
The information you need is likely in one of the other tabs of the provisioning logs - I'm not sure which it would be in.
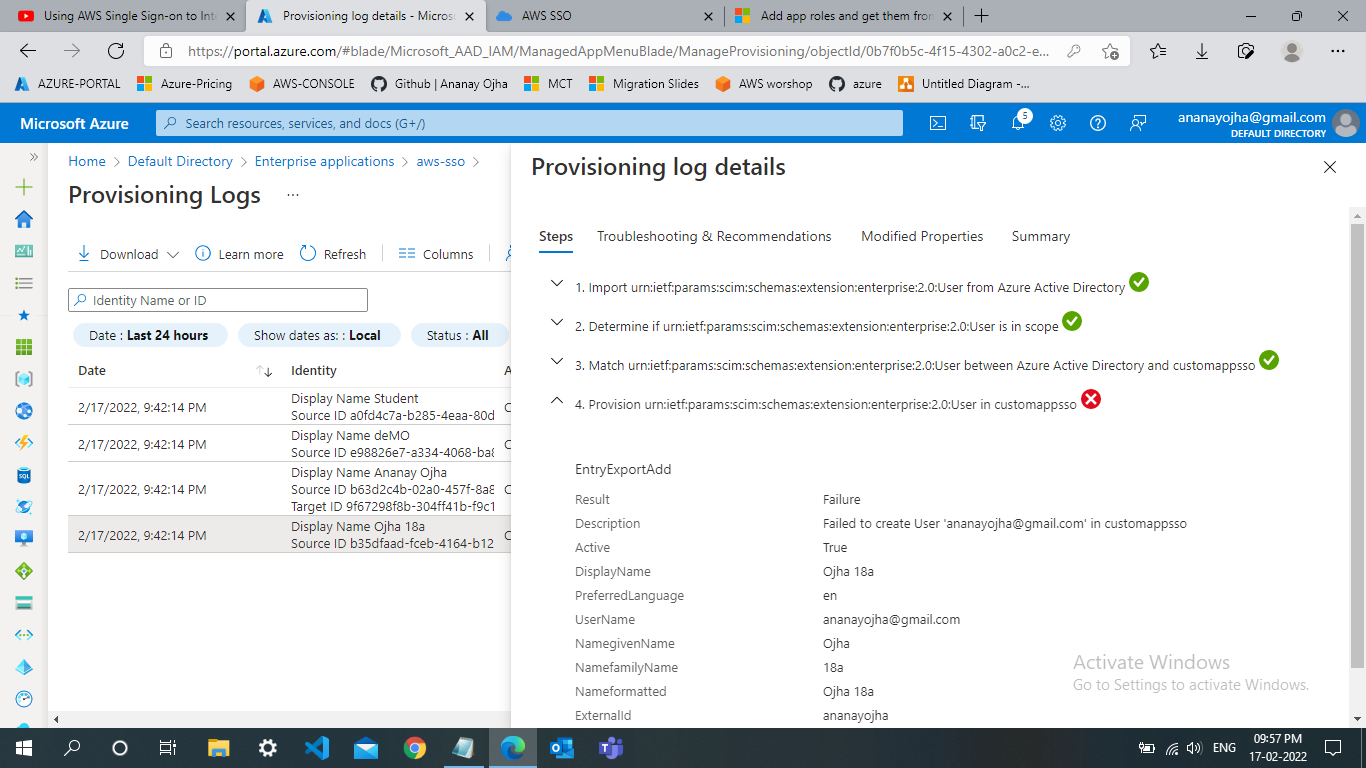
I was able to find this provisioning activity in our backend logs, however. It looks like this is failing due to an error about a duplicate resource (user) existing. That error is generated by AWS, and to understand the logic behind when and why AWS' SCIM server returns that error you would need to reach out to their support team.
