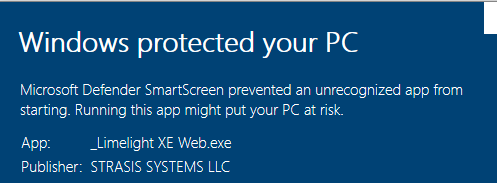
Well, not sure if it helps, however it seems the problem is with the issuer of your EV signing certificate (not with your signature or tool). There are many issues with the chain validation:
Issuer:
CN=TrustID EV Code Signing CA 3
O=IdenTrust
C=US
Name Hash(sha1): 0873edd6480ff39fb261e4b3df26f285e3b55c7d
Name Hash(md5): 750f1c6fba829034a33aa53f460018eb
Subject:
CN=STRASIS SYSTEMS LLC
OU=Strasis Systems
O=STRASIS SYSTEMS LLC
OID.2.5.4.15=Private Organization
OID.1.3.6.1.4.1.311.60.2.1.2=Florida
OID.1.3.6.1.4.1.311.60.2.1.3=US
SERIALNUMBER=L11000091926
L=Sanford
S=Florida
C=US
Name Hash(sha1): e3596c17d4931b29ba292711dfa9cc00a1e2280d
Name Hash(md5): 3bc34772b10c179dd5ab32f3a4d44efd
Cert Serial Number: 40017ed631aaaab42e6591a8e3f7d7e3
dwFlags = CA_VERIFY_FLAGS_CONSOLE_TRACE (0x20000000)
dwFlags = CA_VERIFY_FLAGS_DUMP_CHAIN (0x40000000)
ChainFlags = CERT_CHAIN_REVOCATION_CHECK_CHAIN_EXCLUDE_ROOT (0x40000000)
HCCE_LOCAL_MACHINE
CERT_CHAIN_POLICY_BASE
-------- CERT_CHAIN_CONTEXT --------
ChainContext.dwInfoStatus = CERT_TRUST_HAS_PREFERRED_ISSUER (0x100)
ChainContext.dwRevocationFreshnessTime: 13 Days, 16 Hours, 31 Minutes, 32 Seconds
SimpleChain.dwInfoStatus = CERT_TRUST_HAS_PREFERRED_ISSUER (0x100)
SimpleChain.dwRevocationFreshnessTime: 13 Days, 16 Hours, 31 Minutes, 32 Seconds
CertContext[0][0]: dwInfoStatus=102 dwErrorStatus=0
Issuer: CN=TrustID EV Code Signing CA 3, O=IdenTrust, C=US
NotBefore: 07.02.2022 23:58
NotAfter: 20.05.2022 23:58
Subject: CN=STRASIS SYSTEMS LLC, OU=Strasis Systems, O=STRASIS SYSTEMS LLC, OID.2.5.4.15=Private Organization, OID.1.3.6.1.4.1.311.60.2.1.2=Florida, OID.1.3.6.1.4.1.311.60.2.1.3=US, SERIALNUMBER=L11000091926, L=Sanford, S=Florida, C=US
Serial: 40017ed631aaaab42e6591a8e3f7d7e3
Cert: 1113f8a10f3108806bed15c44e2efba98b52f099
Element.dwInfoStatus = CERT_TRUST_HAS_KEY_MATCH_ISSUER (0x2)
Element.dwInfoStatus = CERT_TRUST_HAS_PREFERRED_ISSUER (0x100)
---------------- Certificate AIA ----------------
Wrong Issuer "Certificate (0)" Time: 0 df717eaa4ad94ec9558499602d48de5fbcf03a25
[0.0] http://validation.identrust.com/certs/trustidevcodesigning3.p7c
Verified "Certificate (1)" Time: 0 b82e9fd70413f7ecd4eddb368de44e75feeebe6c
[0.1] http://validation.identrust.com/certs/trustidevcodesigning3.p7c
---------------- Certificate CDP ----------------
Verified "Base CRL (0179)" Time: 0 3817d2fcaff1ec8932dbe48c261be7ef6f6c12a8
[0.0] http://validation.identrust.com/crl/trustidevcodesigning3.crl
---------------- Base CRL CDP ----------------
No URLs "None" Time: 0 (null)
---------------- Certificate OCSP ----------------
Verified "OCSP" Time: 0 4ed4dc27027a85ded28d0ef217730cef1f141ab5
[0.0] http://commercial.ocsp.identrust.com
--------------------------------
CRL (null):
Issuer: CN=TrustID Code Signing CA 3 OCSP Signer, O=IdenTrust, C=US
ThisUpdate: 18.02.2022 17:46
NextUpdate: 19.02.2022 17:46
CRL: d2650275ecf0e0199244f97644ccdec7176dfd08
Issuance[0] = 2.23.140.1.3
Application[0] = 1.3.6.1.5.5.7.3.3 Code Signing
CertContext[0][1]: dwInfoStatus=102 dwErrorStatus=0
Issuer: CN=IdenTrust Commercial Root CA 1, O=IdenTrust, C=US
NotBefore: 20.08.2021 22:20
NotAfter: 20.08.2029 22:20
Subject: CN=TrustID EV Code Signing CA 3, O=IdenTrust, C=US
Serial: 40017b6539031240c2d47f8e6ca4f5cc
Cert: b82e9fd70413f7ecd4eddb368de44e75feeebe6c
Element.dwInfoStatus = CERT_TRUST_HAS_KEY_MATCH_ISSUER (0x2)
