I'm not sure if this is recommended in an existing CA deployment, or possibly just recreating so that HTTP is #1.
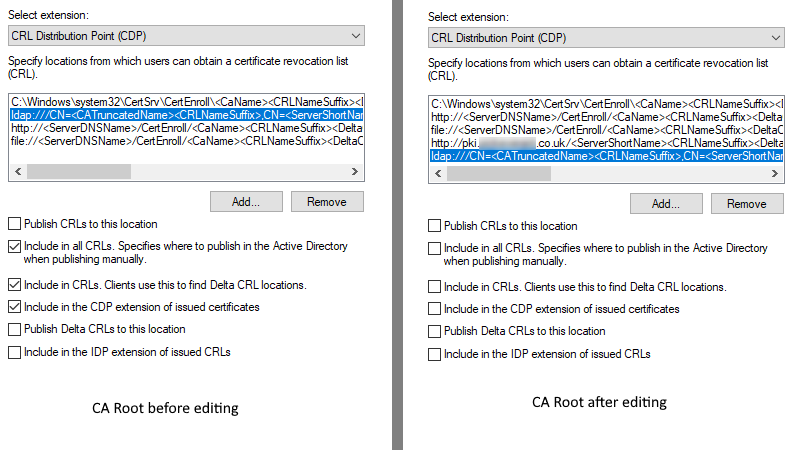
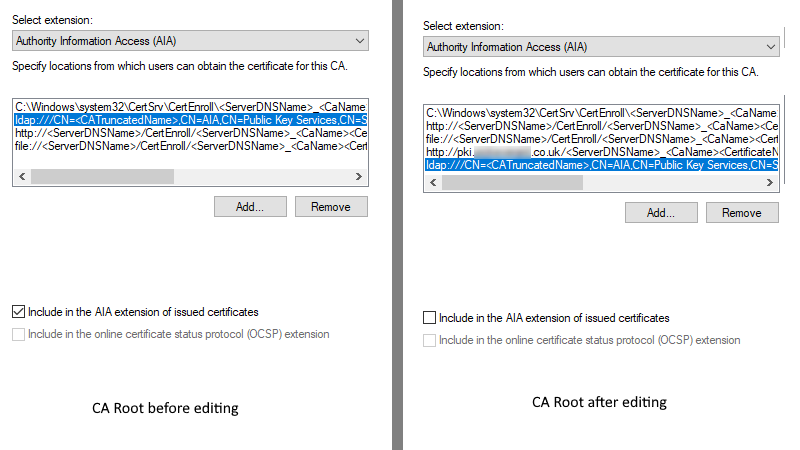
it is still my recommendation. I believe you are referring to my article: Designing CRL Distribution Points and Authority Information Access locations. If you have configured both, LDAP and HTTP, then you clear checkboxes from LDAP URL which instruct CA to include the URL in certificates and CRLs, i.e.:
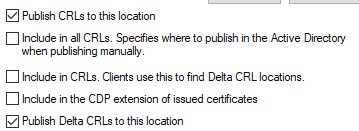
this is how checkboxes must be set for LDAP. This way CA will continue to publish CRLs there so existing certificates (that include LDAP URL) can download CRL from LDAP until they get replaced. No new certificate will contain LDAP, they will contain only HTTP.
However, it still outputs issues with our Root CA's CDP and AIA
you can solve this only be editing Root CA URLs and renewing your subordinate CA with new key pair.
PKIVIEW still shows these as LDAP
after updating URLs you have to revoke the most recent certificate based on "CA Exchange" certificate template and re-run the PKIView.msc.