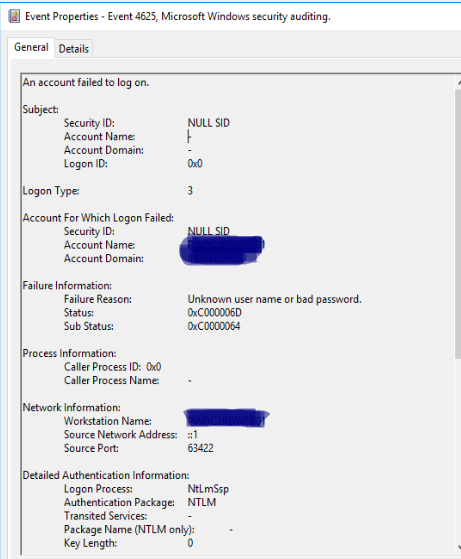
The situation where a computer account is reported as having an "unknown user name or bad password" in an Event ID 4625 log can indeed seem confusing. However, there are a few scenarios where this could happen:
Machine Account Password Mismatch: While rare, it's possible for the password of a computer account to become out of sync with the domain controller. This can happen due to various reasons like restoration of an old system state, issues with the domain controller, or network problems causing synchronization issues.
Stale Computer Account: If the computer has been offline for an extended period (beyond the domain's machine account password reset interval), its account may become stale, leading to authentication issues.
Duplicate Names: If another computer with the same name tries to join the domain, it might cause conflicts resulting in such log entries.
Malfunctioning Services or Processes: Certain services or processes that use the computer account for network operations might malfunction and send incorrect credentials.
External Interference or Attack: Although less common, an external entity might be trying to use the computer's account name to gain access, leading to failed logon attempts recorded in the logs.
To investigate this issue:
Check the Computer's Domain Membership: Verify that the computer "Dell-56" is correctly joined to the domain and there are no issues with its trust relationship with the domain.
Examine Network Issues: Look for any network connectivity problems that might be affecting the computer's ability to communicate with the domain controller.
Review System and Application Logs: Check for any errors or issues in the system and application logs around the time of the failed logon attempts that might provide more context.
Validate Computer Account Status in AD: Ensure the computer account in Active Directory is active and not disabled.
Consider Rejoining the Domain: If other methods don’t resolve the issue, removing and then rejoining the computer to the domain can sometimes fix such problems.
Security Review: If you suspect malicious activity, a thorough security review and monitoring might be necessary to rule out any external threats.
Remember, while the Event ID 4625 log provides important clues, often a broader investigation is needed to pinpoint the exact cause of such anomalies.


 ]
]