When I meet this issue, solve it by:
set ValidateIssuer = false;
rebuild, redeploy, confirm it works.
set ValidateIssuer = true;
rebuild, redeploy, confirm it works.
Totally have no ideas.
This browser is no longer supported.
Upgrade to Microsoft Edge to take advantage of the latest features, security updates, and technical support.
I'm trying to implement SSO for Google and Microsoft (multi-tenant) using custom policies in an SPA application using a .NET core Web API.
I have followed the documentation and got it working for Google where users can login and access authorized endpoints. I followed the documentation for multi-tenant applications and users are able to sign in but cannot access authorized endpoints due to this issue:
Bearer error="invalid_token", error_description="The issuer '(null)' is invalid"
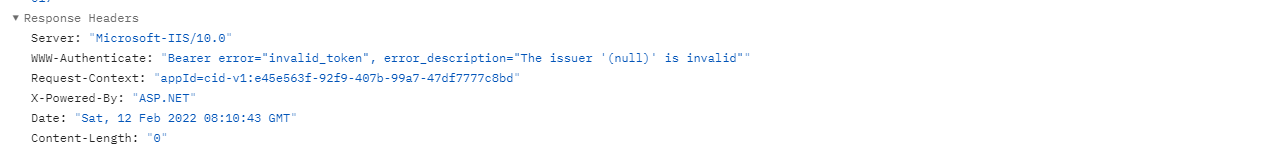
I have looked at similar threads like this and came to the conclusion that my .NET core application is the culprit as I haven't supplied any IssuerURIs.
This is the relevant part of the startup.cs config
// Adds Microsoft Identity platform (Azure AD B2C) support to protect this Api
services.AddAuthentication(JwtBearerDefaults.AuthenticationScheme)
.AddMicrosoftIdentityWebApi(options =>
{
Configuration.Bind("AzureAdB2C", options);
options.TokenValidationParameters.NameClaimType = "name";
},
options => { Configuration.Bind("AzureAdB2C", options); });
// End of the Microsoft Identity platform block
services.AddControllers();
And this is the relevant settings in appsettings.json
"AzureAdB2C": {
"Instance": "https://{mytenant}.b2clogin.com",
"ClientId": "eec3643d-xxxx-xxxx-8f5f-3f276742f101",
"Domain": "{mytenant}.onmicrosoft.com",
"SignedOutCallbackPath": "/signout/B2C_1A_SIGNUP_SIGNIN",
"SignUpSignInPolicyId": "B2C_1A_SIGNUP_SIGNIN",
},
The decoded token was:
{
"iss": "https://{mytenant}.b2clogin.com/e62fa8ea-xxxx-xxxx-8ae2-8d80a20c33f7/v2.0/",
"exp": 1644657014,
"nbf": 1644653414,
"aud": "eec3643d-xxxx-xxxx-8f5f-3f276742f101",
"email": "******@infyinnos.com",
"name": "Azam Fahmy",
"idp": "https://login.microsoftonline.com/c0ca254d-xxxx-xxxx-a85c-818538084df3/v2.0",
"tid": "c0ca254d-xxxx-xxxx-a85c-818538084df3",
"sub": "4a959031-xxxx-xxxx-88df-b61819990510",
"nonce": "d1f95a59-xxxx-xxxx-b58c-1ca643338886",
"scp": "profile.view",
"azp": "6acb4d16-xxxx-xxxx-8863-88ffb0133963",
"ver": "1.0",
"iat": 1644653414
}
In the Azure AD B2C OpenID Connect metadata document, the issuerURI was
issuer": "https://{mytenant}.b2clogin.com/e62fa8ea-xxxx-xxxx-8ae2-8d80a20c33f7/v2.0/",
"authorization_endpoint": "https://{mytenant}.b2clogin.com/{mytenant}.onmicrosoft.com/b2c_1a_signup_signin/oauth2/v2.0/authorize",
"token_endpoint": "https://{mytenant}.b2clogin.com/{mytenant}.onmicrosoft.com/b2c_1a_signup_signin/oauth2/v2.0/token",
I think I need to add the issuer URI from the OpenID Connect metadata to the .NET application but I am unfamiliar on how to do so. I searched for documentation but failed to find any.
I may be wrong and the source of the issue could be in my SPA application so here's the settings used in the MSAL.js in the SPA
REACT_APP_CLIENT_ID=6acb4d16-xxxx-xxxx-8863-88ffb0133963
REACT_APP_B2C_AUTHORITY_DOMAIN = "{mytenant}.b2clogin.com"
REACT_APP_SCOPES=https://{mytenant}.onmicrosoft.com/eec3643d-xxxx-xxxx-8f5f-3f276742f101/profile.view,
REACT_APP_B2C_SI_AUTHORITY = "https://{mytenant}.b2clogin.com/{mytenant}.onmicrosoft.com/B2C_1A_SIGNUP_SIGNIN"
I'm a newbie on .NET Core and new to Azure B2C :)
When I meet this issue, solve it by:
set ValidateIssuer = false;
rebuild, redeploy, confirm it works.
set ValidateIssuer = true;
rebuild, redeploy, confirm it works.
Totally have no ideas.
This answer has been deleted due to a violation of our Code of Conduct. The answer was manually reported or identified through automated detection before action was taken. Please refer to our Code of Conduct for more information.
Comments have been turned off. Learn more