@Taranjeet Malik Are you referring to specific blob? Are you using Azure Active Directory authentication for azure blob container?
Not sure I understand the question: Are you referring to the azure blob container: Assign Azure roles for access rights? If I am wrong, please correct me
There is a inbuilt role can been assigned to user
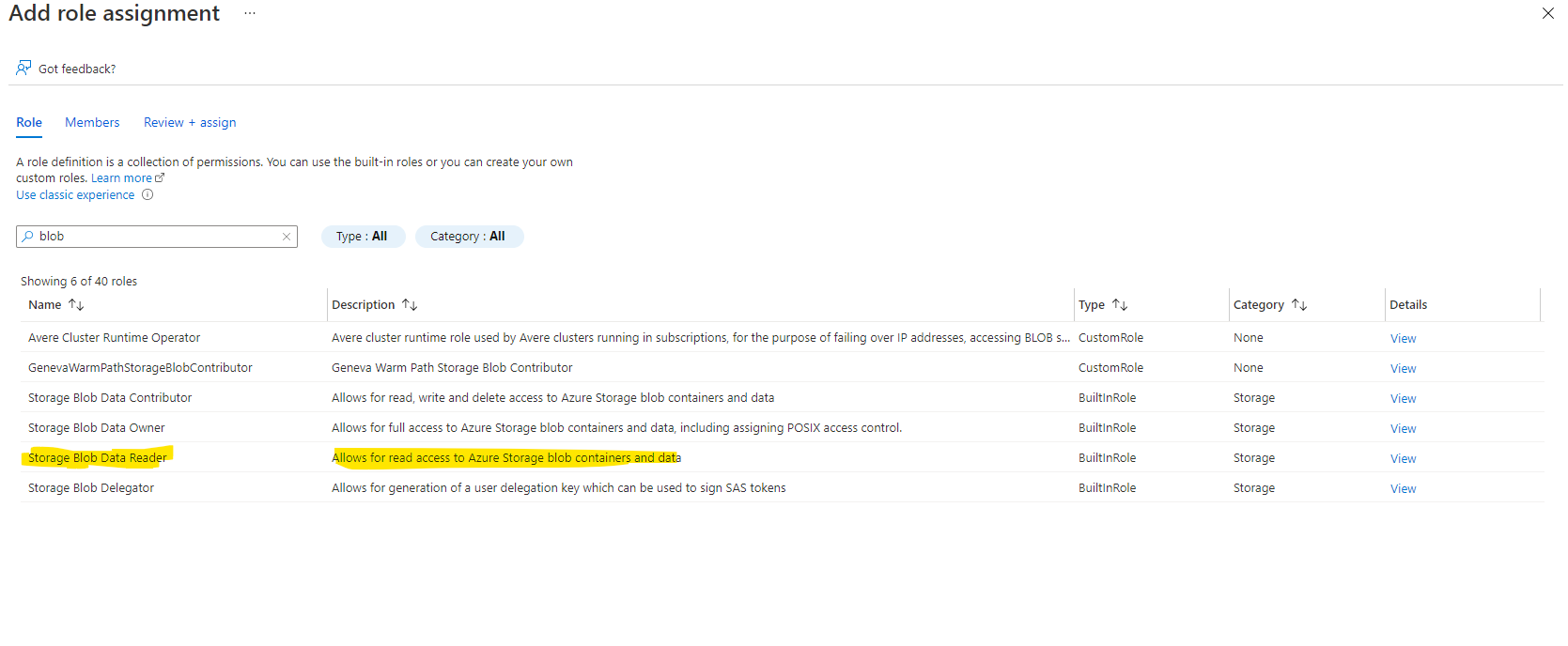
Azure Active Directory (Azure AD) authorizes access rights to secured resources through Azure role-based access control (Azure RBAC). Azure Storage defines a set of Azure built-in roles that encompass common sets of permissions used to access blob and queue data. You can also define custom roles for access to blob and queue data.|
When an Azure role is assigned to an Azure AD security principal, Azure grants access to those resources for that security principal. Access can be scoped to the level of the subscription, the resource group, the storage account, or an individual container or queue. An Azure AD security principal may be a user, a group, an application service principal, or a managed identity for Azure resources.
Azure storage supports Azure AD authentication and can be used for authentication instead of storage account name / key, SAS tokens or SAS policy. Azure Storage Explorer can also use Azure AD to authenticate to storage service. You can read more about it here: https://learn.microsoft.com/en-us/azure/storage/common/storage-auth-aad
Additional information: Prevent anonymous public read access to containers and blobs
There is also a similar thread discussion in SO forum which can give some information on your query.
Hope this helps!
Kindly let us know if the above helps or you need further assistance on this issue.
--------------------------------------------------------------------------------------------------------------
Please don’t forget to  and “up-vote” wherever the information provided helps you, this can be beneficial to other community members.
and “up-vote” wherever the information provided helps you, this can be beneficial to other community members.

 and “up-vote” wherever the information provided helps you, this can be beneficial to other community members.
and “up-vote” wherever the information provided helps you, this can be beneficial to other community members. 