Element.dwInfoStatus = CERT_TRUST_HAS_PREFERRED_ISSUER (0x100)
---------------- Certificate AIA ----------------
Wrong Issuer "Certificate (0)" Time: 0 dac9024f54d8f6df94935fb1732638ca6ad77c13
[0.0] http://validation.identrust.com/roots/commercialrootca1.p7c
Verified "Certificate (1)" Time: 0 890ff22a017207912a75c4747623dc65a1eee8d6
[0.1] http://validation.identrust.com/roots/commercialrootca1.p7c
Verified "Certificate (2)" Time: 0 df717eaa4ad94ec9558499602d48de5fbcf03a25
[0.2] http://validation.identrust.com/roots/commercialrootca1.p7c
---------------- Certificate CDP ----------------
Verified "Base CRL (7b)" Time: 0 ca5b7611b351132741d47c6fb3f5a23152f9b2d5
[0.0] http://validation.identrust.com/crl/commercialrootca1.crl
---------------- Base CRL CDP ----------------
No URLs "None" Time: 0 (null)
---------------- Certificate OCSP ----------------
Unsuccessful "OCSP" Time: 0 8c015d80b8a23f780bdd215dc842b0f5551f63bd
[0.0] http://commercial.ocsp.identrust.com
--------------------------------
CRL 7b:
Issuer: CN=IdenTrust Commercial Root CA 1, O=IdenTrust, C=US
ThisUpdate: 05.02.2022 02:02
NextUpdate: 07.03.2022 02:02
CRL: ca5b7611b351132741d47c6fb3f5a23152f9b2d5
Issuance[0] = 2.23.140.1.3
Issuance[1] = 2.16.840.1.113839.0.6.14.1
Application[0] = 1.3.6.1.5.5.7.3.3 Code Signing
CertContext[0][2]: dwInfoStatus=10c dwErrorStatus=0
Issuer: CN=IdenTrust Commercial Root CA 1, O=IdenTrust, C=US
NotBefore: 16.01.2014 20:12
NotAfter: 16.01.2034 20:12
Subject: CN=IdenTrust Commercial Root CA 1, O=IdenTrust, C=US
Serial: 0a0142800000014523c844b500000002
Cert: df717eaa4ad94ec9558499602d48de5fbcf03a25
Element.dwInfoStatus = CERT_TRUST_HAS_NAME_MATCH_ISSUER (0x4)
Element.dwInfoStatus = CERT_TRUST_IS_SELF_SIGNED (0x8)
Element.dwInfoStatus = CERT_TRUST_HAS_PREFERRED_ISSUER (0x100)
---------------- Certificate AIA ----------------
No URLs "None" Time: 0 (null)
---------------- Certificate CDP ----------------
No URLs "None" Time: 0 (null)
---------------- Certificate OCSP ----------------
No URLs "None" Time: 0 (null)
--------------------------------
Application[0] = 1.3.6.1.5.5.7.3.2 Client Authentication
Application[1] = 1.3.6.1.5.5.7.3.3 Code Signing
Application[2] = 1.3.6.1.4.1.311.10.3.12 Document Signing
Application[3] = 1.3.6.1.4.1.311.10.3.4 Encrypting File System
Application[4] = 1.3.6.1.5.5.7.3.4 Secure Email
Application[5] = 1.3.6.1.5.5.7.3.1 Server Authentication
Application[6] = 1.3.6.1.5.5.7.3.8 Time Stamping
EV[0] = 2.16.840.1.113839.0.6.9
EV[1] = 2.23.140.1.1
EV[2] = 2.16.840.1.113839.0.6.14.1
EV[3] = 2.23.140.1.3
Exclude leaf cert:
Chain: d92a62594c0fcb5cee3972b9e534dc99fd227b95
Full chain:
Chain: d77a151125d7cf937c8faf2d95b828ef72921144
EV Cert
------------------------------------
Verified Issuance Policies:
2.23.140.1.3
Verified Application Policies:
1.3.6.1.5.5.7.3.3 Code Signing
Verified Extended Validation (EV) Policies:
2.23.140.1.3
Extended Validation Certificate
Cert is an End Entity certificate
ERROR: Verifying leaf certificate revocation status returned The revocation function was unable to check revocation because the revocation server was offline. 0x80092013 (-2146885613 CRYPT_E_REVOCATION_OFFLINE)
CertUtil: The revocation function was unable to check revocation because the revocation server was offline.
You can see several "Wrong Issuer" errors and one "Unsuccessful "OCSP"". OCSP is mandatory for EV certs. You should address your concern to cert issuer.