You direct yourself to the Virtual network and then click on the NIC interface for your resource.... After that you will find the following options:
This browser is no longer supported.
Upgrade to Microsoft Edge to take advantage of the latest features, security updates, and technical support.

I have 2 VNETs in Azure.
Vnet1 -10.0.0./24 -- Peered
Vnet2- 10.10.0.0/24 -- Peered.
Gateway transit is allowed on Vnet1 and use remote gateway is selected on Vnet2
Firewall Sonic wall. Current status: VPN tunnel is created(route-based) and connected from on-prem to Vnet1 and VM's on Vnet1 to On-prem
peering is completed, DBvnet used a remote virtual network, and it connects with Vnet1.
The challenge.Vnet2 cannot connect with on-prem and on-prem cannot connect with Vnet2

You direct yourself to the Virtual network and then click on the NIC interface for your resource.... After that you will find the following options:


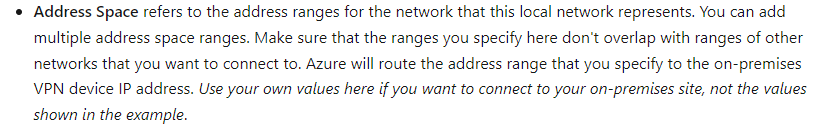
Have you advertised the DBvnet address space to your Sonicwall and have you defined the DBvnet address space in your local network gateway?
https://learn.microsoft.com/en-us/azure/vpn-gateway/tutorial-site-to-site-portal

I wonder if this topology is Hub and spoke since you mentioned that your Firewall Sonic wall is the one running IPsec protocol(Facing your on-premises FW).
If you have an overlapping allocation issue between on-premises and your Vnets, you can think of using NAT(If any of your resources hosted on those Vnets and are using an FQDN you can set up DNAT using a FQDN as destination ip.
If you want to gather more details perphas we can help...
Cheers,

Have you checked your effective routes vs UDR routes(User defined routes table)?
Resolved added address objects of both the Vnet's in-group and added the Tunnel interface on routing policies