP but I want this removed from SMTP and IIS but I can't uncheck them in EMC.
In EMS I list the certs to get their thumbprints with "Get-ExchangeCertificate" then run the following command:
Enable-ExchangeCertificate -Services None -Thumbprint <SSL Cert Thumbprint>
It appears to execute properly, there are no errors however when I refresh or even reload EMC the self assigned cert is still bound to those services.
When I use the Digicert tool to see what's being presented IIS shows the public cert but SMTP is still using the self assigned cert.
Do I have to completely remove (delete) the self assigned cert to get this working properly or is there something else that I am missing?