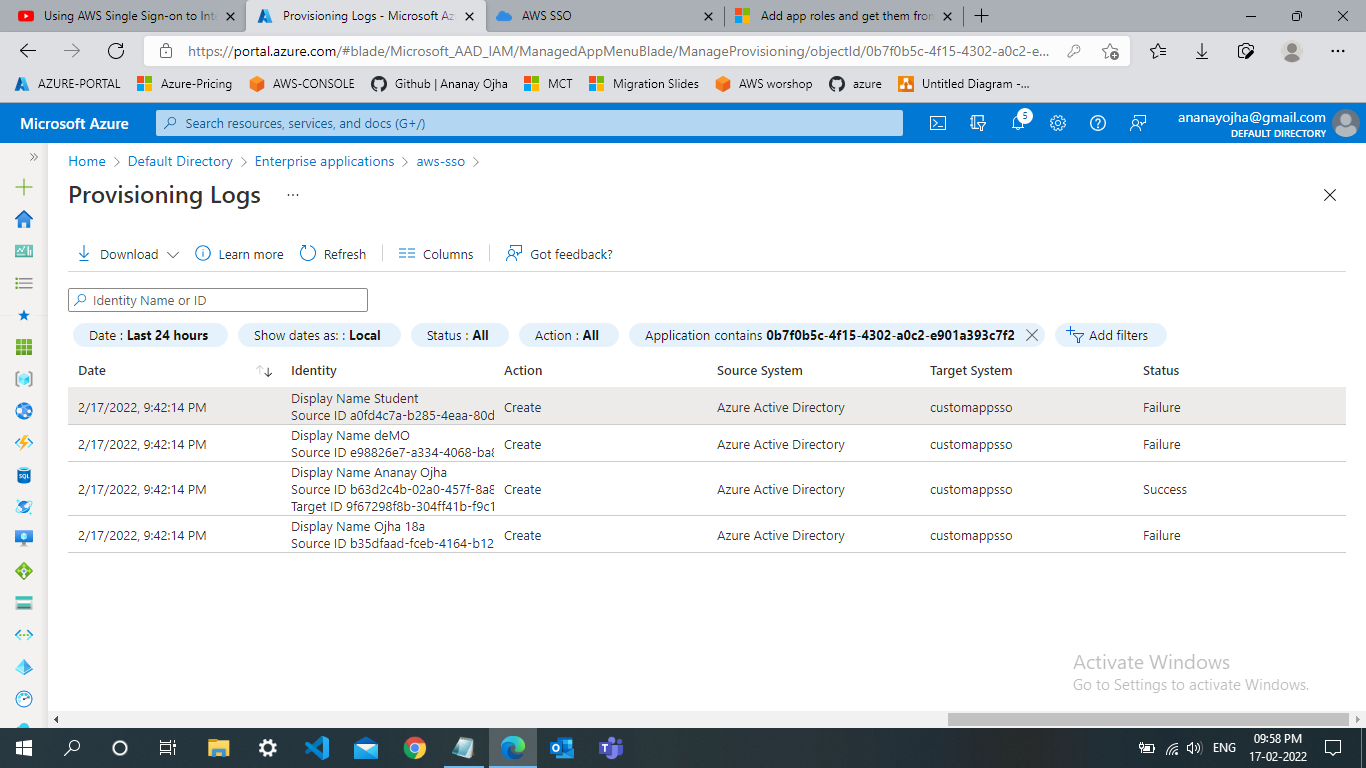
 to establish SSO with AWS using Azure AD User and Groups. For this I enabled Auto provisioning of assigned users in my enterprise app (AWS). Suprisingly out of 4 users assigned only 1 user succesfully created and I am able to SSO with that user, while other user creation failed. I have also attached the screenshots
to establish SSO with AWS using Azure AD User and Groups. For this I enabled Auto provisioning of assigned users in my enterprise app (AWS). Suprisingly out of 4 users assigned only 1 user succesfully created and I am able to SSO with that user, while other user creation failed. I have also attached the screenshots 
